BOOK THIS SPACE FOR AD
ARTICLE ADAkamai’s 2020 gaming report shows that cyberattacks on the video game industry skyrocketed, shooting up 340 percent in 2020.
Attacks on the gaming industry skyrocketed during the year of the pandemic, with attacks on web applications shooting up 340 percent in 2020.
According to Akamai Technologies’ latest State of the Internet and Security report, Gaming in a Pandemic (PDF), cyberattack traffic targeting the video game industry took the cake during 2020, growing at a furious rate that outpaced all other industries during the COVID-19 pandemic.
The gaming industry suffered more than 240 million web app attacks in 2020. To be precise, Akamai tracked 246,064,297 web app attacks on the gaming industry globally, representing about 4 percent of the 6.3 billion attacks the company tracked over 2020. Looking back further in time, the increase is even spikier. Since 2018, Akamai has witnessed a 415 percent increase in web app attacks on the gaming industry.
“In fact, the year-over-year change globally for web application attacks was only 2%, meaning that gaming saw more growth in attack traffic than any other industry in 2020,” according to the report.
“Criminals are relentless, and we have the data to show it,” Steve Ragan, Akamai security researcher and author of the report, was quoted as saying in a press release. “We’re observing a remarkable persistence in video game industry defenses being tested on a daily – and often hourly – basis by criminals probing for vulnerabilities through which to breach servers and expose information. We’re also seeing numerous group chats forming on popular social networks that are dedicated to sharing attack techniques and best practices.”
Credential Stuffing Also Exploded
But it wasn’t just web app attacks that rocked the gaming world. Credential-stuffing attacks also burgeoned, up 224 percent over 2019. Weirdly enough, distributed denial-of-service (DDoS) attacks dropped off nearly 20 percent over the same period.
Why the focus on gamers, those people whom the Akamai report refers to as “a focused, highly engaged, and motivated demographic”? Clearly, gamers are some of the favorite targets for “cold and ruthless” cybercrooks, as Akamai put it.
Clearly, threat actors are interested in abusing gamers and the gaming industry for a variety of reasons. One of the most notable recent incidents was the use of the Steam gaming platform to distribute malware. Last month, security analysts found malware lurking in an image file’s metadata. The technique, called steganography, isn’t new, but using it on a gaming platform certainly is.
Another reason is money. The report referred to estimates from analytics firm Newzoo that the global gaming market will hit $175 billion in 2021. Mobile game revenues are predicted to account for 52 percent of that, as gamers readily swap real cash for virtual currency to be used in-game on items such as skins and custom character enhancements.
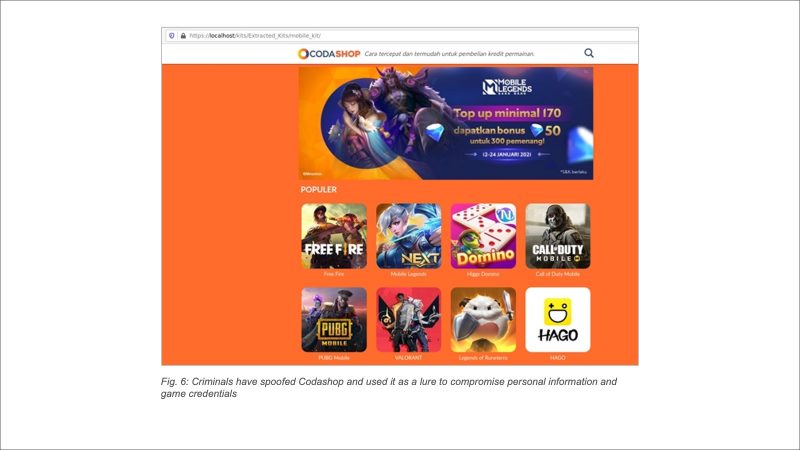
Akamai researchers came across one scam where the criminals targeted a company called Codashop, one of the largest “top-up” portals for gamers, spoofing its site and using it as a lure for grabbing gamers’ personal information and credentials.
The Codashop phishing kit collected victims’ email addresses, passwords, game login details, game usernames, geolocation data, and their player level and tier, all to be sold on criminal markets.
The Crooks Were Just as Bored as the Rest of Us
With regards to the 2020 gaming industry attack spike, Akamai researchers suggested that, rather than cybercrooks being motivated solely by profit, pandemic-era cabin fever spread in the underground just like it did in the above-ground.
It’s not always about the money, according to Alex Bakshtein, architect, edge security, at cybersecurity firm Imperva. Rather, these attacks are often meant simply to needle gamers. “In the gaming space, these attacks are rarely motivated by money,” he told Threatpost on Wednesday. “More often than not, the attackers are doing it to get under the skin of other gamers or publishers, or even worse, just for their own amusement because they can.”
That notion jibes with Akamai researchers’ thoughts: They wrote that in trying to suss out the “why’s?” behind these ferocious spikes in gaming industry attacks, we can’t ignore the fact that 2020 was “wild.”
“While we were all at home, adjusting to the ‘new normal,’ trying to balance work, school, and day-to-day existence during a pandemic, many people turned to gaming as an outlet and means of personal connection,” according to the report. “Criminals did this too. Make no mistake: While their intentions are malicious, they are still people. They talked to each other, they played games, and in some cases this social bond meant they coordinated their efforts, to varying degrees.”
Chatting About Ruining Everybody’s Gaming Fun
For example, Akamai found group chats about how to go after gamers on the popular Discord social platform – a platform that, for what it’s worth, is also popular with threat actors who use it to evade security so as to deliver info-stealers, remote-access trojans (RATs) and other malware.
Akamai researchers found Discord group chats on the techniques, tools and “best practices” of these top web app attack vectors:
SQL Injection (SQLi) Local File Inclusion (LFI) Cross-Site Scripting (XSS)“The popular discussions and tutorials centered on all-in-one tools and using services like Shodan and Censys to locate databases, unprotected assets, and more,” the report explained. “The key to many of these discussions was leveraging known tools and services as a means of obfuscation during their searching and scanning efforts.”
SQLi & LFI: The Weapons of Choice for Automated Attacks
While the web app attacks have spiked, the attackers’ favorite attack vectors have stayed steady: Akamai found that SQLi is still the number one attack vector in the gaming industry at 59 percent, followed by LFI attacks at 24 percent.
These top two attack vectors are mostly coming from attackers who’ve automated their efforts and are on the prowl for “opportunistic situations,” the report explained, “where a new app, API, or account function wasn’t properly hardened and exposed.”
Prime targets for LFI and LFI attacks are mobile and web-based games, given attackers’ likely assumption that such platforms are sitting ducks, the report said: They’re likely “not as robustly defended as their desktop and console counterparts,” the attackers’ thinking goes.
Akamai said that LFI attacks in general try to expose sensitive details within apps or services running ASP, JSP, or PHP languages. “Typically, LFI attacks lead to information disclosure, such as configuration files (that can be used to further compromise the server or accounts),” researchers observed. “In the case of the gaming industry, these attacks can expose player or account details that could be used for cheating or exploitation.”
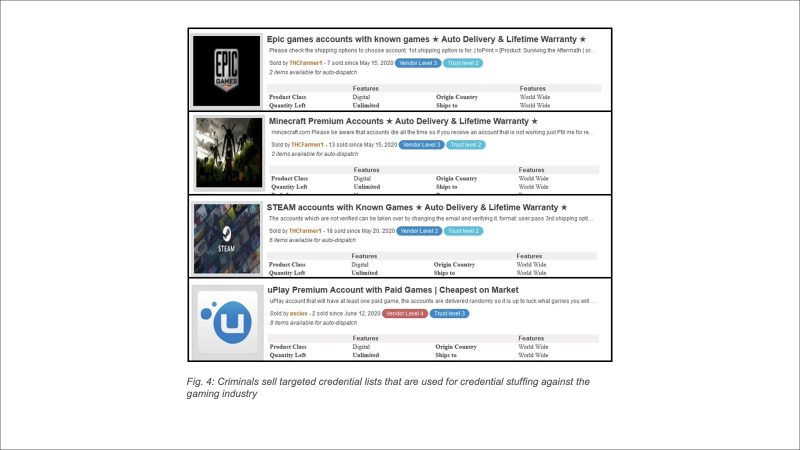
When SQLi attacks are launched on the gaming industry in particular, they could yield login credentials, personal information, or anything else stored in an exposed database, according to the report. Attackers then sell those credentials on Dark Web marketplaces, where buyers go on to use them in credential-stuffing attacks.
XSS attacks and Remote File Inclusion (RFI) attacks come in at a distant third, at 8 percent and 7 percent, respectively. “Over the past three years, this really hasn’t changed at all,” the report stated.
‘Dorks’ Are Behind Attack Spikes
Akamai graphed some noteworthy spikes in attacks: On June 1, and then again on July 11, 2020, when Akamai recorded 14.6 million attacks: A number that blew by the entire number of attacks in the previous month, in just one day. There was another peak in September, when Akamai observed more than 2 million attacks.
The company didn’t see any “real, direct connection to what was taking place in the
criminal world and their sudden explosive focus on the gaming industry,” as the report explained.
But earlier last summer, Akamai researchers did observe several tutorials passed around on
criminal forums. Those tutorials focused on automated SQLi and LFI attacks, including “dorks,” which help criminals new to this type of attack understand what to look for. Researchers noted that “many of these tutorials were pirated copies of established training, such as books and courses offered by SANS and Offensive Security, and classes taught at Udemy.”
Credential Stuffing
Credential stuffing made up about 6 percent of the 193 billion attacks Akamai tracked globally last year. The company tracked 10,851,228,730 credential stuffing attacks in the gaming industry: a 224 percent year-over-year increase. These attacks grew by 24 percent over three years, between 2018 and 2020.
Akamai attributes some of this growth to the visibility it’s gained as it’s added new customers to its global network over the past year. It blames the attacks on persistent criminals, with spikes hitting on April 11 (76 million), October (101 million) and December (157 million).
“Second only to phishing, credential stuffing is the most common type of account takeover attack, mostly due to the multiple ways a compromised account can be leveraged by criminals,” the report continued. “During the summer of 2020, bulk lists of usernames and passwords were going for as little as $5 per million records.”
In its 2020 gaming report, Akamai observed that criminals used their downtime during the COVID-19 lockdowns “to recycle old credential lists and test them against new targets,” researchers wrote. They started in early 2020, and they kept going throughout the year.
Credential stuffing is a “constant problem” because so many of us have such egregious password hygiene, the report suggested. “When gamers, or the public in general, reuse credentials across platforms and services, a successful attack against one will directly
lead to a successful attack against all the other places where that password exists,” the report continued.
It makes password managers “essential,” researchers said, given how they stop crooks when they try to “recycle” passwords. “If the gaming password is the same password used on a banking website, when a criminal compromises one account, they will compromise all of them, because that recycled password will be tested against multiple platforms and services,” such as accounts for streaming media, finance, and corporate assets, they wrote.
Nerfing Up Defenses
Imperva’s Alex Bakshtein told Threatpost that the most commonly used tool to protect from a range of web app attacks is a web application firewall (WAF).
When it comes to XSS attacks, the WAF “should use signature-based filtering to identify and block malicious requests,” he noted.
When it comes to stopping SQLi attacks, a WAF relies on a large, and constantly updated, list of meticulously crafted signatures that allow it “to surgically weed out malicious SQL queries,” he said via email. Such a list typically holds signatures to address specific attack vectors and is regularly patched to introduce blocking rules for newly discovered vulnerabilities.
He said that when it comes to RFI attacks, “input sanitization and proper file management practices are almost never sufficient on their own, even if they effectively minimize the risk of an RFI.” A WAF that monitors user inputs and filters out malicious requests using a combination of signature, behavioral and reputation-based security heuristics is “ideal,” he opined. “The WAF is deployed as a secure proxy and blocks RFI attempts at the edge of the server—before they can interact with your web application.”
Bakshtein added that modern WAFs “should be integrated with other security solutions, like advanced bot protection. From these, a WAF can receive additional information that further augments its security capabilities. For example, a web application firewall that encounters a suspicious, but not outright malicious input may cross-verify it with IP data before deciding to block the request. It blocks the input if the IP itself has a bad reputational history.”
Join Threatpost for “Tips and Tactics for Better Threat Hunting” — a LIVE event on Wed., June 30 at 2:00 PM ET in partnership with Palo Alto Networks. Learn from Palo Alto’s Unit 42 experts the best way to hunt down threats and how to use automation to help. Register HERE for free.
.png)



















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·