BOOK THIS SPACE FOR AD
ARTICLE ADFeature Cops have brought down a dark-web souk that provided cyber criminals with convincing copies of trusted brands' websites for use in phishing campaigns.
The phishmonger was called LabHost and had been a port of call for phisherfolk since 2021, as it offered downloadable fake websites that masqueraded as the legit online homes of more than 170 well-known organizations – including banks and major retailers.
It's believed tens of thousands of victims in the UK were duped by these fake sites, many handing over their login details and other information under the mistaken impression they were using brands’ real websites. This info was used to steal money or was sold to other fraudsters. A lot of LabHost's subscribers were students in their late teens or 20s looking to make a fast buck, police said.
Arrests
The phishing bazaar had many of its domains seized and shut down on Wednesday in an international operation led by London's Metropolitan Police Service (MPS) in the UK.
The action, which involved authorities in 17 countries, has been ongoing since June 2022, and has led to at least 35 arrests – 25 in the UK and ten outside of Blighty – with all of the suspects collared between Sunday and Wednesday this week. More are expected to be detained, we're told, following the police's infiltration and seizure of the LabHost network.
Police told us one of those arrested in the UK is suspected of leading LabHost's British arm, which would mean they'd allegedly be responsible for much of the technical infrastructure that supported its operations.
The others are suspected of other functions, either through the alleged running of LabHost or through supposed affiliation with its alleged money-laundering processes. None of them can be named at this stage for legal reasons.
Oliver Richter, detective inspector at the MPS Cyber Crime Unit, who briefed The Register earlier this week, explained that the disruption operation was a spin-off from a 2022 campaign code-named “Elaborate” that brought down phone-spoofing service iSpoof.
Gone for good – hopefully
Will LabHost stay offline following this latest action, or will it bounce back like LockBit seemingly did after the National Crime Agency – the UK's FBI – and its partners dramatically attempted to dismantle the crew earlier this year?
Richter told us he believed it would be tough for the phishing emporium to return.
That said, he conceded outfits like LabHost will always have a customer base and will likely return in some guise. The ultimate goal here – as with the LockBit and ALPHV/BlackCat takedowns – will be to scare off criminal users of these sites by convincing them they will eventually be caught.
"These as-a-service platforms put the user at a huge risk because their data, as a criminal, is being stored somewhere," DI Richter warned.
It doesn't matter where you base your server infrastructure, where your admins are, where your domain names are, we will use all the tactics available to us to disrupt what you're doing
"They're not in control of it. And if ultimately those enablers are not as tech-savvy as they think they are, or they're making mistakes, which obviously we all do, then law enforcement certainly has an appetite [to disrupt them] now, not just in the UK," Richter added.
"People have felt that you're more likely in the UK to be a victim of fraud now than any other crime type, and we maybe don't shout as much about the work that we're doing online in that space. This is us saying: both The Met, and all our partners in the UK and internationally, have an appetite.
"It doesn't matter where you base your server infrastructure, where your admins are, where your domain names are, we will use all the tactics available to us to disrupt what you're doing."
The Met also hopes its actions will reassure victims, if not the public, that something is being done to tackle this kind of cybercrime.
It's believed miscreants using services like LabHost to commit crimes are often young, possibly attending university, and under the impression that this is a way to make a bit of quick cash before they enter the real world of work. Sting operations of this sort are trying to dispel such notions.
Asked about how the authorities infiltrated and seized control of LabHost's infrastructure, Richter didn't give up too many details. The Met would presumably like to reuse its tactics in future ops. All we got out of him was that they used "a variety of techniques."
Inside the lab
According to cybersecurity software vendor Fortra, whose researchers previously looked into LabHost, the crime souk spun up in late 2021 and bore a resemblance to an entity named Frappo which launched a month earlier and offered a similar service.
Richter told us LabHost, at its peak, offered phishing kits for about 170 organizations, 47 of which had a UK focus. These kits were available to paying subscribers who, according to Fortra, paid around $300 (£240) a month for platform access. Within five minutes of payment using cryptocurrency, criminals could access a deep catalog of phishing templates.
Fortra believes LabHost offered different subscription packages. One offered only North America sites, while an international package allowed access to sites mimicking global brands such as Spotify and DHL.
"LabHost's standard membership limits the threat actor to only Canadian brands and three concurrently active phishing pages," Team Fortra revealed. "Premium membership grants phishers access to kits targeting US banks and increases the concurrent page count to 20 active phish."
Kits would offer spoofed website templates that could be used to harvest personal data, financial information, and more from victims.
Crooks hook hundreds of exec accounts after phishing in Azure C-suite pond As if working at Helldesk weren't bad enough, IT helpers now targeted by cybercrims Russia's Cozy Bear caught phishing German politicos with phony dinner invites Fire in the Cisco! Networking giant's Duo MFA message logs stolen in phish attackThe most sophisticated of LabHost’s offerings was “LabRat,” a tool that allowed criminals to extract specific details from victims in real time. A victim would be fooled into using a phishing site and entering their credentials; the crooks would then use LabRat to immediately prompt the user for more information – such as one-time authentication codes or personal details to steal.
It appears LabRat could act as a man-in-the-middle proxy, logging the visitor into the real site so that they could see real information and results, all while the tool is stealing their data and prompting them for more. Richter described it as a "really slick" platform.
"Instead of just using it passively, setting up the service and coming back in a couple of days to see what data your victims have put in and then selling it on, there was an active approach you could take," he explained.
"It would notify you that one person has just logged onto the site and from there you could then guide them through that victim journey.
Richter said LabRat meant victims could visit their actual banks, but “every time it's loading or the next page is coming up, you can be sat there on LabHost saying 'I now want an OTP' or 'I now want your mother's maiden name', etc. You could really guide them through that process."
Popularity
LabHost had about 2,000 paying customers by the time the authorities took it down, and won over $1 million in subscription revenue – all generated from criminality. The number of account signups was much higher, though many never actually purchased a subscription. They are thought to have just signed up to see what it was all about.
Richter said more than 40,000 phishing sites were facilitated by LabHost's tools, and the MPS has endeavored to seize as many of these as possible. Each seized site will display one of the usual law enforcement splash pages, clearly communicating that the site has been nabbed.
In working to take these sites down, authorities have collected logs that reveal around a million interactions with victims of sites created by LabHost.
Of the million, around 82,000 were related to UK victims – which authorities have narrowed down to what they believe to be just under 70,000 actual individual victims.
Fortra observed that the crime bazaar's popularity seemed to increase notably toward the start of 2023, when it released phishing kits to target Canadian banks.
Although LabHost suffered a serious outage in October 2023 – which meant no new users could purchase subscriptions – the outfit recovered fairly quickly in December of the same year and returned to previous levels of activity. In real terms that means it was supporting a few hundred phishing attacks per month.
We asked Richter about that outage in October and whether it was in any way linked to the authorities' efforts to ultimately bring it down. He said his team was aware of the incident “but that's not something that we're looking to have any claims as being responsible for."
"We certainly know that they had that outage and that problem,” he added.
As part of Wednesday's takedown, authorities are looking to cause a similar stir as the National Crime Agency did when it tackled LockBit, seizing its infrastructure and communicating to its members directly using its own tools.
Phish, wrapped
The disruption efforts were ongoing at the time of writing on Wednesday afternoon, and include contacting many of LabHost's subscribers and letting them know their information is now in the hands of global police.
The Met has control of LabHost's infrastructure, including its official Telegram channel, where it has already posted a message to its circa-6,200 followers dismissing rumors of a takedown.
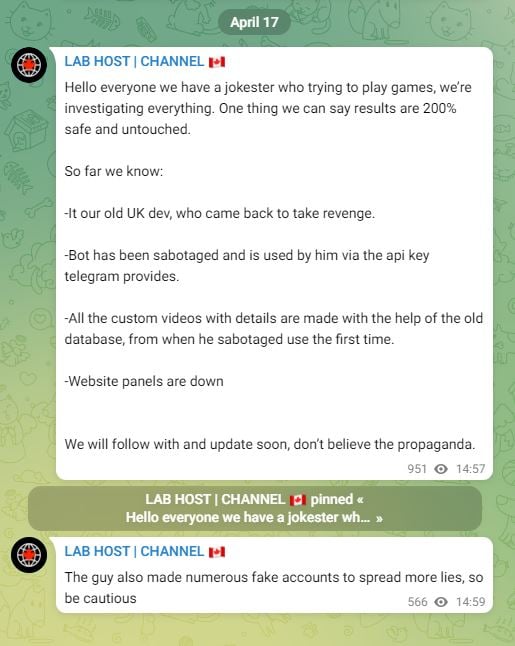
Lab Host's Telegram channel displays reassuring messages sent by UK police, which took control of the operation's infrastructure
Around half of the global LabHost userbase will have already received – or will soon receive – messages in the style of Spotify's annual Wrapped campaign which, to the uninitiated, is an Instagram Reels-like summary of each person's listening habits. In this case, it'll be about LabHost activities.
We understand these messages will be sent from official LabHost channels and accounts, cementing the idea that the operation has been thoroughly compromised by the cops.
"You'll be in no doubt after watching that video that we definitely do know what you've been up to," said Richter. "A combination of those people will be arrested or will be subject to other law enforcement activity in the coming months.
We have access to all the data, everything that those users have been doing through that service
"We have access to all the data, everything that those users have been doing through that service, as do 17 countries currently and their law enforcement agencies."
Asked how long the Met has had control of LabHost's infrastructure, Richter defaulted to the defense of not wanting to reveal tactics. Although he did say there was no Hansa-style takeover – in which Dutch officers had control of that dark web market for so long that they could watch fraud happen in real time.
"So we certainly haven't, for example, watched any live frauds take place and been in a position of saying 'Are we going to act now, are we not?' We haven't used tactics that have got us into that realm," explained Richter.
"The reason we're taking this action now is that this is the first time, and it's as early as we felt, that we actually did have the capability to truly disrupt the service in a significant fashion, and also be able to get across to as many of those users as possible that wider messaging, as well as being able to then safeguard the victims, truly know how many UK victims we're looking at, and get proper communication out to them."
Up to 25,000 victims in the UK will have been contacted by the end of Thursday 18 April with details of the phishing scam to which they are believed to have fallen victim. The Met will also have what it's calling a "victim package" on its website that will offer further help and resources. ®
.png)
 7 months ago
49
7 months ago
49 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·