BOOK THIS SPACE FOR AD
ARTICLE ADThis blog is about the misconfiguration issue in the ISP I was using. While working on Shodan, I discovered that ISP has left WiFi modem/router with public IP and default password. Which may lead to the hacking of multiple ISP customers by malicious attackers. I have tried contacting them via Twitter.
None of the users were exploited or troubled. Data is masked and used only for POC and reporting purposes.

There was a login page of the router/modem that will appear at 192.168.1.1 and then I didn’t know the username or password of my router’s console. So being a security engineer I entered admin/admin and I was inside the router. I logged into my router’s admin console (192.168.1.1) and went straight to the page which showed the internet connection (PPPOE). In the WAN status, it was showing the gateway address. Gateway IP address is the IP address of a through which all your internet traffic routes to the outside network. I started scanning but then I saw public IP assigned to my router/modem. I copied and opened it. And I could see the same router console.
Then I started my nmap and did a ping sweep of the whole range. I found multiple active IPs. To my surprise, all routers were publicly accessible. Then to all those routers, there was a version whose version was similar to my router and then I logged in via admin/admin. After that I used shodan and entered all those public IP assigned to router and to my surprise, I was able to find only that version of the router which was vulnerable to misconfiguration thus simplifying my attack surface I was able to see all the devices and their password, etc. It was easy to change their DNS, use password spray using the mobile and password used in the router, and so on.
I tried contacting ISP via Twitter but no response when I reported the issue to cert-in and it was fixed.
It was also possible to use someone else’s credentials to directly connect to server and get internet connection by ISP credentials stored in router connection page.
The impact of this vulnerability is high since any malicious entity can use publicly available result and exploit all the customers by login into the WiFi modem/router.
As the Public IP assigned to the modem with default credentials to login to panel, which are accessed via 192.168.1.1 Due to ZTE router, which comes with default admin/admin password. Any one can login to modem and steal data as well as poison and change the DNS to perform dns based attacks affecting all users connected via device.
Perform ping sweep -> Find routers which are up -> Login via admin/admin -> Exploit the victims.
An attacker can log in via default username password i.e. admin/admin and see the passwords and devices and make them public using Nmap.An attacker can find the SSID of the wifi modem and also get personal details of the user if used in SSID or password (like mobile number, etc).Poisoning DNS gateway to attackers DNS can cause large phishing based attacks and thus stealing banking credentials as well as social networking credentials via numerous attack.It causes a complete takeover of the victim’s WiFi modem.http://Public-IP-Address/start.ghtml
Check your local IP and modem gateway by ifconfig and route -n.Run the ping sweep command via Nmap.
3. Save the IPs and open the list of IPs. This can be automated as well.
4. Once opening the public IP, the router’s login page which is accessible appears.

5. Then try default router credentials (admin/admin).

6. Boom! We are inside someone else’s device.

7. Check the connected devices and other details for the victim.

8. Also searching these IPs in shodan.io will give you the name and model number of the router.
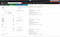
9. Search the router’s default username and password i.e. admin/admin.
10. Attacker can dump this data or post it publicly and also it can be used to sniff the traffic and even try password spraying attack.
Disallow ping sweep in the network.Change default credentials of all WiFi modem.Public IP based access should be restricted to ISP’s IP, thus not allowing any other IP to access via port 80.In the next tutorial, we will see other attacks and further automation by multiple tools and python scripts.
This issue was reported to ISP via cert-in and also ISP was contacted via Twitter but they did not respond.
Finally after sometime, I received a mail as a customer about the issue.
Anyway, the issue was fixed, which is a good.
Disclaimer: All information provided is for educational purposes only. The information related to ethical hacking and information security found on this page is not meant to be used maliciously/illegally and the author is not responsible for any misuse of the provided information.
If you are an ISP then kindly test and fix the issue before it is exploited.
.png)
 3 years ago
165
3 years ago
165 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·