BOOK THIS SPACE FOR AD
ARTICLE ADThe Back Story
I have been doing Bug Bounty for a couple of years now, as you may know, most of the people working in this field tend to share many similarities. The type of movies they watch, programs to work with, and even the same group of YouTubers to get information and learn more skills from.
But the thing most or just all Bug Hunters have in common are CTFs. I kind of knew what was it but never had a real interest in it just until today. Yes, today was my first time playing CTF. Somehow Youtube sent my way a video of a DEFCON conference talking about picoctf.org. At first, it wasn’t hard to find most flags until I scramble into “Transformation”
What is Capture The Flag?
Capture The Flags, or CTFs is a kind of computer security competition. Teams of competitors (or just individuals) are pitted against each other in a test of computer security skills. Very often CTFs are the beginning of one’s cybersecurity career due to their team-building nature and competitive aspect.

As we can see from the photo I was given a file to download, some python snippet code, and a hint to try to solve the flag. If you know your way around Python, this was the point to start from. Being me that’s not where I started, although I should have.
First Shot
After downloading the file to a local directory for data analysis, I went ahead and toss it into a hex editor to check for any hidden secrets.

At first glance, you can see that nothing significant was revealed. At this point, I was very disappointed thinking I hit a dead-end, that’s until I selected the result and switched the hex editor from Signed Int to UTF-8 format as shown below;


HA! I got something, these were the Chinese words for New Year’s Eve Symphony. Now what? After solving some flags involving ASCII the same day. I thought, what if this is just ASCII encoding that I need to decode instead of a real sentence with a meaning? It turned out it was just that. Using the Hint from the website, I tried to decode the ASCII, although I didn’t know it was ASCII at the time.
Using branah.com to decode 灩捯䍔䙻ㄶ形楴獟楮獴㌴摟潦弸強㕤㐸㤸扽, I had the following results below, from all these results the only one that really got my attention was the Base64.
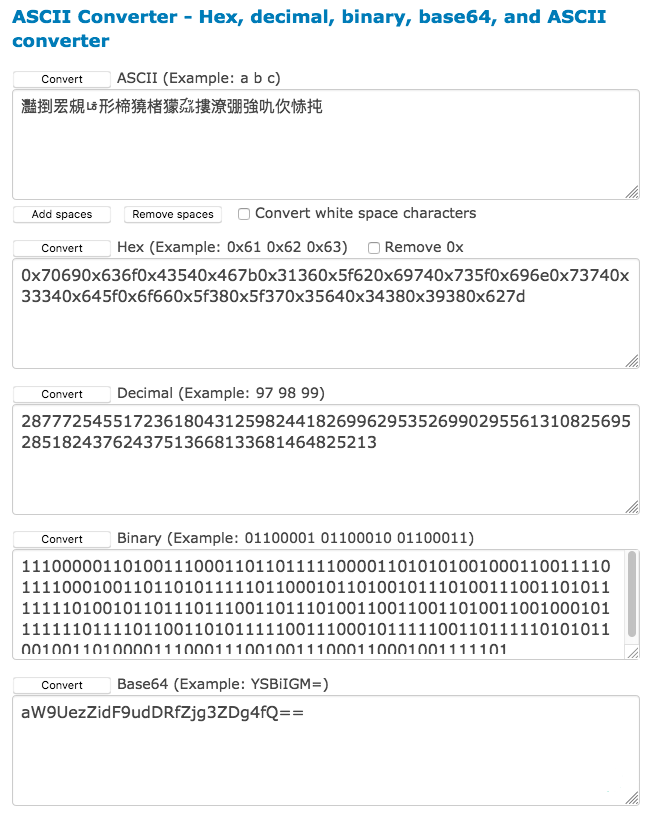
Which decoded into Text resulted in “ioT{6bt_nt4_f87d88}”. This really was something good.

Although I knew this was part of the flag phrase, it was not the answer to the flag, something was missing but I didn’t know what. The flag should be something like picoCTF{XXXX}, not IoT.
The Second Shot
Taking a closer look at the random string values from the python snippet code, I realized the script was using chr() and ord() python functions, For loop, and len. Trying to refresh my glorious python days, I went on the lookout to was what chr() and ord() mostly use for. It was at this point I found a StackOverflow.com post of a guy asking for help because he made a script that use the ASCII table to encode messages but was not decoding it back. Basically, after I went through his code, I understood that the answer to my flag was encoded using a python script with these two functions.
Somehow I needed to create a python ASCII decoder script and feed 灩捯䍔䙻ㄶ形楴獟楮獴㌴摟潦弸強㕤㐸㤸扽 to it as an input which then will decode it into plain text.
After coming up with this script and running it in the Visual Studio Code console, I got the following results;
This was the result I was looking for. Knowing every flag starts as “picoctf{xxxx}” and noticing “pi” as the first two letters in the decoded message, I finally retrieved the flag from the Chinese hidden message, or at least that’s what I thought. By taking a closer look we can see that the decoded message has some extra strings
pi0co1CT2F{3164_b5it6s_7in8st93410d_11of12_813_7145d1548169817b}18The Last Shot
After all this work all I have is;
ioT{6bt_nt4_f87d88}pi0co1CT2F{3164_b5it6s_7in8st93410d_11of12_813_7145d1548169817b}18灩捯䍔䙻ㄶ形楴獟楮獴㌴摟潦弸強㕤㐸㤸扽What do I do next?! This looks like the end. Well, I decided to try for the last time, in case it doesn’t work, I will just move on to another flag.
The most obvious step was to try picoctf{6bt_nt4_f87d88} instead of ioT{6bt_nt4_f87d88} obviously this did not work.
I moved on to deleting the 0, 1, 2, and 18 to have a more flag looking like picoCTF{3164_b5it6s_7in8st93410d_11of12_813_7145d1548169817b}, this also didn’t work, but I knew I was closed. All I needed to do was mix whatever was inside {} in the first two results into one, but how?
While meditating on how come I got this answer from my python script pi0co1CT2F{3164_b5it6s_7in8st93410d_11of12_813_7145d1548169817b}18, I realized that my code was not written efficiently, which is why it couldn’t decode the ASCII message to the fullest. I needed to find the answer by myself using logic or just second-guessing, debugging or writing up my script again was not an option for me at 3am.
The Breakthrough 👊
Still staring at the half-decoded flag and thinking about how python or just my python knowledge let me down, it was at this exact moment my inner coder kicked in. People start counting from 1, programmers know that 1 really means 0. This made me noticed that after “pi” there was a 0, two more letters after and there was 1, two more strings and there was a 2, and so on. Until reaching the number 18. This and having ROT13 in the back of my head, deleting any number after every two strings/letters finally gave me the decoded flag!
The Final Result
pi0co1CT2F{3164_b5it6s_7in8st93410d_11of12_813_7145d1548169817b}18— to
picoCTF{16_bits_inst34d_of_8_75d4898b}voilå, this was the decoded flag for this exercise.
Personal thoughts, Simple Explanation, and Suggestions
The reason behind trying CTF for the first time was to test the guy in the video theory of “How the best hacker learns their craft”. He stated that by learning small things at a time just like a puzzle at the end putting all that together could make you a good hacker.
Using this concept is how I was able to get this flag decoded. The same day I solved some flags involving ASCII, Base64, and rot13. Which we all can see was used in this task, here is how;
1) The file strings were encoded using ASCII
2) The decoded message was a Base64 format message
3) Somehow the result from my script gave me a broken look-alike result of a hidden message kind of written as ROT13
Combining all these three factors and with the help of python knowledge, I accomplished my mission. Yes, some coding knowledge is needed to hack, whoever tells you otherwise is lying to you. He was right, baby steps will soon make you run faster. When you are out there hacking stuff, always try different approaches.
.png)
 3 years ago
327
3 years ago
327 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·