BOOK THIS SPACE FOR AD
ARTICLE ADResearchers are tracking a number of open-source “protestware” projects on GitHub that have recently altered their code to display “Stand with Ukraine” messages for users, or basic facts about the carnage in Ukraine. The group also is tracking several code packages that were recently modified to erase files on computers that appear to be coming from Russian or Belarusian Internet addresses.

The upstart tracking effort is being crowdsourced via Telegram, but the output of the Russian research group is centralized in a Google Spreadsheet that is open to the public. Most of the GitHub code repositories tracked by this group include relatively harmless components that will either display a simple message in support of Ukraine, or show statistics about the war in Ukraine — such as casualty numbers — and links to more information on the Deep Web.
For example, the popular library ES5-ext hadn’t updated its code in nearly two years. But on March 7, the code project added a component “postinstall.js,” which checks to see if the user’s computer is tied to a Russian Internet address. If so, the code broadcasts a “Call for peace:”
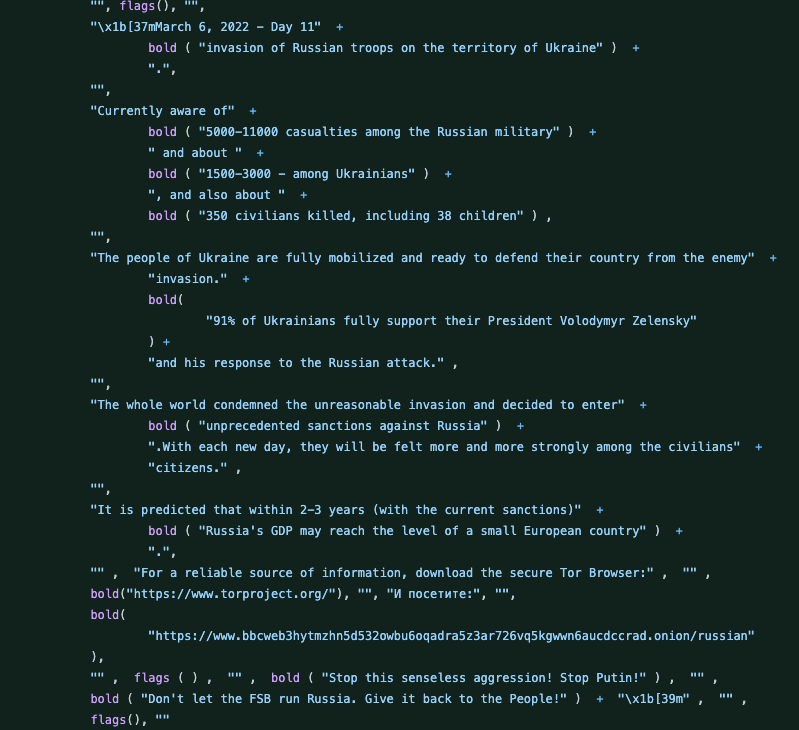
A message that appears for Russian users of the popular es5-ext code library on GitHub. The message has been Google-Translated from Russian to English.
A more concerning example can be found at the GitHub page for “vue-cli,” a popular Javascript framework for building web-based user interfaces. On March 15, users discovered a new component had been added that was designed to wipe all files from any systems visiting from a Russian or Belarusian Internet address (the malicious code has since been removed):
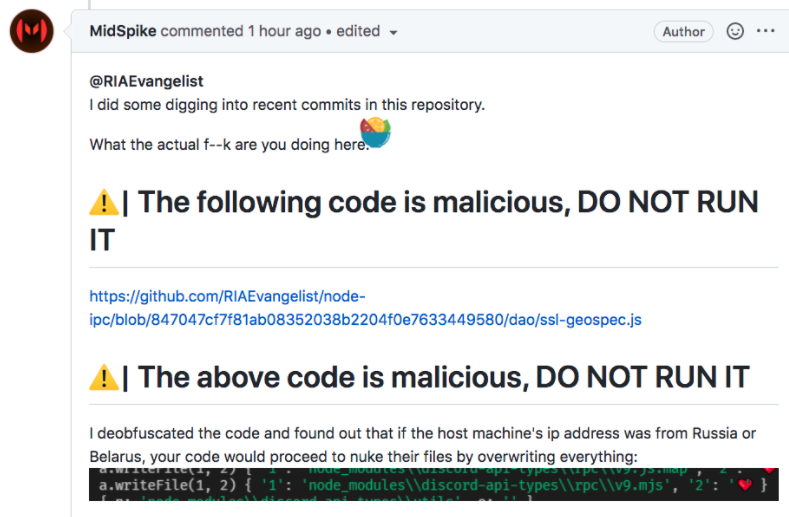
Readers complaining that an update to the popular Vue-Cli package sought to wipe files if the user was coming from a Russian IP address.
“Man, I love politics in my APIs,” GitHub user “MSchleckser” commented wryly on Mar. 15.
The crowdsourced effort also blacklisted a code library called “PeaceNotWar” maintained by GitHub user RIAEvangelist.
“This code serves as a non-destructive example of why controlling your node modules is important,” RIAEvangelist wrote. “It also serves as a non-violent protest against Russia’s aggression that threatens the world right now. This module will add a message of peace on your users’ desktops, and it will only do it if it does not already exist just to be polite. To include this module in your code, just run npm i peacenotwar in your code’s directory or module root.”
Alex Holden is a native Ukrainian who runs the Minneapolis-based cyber intelligence firm Hold Security. Holden said the real trouble starts when protestware is included in code packages that get automatically fetched by a myriad of third-party software products. Holden said some of the code projects tracked by the Russian research group are maintained by Ukrainian software developers.
“Ukrainian and sadly non-Ukrainian developers are modifying their public software to trigger malware or pro-Ukraine ads when deployed on Russian computers,” Holden said. “And we see this effort, which is the Russians trying to defend against that.”
Commenting on the malicious code added to the “Vue-cli” application, GitHub user “nm17” said a continued expansion of protestware would erode public trust in open-source software.
“The Pandora’s box is now opened, and from this point on, people who use opensource will experience xenophobia more than ever before, EVERYONE included,” NM17 wrote. “The trust factor of open source, which was based on good will of the developers is now practically gone, and now, more and more people are realizing that one day, their library/application can possibly be exploited to do/say whatever some random dev on the internet thought ‘was the right thing they to do.’ Not a single good came out of this ‘protest.'”
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·