A newly spotted banking trojan has been caught leveraging legitimate platforms like YouTube and Pastebin to store its encrypted, remote configuration and commandeer infected Windows systems, making it the latest to join the long list of malware targeting Latin America (LATAM) after Guildma, Javali, Melcoz, Grandoreiro, Mekotio, Casbaneiro, Amavaldo, Vadokrist, and Janeleiro.
The threat actor behind this malware family — dubbed "Numando" — is believed to have been active since at least 2018.
"[Numando brings] interesting new techniques to the pool of Latin American banking trojans' tricks, like using seemingly useless ZIP archives or bundling payloads with decoy BMP images," ESET researchers said in a technical analysis published on Friday. "Geographically, it focuses almost exclusively on Brazil with rare campaigns in Mexico and Spain."
Written in Delphi, the malware comes with an array of backdoor capabilities that allow it to control compromised machines, simulate mouse and keyboard actions, restart and shutdown the host, display overlay windows, capture screenshots, and terminate browser processes. Numando is "almost exclusively" propagated by spam campaigns, ensnaring several hundred victims to date, according to the cybersecurity firm's telemetry data.
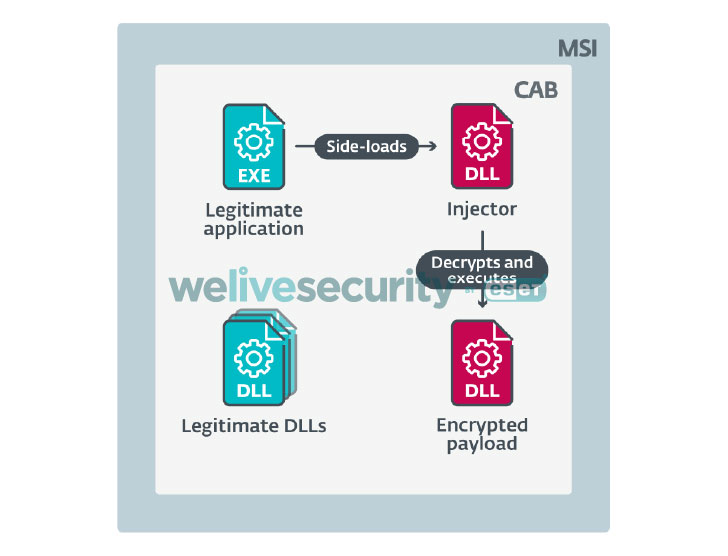
The attacks begin with a phishing message that comes embedded with a ZIP attachment containing an MSI installer, which, in turn, includes a cabinet archive with a legitimate application, an injector, and an encrypted Numando banking trojan DLL. Executing the MSI leads to the execution of the application, causing the injector module to be side-loaded and decrypt the final-stage malware payload.
In an alternate distribution chain observed by ESET, the malware takes the form of a "suspiciously large" but valid BMP image file, from which the injector extracts and executes the Numando banking trojan. What makes the campaign stand out is its use of YouTube video titles and descriptions — now taken down — to store the remote configuration such as the IP address of the command-and-control server.
"[The malware] uses fake overlay windows, contains backdoor functionality, and utilizes MSI [installer]," the researchers said. "It is the only LATAM banking trojan written in Delphi that uses a non-Delphi injector and its remote configuration format is unique, making two reliable factors when identifying this malware family."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
186
3 years ago
186 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·