BOOK THIS SPACE FOR AD
ARTICLE ADBrazilians are warned of a new Vizom malware masquerading as video conferencing and browser software.
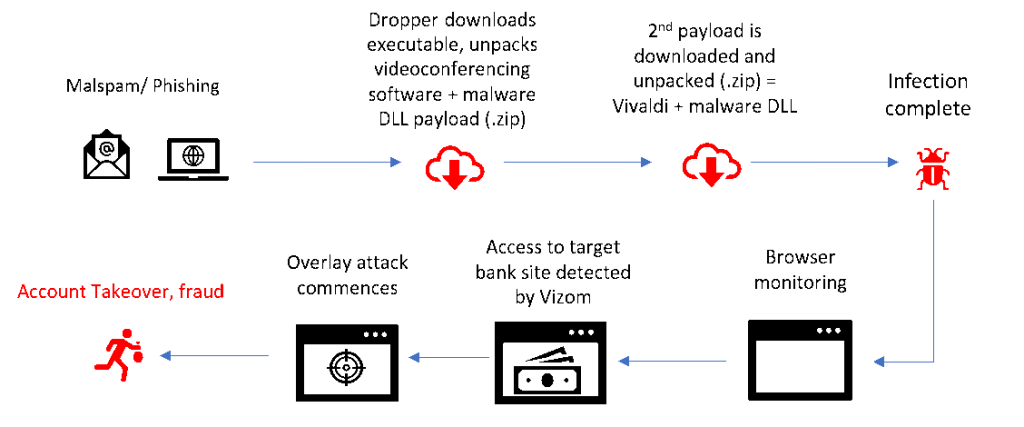
Brazilians are being warned of a new overlay malware targeting Windows users in order to siphon victims’ financial data and drain their bank accounts. Researchers say what the malware, dubbed Vizom, lacks in sophistication it makes up for in its creative abuse of the Windows ecosystem.
Trusteer, a Boston-based research arm of IBM Security, said the new code is being actively used in campaigns targeting online bank users in Brazil. Overlay malware, it said, is prevalent in Latin America and a top offender for the past decade.
Vizom is similar to other overlay malware strains in that its attack vector is via malspam and phishing campaigns delivered to potential victims’ inboxes.
“Typically delivered by spam, once Vizom is downloaded by an unwitting user, it finds its way into the [Windows] AppData directory and launches the infection process,” wrote Chen Nahman, security threat researcher at Trusteer.
He explained the malware is called “Vizom” because it leverages some legitimate computer code used by the Chromium browser Vivaldi, and binaries from a popular videoconferencing software, which researchers did not identify by name.
First, the dropper downloads an executable, then unpacks the video conferencing software and a malware DLL payload, explained Nahman in a breakdown of the malware infection chain posted Monday.
“What we found interesting about Vizom, is the way it infects and deploys on user devices. It uses ‘DLL hijacking’ to sneak into legitimate directories on Windows-based machines, masked as a legitimate, popular video conferencing software, and tricks the operating system’s inherent logic to load its malicious Dynamic Link Libraries (DLLs) before it loads the legitimate ones that belong in that address space. It uses similar tactics to operate the attack,” Nahman wrote.
Once infected, Vizom uses the above technique to piggyback on Windows in a variety of ways, such pre-loading malicious files from the various OS directories as the malware executes.
Anti-Virus Sidestep
“In this case, the malicious DLL’s name was taken from a popular videoconferencing software: ‘Cmmlib.dll.’ To make sure that the malicious code is executed from ‘Cmmlib.dll,’ the malware’s author copied the real export list of that legitimate DLL but made sure to modify it and have all the functions direct to the same address – the malicious code’s address space,” he wrote.
Similarly, to sneak past endpoint mitigations, the legitimate browser Vivaldi is dropped to the target system alongside the malware’s malicious DLLs – also used to carry out the attack, according to the report.
The malware’s persistence is maintained via modifying the “browser shortcuts so that they will all lead to its own executables and keep it running in the background no matter what browser the user attempted to run.”
Now, when a victim launches their browser, the Vizom malware is loaded and disguised as a Vivaldi browser process in order to increase its odds of not being detected.
“Since so many people have shifted to working from home, and almost everyone is using videoconferencing… Vizom uses the binaries of a popular videoconferencing software to pave its way into new devices,” he wrote.
“Vizom uses the files of yet another legitimate software, this time the Internet browser Vivaldi, which helps to disguise the malware’s activity and avoid detection from operating system controls and anti-virus software,” he added.
Post Infection Pest
Post infection, the malware monitors browser activity, communicates to the attackers’ command-and-control (C2) server, captures keystrokes and deploys its overlay screen above a bank’s website that the attackers have preselected.
“After it begins fully running on an infected device, Vizom, like other overlay malware, monitors the user’s online browsing, waiting for a match for its target list,” the researcher wrote. “Since Vizom does not hook the browser like other, more sophisticated malware typically does, it monitors activity by comparing the window title the user is accessing to key target strings the attacker is interested in. This comparison happens continually in a loop.”
Once a victim visits a desired bank’s website, the attacker is alerted in real time to the open banking session. Vizom triggers the attacker by opening a TCP socket and linking C2 server. The communication with the C2 server is a reverse shell that the infected machine uses to communicate back to the attacking server, where a listener port receives the connection.
Phase RAT
Next, the attacker leverages a remote access trojan component of it malware to launch the overlay interface and take control of the browser session. Researchers said victims are then tricked into providing personal identifiable information (PII) and financial information, which helps the attacker complete fraudulent transactions from the target’s bank account.
The actual data pilfered from targets is collected with a keylogger and then sent to the attacker’s C2. Of note, according to Nahman, is that Vizom “generates an HTML file from encrypted strings, then opens it with the ‘Vivaldi’ browser in application mode.” This, he said, is not typical of similar overlay malware and allows the application to be executed on a single web page without the typical browser’s user interface – preventing the infected victim from taking on-screen actions.
“Vizom focuses on large Brazilian banks, however, the same tactics are known to be used against users across South America and has already been observed targeting banks in Europe as well,” he warned.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·