BOOK THIS SPACE FOR AD
ARTICLE ADPlay Ransomware Targets Linux! New Variant Attacks ESXi with Prolific Puma Ties. Learn how to protect your organization from this evolving threat targeting virtual environments.
Trend Micro researchers have uncovered a worrying development in the ever-widening ransomware arsenal – a new Linux variant of the Play ransomware group targeting ESXi environments.
Trend Micro’s threat hunters report that this new variant of Play ransomware, aka Balloonfly and PlayCrypt, only encrypts in the VMware ESXi environments, which means the group may be expanding its attacks across the Linux platform, potentially “leading to an expanded victim pool and more successful ransom negotiations.” It aims to maximize the impact of attacks, targeting organizations with a heavy reliance on virtualized environments.
ESXi environments, used by businesses to host multiple virtual machines, critical applications, and data, can disrupt operations, encrypt backups, and reduce data recovery capabilities if compromised. By attacking ESXi hosts, the Play ransomware can potentially cripple an organization’s entire virtual infrastructure.
The group was first detected in June 2022 and is known for its double-extortion tactics, evasion techniques, and impact on Latin American organizations. As of October 2023, around 300 organizations were targeted by Play and this year it is focusing more on the US.
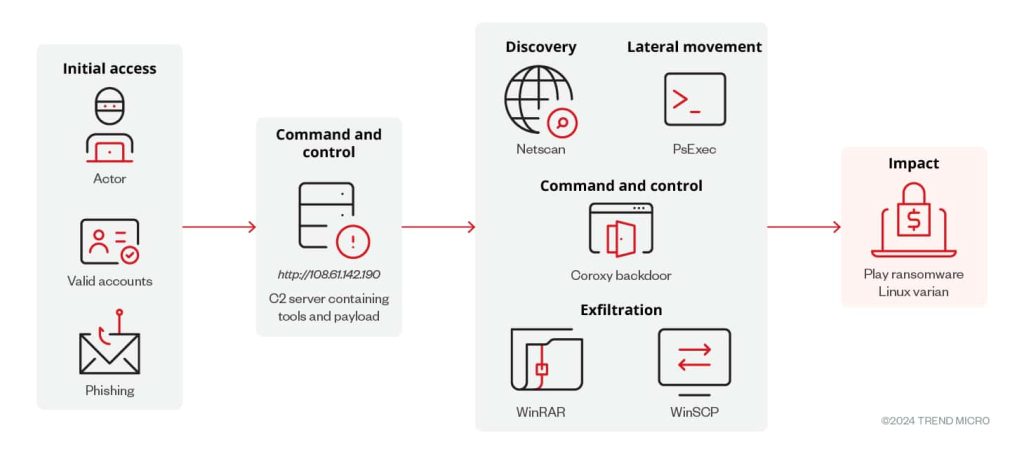
As per Trend Micro’s report, the newly discovered Linux variant exhibits behaviour consistent with Play’s previous ransomware attacks. The Linux variant is compressed in a RAR archive file hosted on an IP address containing tools used in Play’s previous attacks, including PsExec, NetScan, WinSCP, WinRAR, and the Coroxy backdoor.
Researchers believe that the Linux variant might employ similar tactics, techniques, and procedures (TTPs). The ransomware sample ensures running in an ESXi environment before encrypting virtual machine files, including VM disk, configuration, and metadata files, and dropping a ransom note in the root directory. Analysis revealed the use of a custom shell script for payload delivery and execution.
Abusing Registered Domain Generation Algorithm (RDGA)
Even more surprising is Play ransomware group uses a Registered Domain Generation Algorithm (RDGA) mechanism linked to another notorious threat actor – Prolific Puma. RDGAs are a tactic employed by malware to dynamically generate command-and-control (C2) server addresses, making them harder to detect and block. The shared use of Prolific Puma’s RDGA system raises questions about potential collaboration between the two groups.
Hackread.com warned of RDGA abuse just last week when cybersecurity researchers at Infoblox reported that an unidentified threat actor, “Revolver Rabbit,” was found using RDGA to register 500,000 .Bond TLDs (Top Level Domains).
Therefore, organizations must be vigilant against ransomware attacks, regardless of their operating system. Key steps include promptly patching and updating ESXi hosts, implementing strong access controls and segmentation, regularly backing up data, and investing in endpoint detection and response (EDR) solutions.
Jason Soroko, Senior Vice President of Product at Sectigo commented on the recent development stating, “Compromising an ESXi server can lead to widespread disruption, as a single attack can incapacitate multiple virtual machines simultaneously, affecting core business operations and services.”
“Play’s double extortion tactics, which involve encrypting and exfiltrating data, increase pressure on victims to pay ransoms. The inclusion of commonly used tools for lateral movement and persistence highlights the threat’s potency,” Jason explained.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·