BOOK THIS SPACE FOR AD
ARTICLE AD
Panera Bread, an American chain of fast food restaurants, most likely paid a ransom after being hit by a ransomware attack, suggests language used an internal email sent to employees.
Last week, Panera began sending data breach notifications to employees, warning that threat actors stole personal information in a March cyberattack that included names and social security numbers.
While Panera has not publicly disclosed details about their attack, BleepingComputer first reported that Panera Bread suffered a ransomware attack that encrypted all of its virtual machines.
The attack led to a week-long, company-wide disruption that affected their website, phone systems, mobile app, point-of-sale, and internal systems.
BleepingComputer later learned that one of their storage servers was not encrypted in the attack, allowing the company to rebuild and restore servers from backups.
However, no ransomware gang ever claimed the attack or leaked stolen data, indicating that a ransom was paid.
Just as the data breach notifications were being emailed on Thursday, an alleged employee claimed on Reddit that Panera paid paid a ransom to have the hackers delete the stolen data and avoid a public leak.
"This probably will not make it far but just got out of a corporate meeting where they broke to us that all our data has been stolen since march and they paid the hackers to "not release" its employees data," reads the Reddit thread by an alleged Panera employee.
The anonymous employee also shared an internal email from Panera Senior Vice President KJ Payette, which backs up the ransom payment claim by stating that Panera obtained assurances that stolen data was deleted and would not be published.
"Please note that we obtained assurances that the information involved was deleted and will not be published. As of now, there is no indication that the information accessed has been made publicly available," reads an internal Panera email sent to employees.
During ransomware attacks, threat actors breach a company and then quietly spread throughout its network while stealing corporate data. Once they gain administrative privileges on the network, they deploy the encryptor to encrypt all devices.
The threat actors use the stolen data and encrypted files as leverage to force companies to pay a ransom, promising to deliver a decryptor and delete any data that was stolen in the attack.
It is highly unlikely that Panera could receive assurances that data was deleted and would not be published unless it came directly from the threat actors after a ransom demand was paid.
Furthermore, even if law enforcement were able to intercept the server hosting the data, there would be no way of knowing if a copy of the data was stored elsewhere by the threat actors.
Sadly, even paying a ransom does not guarantee the complete deletion of stolen data, with past incidents demonstrating that threat actors don't always keep their promise and data was sold to other threat actors, leaked on data leak sites, or used to extort the company again.
This was seen recently with the BlackCat ransomware attack on United Healthcare when the company paid a $22 million ransom demand to receive a decryptor and have stolen data deleted.
However, after BlackCat stole the ransom payment without paying the affiliate behind the attack, the affiliate said they never deleted the data and again extorted United Healthcare, stating that they would sell the data to other threat actors unless another payment was made.
To prove they still held the data, the threat actors leaked samples on another ransomware gang's data leak site, Ransom Hub. Eventually, the data leak for United Healthcare disappeared from this data leak site, indicating another ransom was likely paid.
For this reason, ransomware negotiators have told BleepingComputer in the past that companies should never pay a ransom to delete stolen data, as there is no guarantee this will be done.
BleepingComputer contacted Panera Bread to confirm if they paid the ransom but did not receive a response.
.png)
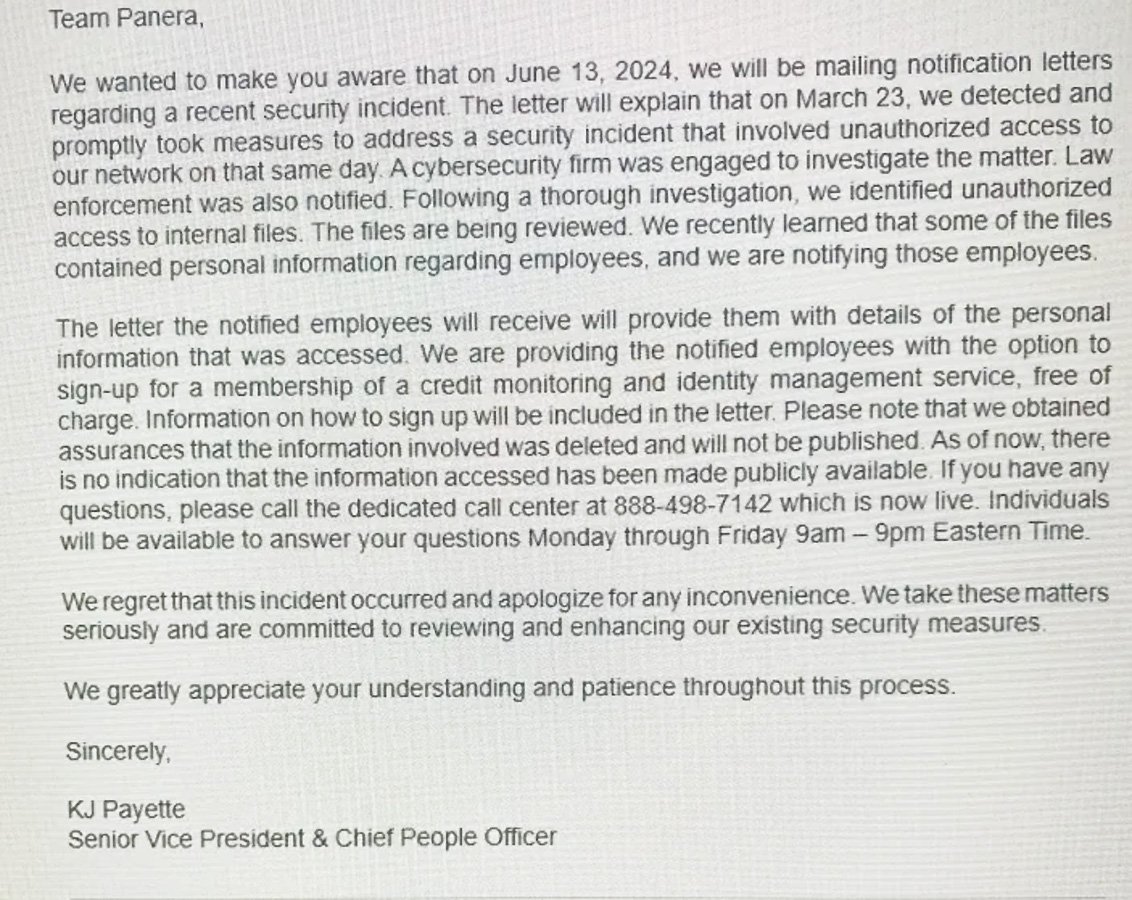 Internal Panera email sent to employees about stolen
Internal Panera email sent to employees about stolen














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·