BOOK THIS SPACE FOR AD
ARTICLE ADWestern Australia's auditor-general has reported 553 IT systems weaknesses to 59 state government entities, saying she was "disappointed" only 50% of them have met the benchmark in information security.
In the auditor-general's latest report [PDF], Information Systems Audit Report 2021 – State Government Entities, it was revealed that 42% of the findings made this year were previously reported to the 59 entities.
"One way entities can remain vigilant against the rapidly changing threats to information systems is by promptly addressing audit findings," state Auditor-General Caroline Spencer said. "Poor information security controls leave entity systems and information vulnerable to misuse and may impact critical services provided to the public."
36 of the 59 entities were provided with capability maturity assessments and were asked to self-assess their general computer controls.
While entities improved their controls in four out of six categories -- business continuity, IT operations, change control, and physical security -- and remained constant in management of IT risks, while going backwards in the infosec category.
"We continue to find a large number of weaknesses that could compromise the confidentiality, integrity and availability of information systems. Information security remains our biggest area of concern," the 13th report from the Office of the Auditor-General (OAG) said.
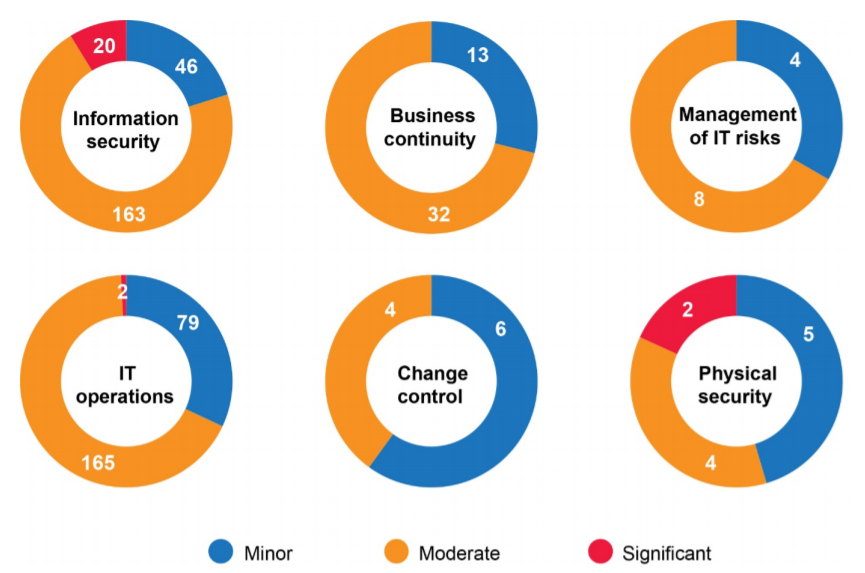
Ratings for general computer control findings in each control category
Image: OAGThe 36 assessments saw the OAG rate entities maturity level across the six categories, using a 0-5 rating system. Level 3, "defined", is the minimum standard that entities are required to meet. 50% of entities found themselves rated at level 3 or above for infosec; 62% for business continuity; 78% for the management of IT risks; 82% for IT operations; 85% for change control, and physical security was the highest scoring, with 91% of entities hitting level 3 or above.
"The number of entities who met our benchmark for information security decreased from 57% in 2018-19 to 50% in 2019-20. We continue to see little improvement in this space over the last 13 years," the report said.
Common weaknesses found included inadequate information security policies, ineffective management of technical vulnerabilities, inadequate access controls, administrator privileges not managed well, lack of data loss prevention controls, inappropriate network segregation, unauthorised device connectivity, weak database security controls, and poor cloud security controls.
Some of the recommendations made include requesting state infosec executive managers ensure patching and vulnerability management, application hardening and control, and strong passphrases/passwords and multi-factor authentication are in place, as well as implement admin account restrictions, segregate networks and prevent unauthorised devices, and secure cloud infrastructure, databases, email, and storage.
The OAG also wants cybersecurity monitoring, intrusion detection, and protection from malware to be prioritised.
Common weaknesses found under the business continuity header were a lack of business continuity planning, no backup testing procedures, inadequate IT disaster recovery plans, and a lack of disaster recovery plan testing.
Management of IT risks issues included inadequate processes to identify, assess, and treat IT risks, as well as a lack of accountability. For change control, common problems included a lack of formalised change management processes within entities, and when they do exist, they weren't being followed.
IT operation common weaknesses, the OAG said, included a failure to review policies and procedures, inadequate staff termination processes, ineffective IT asset management, a lack of supplier performance management, and an overall inadequacy in monitoring events.
Lastly, issues with physical security across the entities probed included unrestricted access to server rooms, combustible materials being stored in server rooms, and a lack of fire suppression systems in place.
Data#3, a supplier of IT to the state's whole-of-government GovNext-ICT initiative, has meanwhile taken it upon itself to help WA entities with security, launching Project Fortify.
Project Fortify, supported by the Office of Digital Government and the Department of Finance, aims to assist state entities with security operations, Essential 8 compliance, and legacy systems risk assessments.
"This is a great opportunity for agencies with limited resources to accelerate their cybersecurity maturity and improve the public sector's resilience to cyberthreats," WA chief information security officer at the Office of Digital Government Peter Bouhlas said.
Funding for the initiative comes by way of a Digital Innovation Fund, which was created under the WA Government Microsoft Licensing Agreement Data#3 picked up in 2019.
.png)
 3 years ago
258
3 years ago
258 













 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·