BOOK THIS SPACE FOR AD
ARTICLE AD
Over three million POP3 and IMAP mail servers without TLS encryption are currently exposed on the Internet and vulnerable to network sniffing attacks.
IMAP and POP3 are two methods for accessing email on mail servers. IMAP is recommended for checking emails from multiple devices, such as phones and laptops because it keeps your messages on the server and synchronizes them between devices. POP3, on the other hand, downloads emails from the server, making them accessible only from the device where they were downloaded.
The TLS secure communication protocol helps secure users' information while exchanging and accessing their emails over the Internet through client/server applications. However, when TLS encryption is not enabled, their messages' contents and credentials are sent in clear text, exposing them to eavesdropping network sniffing attacks.
As scans from the ShadowServer security threat monitoring platform Shadowserver show, around 3.3 million hosts are running POP3/IMAP services without TLS encryption enabled and expose usernames and passwords in plain text when transmitted over the Internet.
ShadowServer is now notifying mail server operators that their POP3/IMAP servers do not have TLS enabled, exposing users' unencrypted usernames and passwords to sniffing attacks.
"This means that passwords used for mail access may be intercepted by a network sniffer. Additionally, service exposure may enable password guessing attacks against the server," Shadowserver said.
"If you receive this report from us, please enable TLS support for IMAP as well as consider whether the service needs to be enabled at all or moved behind a VPN."
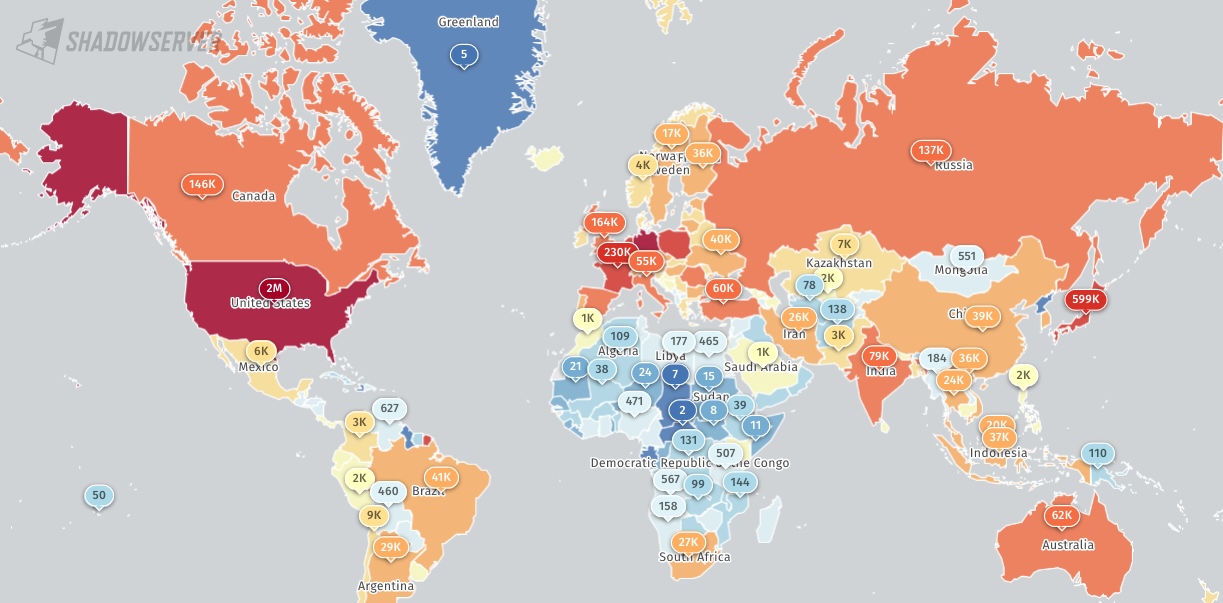 IMAP and POP3 mail servers without TLS (Shadowserver)
IMAP and POP3 mail servers without TLS (Shadowserver)The original TLS 1.0 specification and its successor, TLS 1.1, have been used for nearly two decades, with TLS 1.0 being introduced in 1999 and TLS 1.1 in 2006. After extensive discussions and the development of 28 protocol drafts, the Internet Engineering Task Force (IETF) approved TLS 1.3, the next major version of the TLS protocol, in March 2018.
In a coordinated announcement in October 2018, Microsoft, Google, Apple, and Mozilla said they would retire the insecure TLS 1.0 and TLS 1.1 protocols in the first half of 2020. Microsoft began enabling TLS 1.3 by default in the latest Windows 10 Insider builds starting in August 2020.
In January 2021, the NSA also provided guidance on identifying and replacing outdated TLS protocol versions and configurations with modern, secure alternatives.
"Obsolete configurations provide adversaries access to sensitive operational traffic using a variety of techniques, such as passive decryption and modification of traffic through man-in-the-middle attacks," the NSA said.
"Attackers can exploit outdated transport layer security (TLS) protocol configurations to gain access to sensitive data with very few skills required."
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·