BOOK THIS SPACE FOR AD
ARTICLE AD
The Ohio Lottery is sending data breach notification letters to over 538,000 individuals affected by a cyberattack that hit the organization's systems on Christmas Eve.
A filing with the Office of Maine's Attorney General revealed that the incident impacted 538,959 individuals. The attackers gained access to the affected people's names, Social Security numbers, and other personal identifiers.
"On or about December 24, 2023, the Ohio Lottery detected unauthorized access to our internal office network as a result of a cybersecurity incident that resulted in the exposure of the data we maintain. The incident did not impact the gaming network," the Ohio Lottery said.
"After an extensive forensic investigation and our manual document review, we learned on April 5, 2024 that certain files containing your personal information was subject to unauthorized access."
Ohio Lottery says that no evidence was found that the stolen information had been used for fraud. Still, it provides free credit monitoring and identity theft protection services to all potentially impacted individuals "out of an abundance of caution."
Breach claimed by DragonForce ransomware
While the Ohio Lottery didn't reveal the nature of the incident, which affected mobile and prize-cashing operations, the DragonForce ransomware gang claimed the attack days later.
The threat actors claimed they encrypted devices and stole documents belonging to both Ohio Lottery customers and employees.
An entry added to the ransomware group's dark web leak site on December 27 said the attackers stole over 3 million records. After negotiations failed, the gang leaked four .bak archives and multiple CSV files on January 22, allegedly stolen from Ohio Lottery's systems.
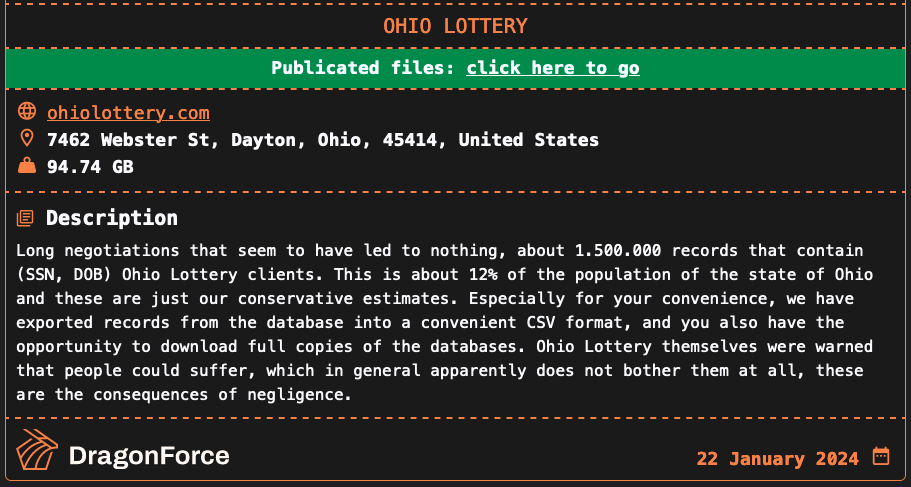 Ohio Lottery DragonForce data leak (BleepingComputer)
Ohio Lottery DragonForce data leak (BleepingComputer)DragonForce says the 94 GB of leaked data contains only 1.500.000 records with Ohio Lottery clients' names, Social Security numbers, and dates of birth.
While DragonForce ransomware is a relatively new operation that exposed its first victim in December 2023, the tactics, negotiation style, and data leak site suggest an experienced extortion group.
Since their leak site now lists almost four dozen victims and law enforcement has been disrupting many ransomware operations in recent months, it wouldn't be surprising if this was a rebrand of a previously known gang.
DragonForce ransomware also claimed a cyberattack that impacted Japanese probiotic beverage manufacturer Yakult's IT systems in Australia and New Zealand in mid-December.
Yakult disclosed the attack after the ransomware gang leaked what it claimed to be 95 GB of data stolen from the company's compromised servers.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·