BOOK THIS SPACE FOR AD
ARTICLE AD
A newly discovered phishing-as-a-service (PhaaS) operation that researchers call Morphing Meerkat, has been using the DNS over HTTPS (DoH) protocol to evade detection.
The platform also leverages DNS email exchange (MX) records to identify victims’ email providers and to dynamically serve spoofed login pages for more than 114 brands.
Morphing Meerkat has been active since at least 2020 and it was discovered by security researchers at Infoblox. Although the activity has been partially documented, it went mostly under the radar for years.
Large-scale phishing operation
Morphing Meerkat is a PhaaS platform providing a complete toolkit for launching effective, scalable, and evasive phishing attacks that require minimal technical knowledge.
It features a centralized SMTP infrastructure to distribute spam emails, with 50% of the traced emails originating from internet services provided by iomart (UK) and HostPapa (US).
The operation can impersonate more than 114 email and service providers, including Gmail, Outlook, Yahoo, DHL, Maersk, and RakBank, delivering messages with subject lines crafted to prompt urgent action like “Action Required: Account Deactivation.”
The emails are delivered multiple languages, including English, Spanish, Russian, and even Chinese, and can spoof sender names and addresses.
If the victim clicks on the malicious link in the message, they go through a chain of open redirect exploits on ad tech platforms like Google DoubleClick, frequently involving compromised WordPress sites, fake domains, and free hosting services.
Once the victim reaches the final destination, the phishing kit loads and queries the victim’s email domain’s MX record using DoH via Google or Cloudflare.
Based on the result, the kit loads a fake login page with the victim's email address filled automatically.
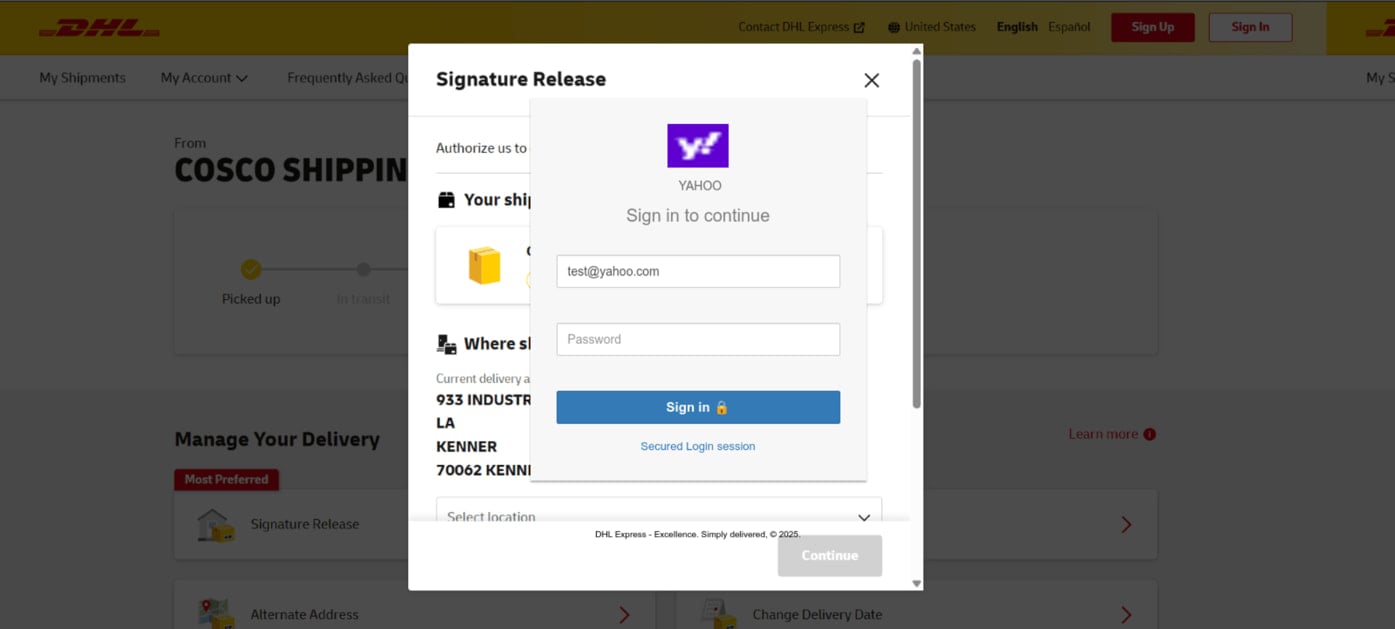 Phishing form overlayed on a fake DHL site
Phishing form overlayed on a fake DHL siteSource: Infoblox
Once the victim enters their credentials, these are exfiltrated to the threat actors via AJAX requests to external servers and PHP scripts hosted on the phishing pages. Real-time forwarding using Telegram bot webhooks is also possible.
When entering the credentials for the first time, an error message reading “Invalid Password.! Please enter email correct password” is served to get the victim to type the password again, thus making sure that the data is correct.
Once they do that, they are redirected to the legitimate authentication page to reduce suspicion.
.jpg) Overview of the Morphing Meerkat phishing attack
Overview of the Morphing Meerkat phishing attackSource: Infoblox
DoH and DNS MX
The use of DoH and DNS MX makes Morphing Meerkat stand out from similar cybercrime tools as these are advanced techniques that offer significant operational benefits.
DNS over HTTPS (DoH) is a protocol that performs DNS resolution via encrypted HTTPS requests, instead of traditional plaintext UDP-based DNS queries.
An MX (Mail Exchange) record is a type of DNS record that tells the internet which server handles email for a given domain.
When the victim clicks a link in a phishing email, the kit is loaded on their browser and makes a DNS query to Google or Cloudflare to find the MX records of their email domain.
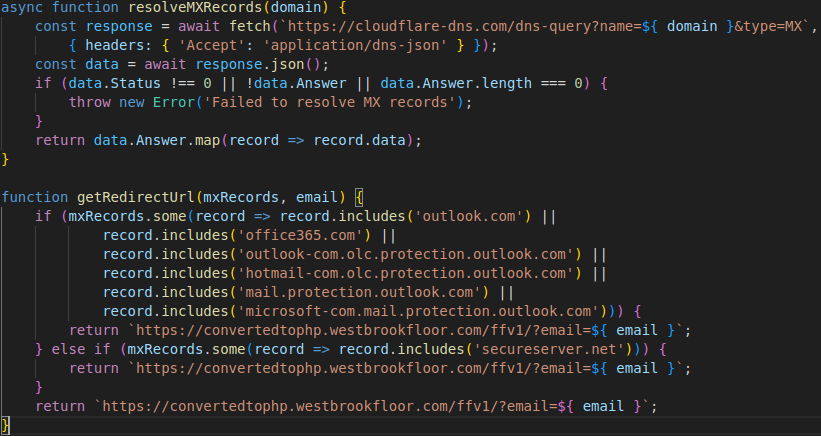 Sending a DNS query to Cloudflare to get the MX record
Sending a DNS query to Cloudflare to get the MX recordSource: Infoblox
This evades detection because the query happens client-side and the use of DoH helps bypass DNS monitoring.
With the email provider identified from the MX record, the phishing kit can then dynamically serve the matching phishing kit to the victim.
One recommended line of defense against this type of threat is tighter "DNS control so that users cannot communicate with DoH servers or blocking user access to adtech and file sharing infrastructure not critical to the business," Infoblox says.
The complete indicators of compromise (IoC) associated with Morphing Meerkat activity were made public on this GitHub repository.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·