BOOK THIS SPACE FOR AD
ARTICLE AD
The Qlocker ransomware gang has shut down their operation after earning $350,000 in a month by exploiting vulnerabilities in QNAP NAS devices.
Starting on April 19th, QNAP NAS device owners worldwide suddenly discovered that their device's files were replaced by password-protected 7-zip archives.
In addition to the encrypted files, QNAP owners found a !!!READ_ME.txt ransom note explaining that their files were encrypted and needed to visit a Tor site to pay a ransom to get their files back.
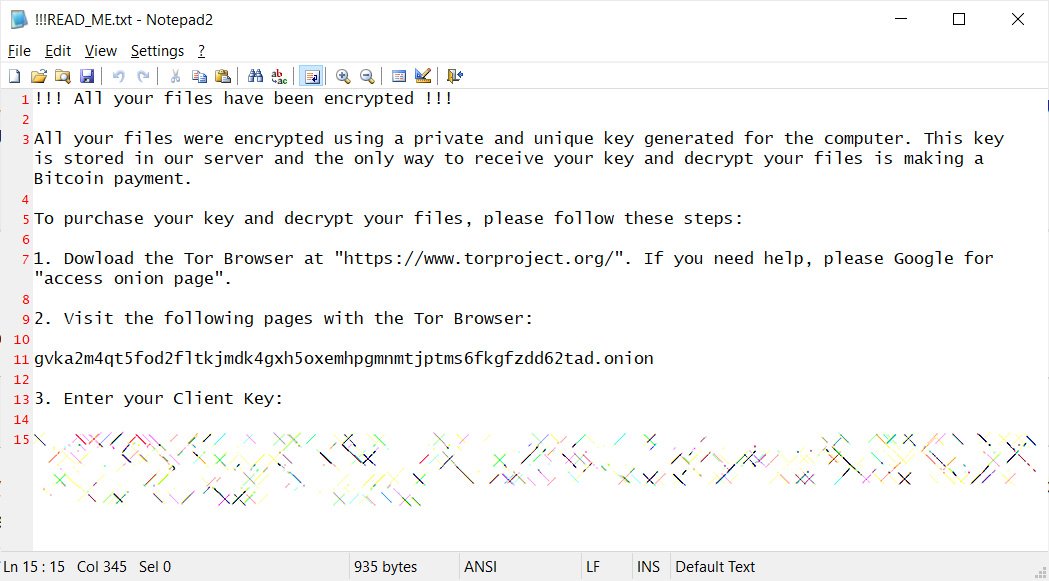 Qlocker ransom note
Qlocker ransom noteThe Tor site identified the attackers as Qlocker and demanded .01 bitcoins, or approximately $550, to receive the password for their files.
Later, it was determined that threat actors conducted the attacks through recently disclosed QNAP vulnerabilities that allowed threat actors to encrypt victims' files using the built-in 7-zip application remotely.
Using such a simple approach allowed them to encrypt over a thousand, if not thousands, of devices in just a month.
Qlocker operation shuts down
As a possible sign of their impending shutdown, the Qlocker Tor sites began displaying a message stating that "This site will be closed soon."
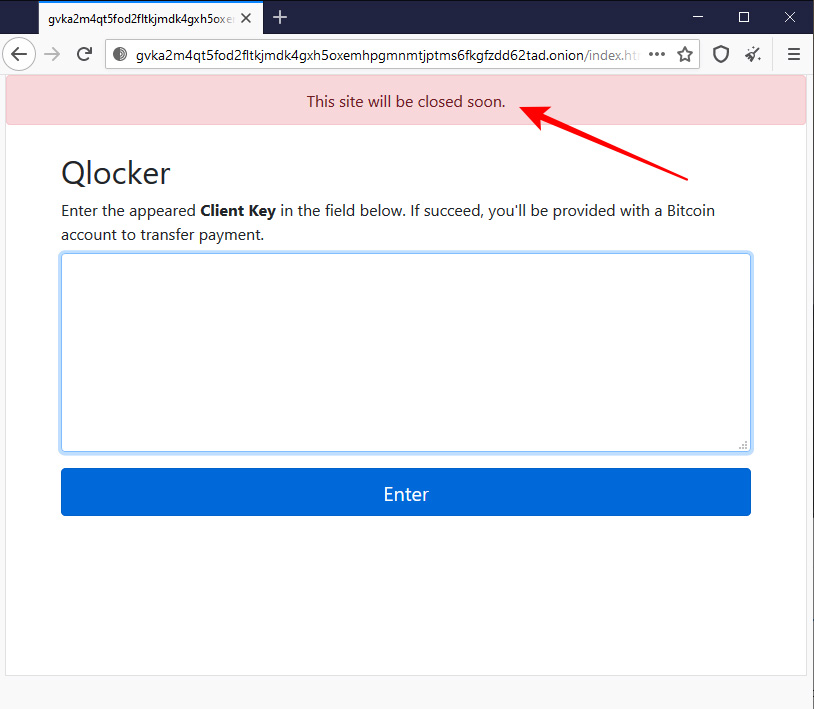 Qlocker Tor site indicating it will shut down soon
Qlocker Tor site indicating it will shut down soonMore recently, the Qlocker gang began a bait-and-switch tactic when it came to ransom payments.
Victims reported that after paying the demanded .01 bitcoins and submitting the transaction ID on the Qlocker Tor site, the site would state that they needed to pay an additional .02 bitcoins to get their files back.
"Bitcoin is getting harder to find, time waits for nothing. The new price is 0.03," the Qlocker Tor site would display during their bait-and-switch.
Eventually, the above site shut down, but another Qlocker Tor site appeared a day or so later.
Today, in BleepingComputer tests and victim's reports in our Qlocker support topic, all of the Qlocker Tor sites are no longer accessible, and victims no longer have a way to pay the ransom.
Since the DarkSide ransomware attack on Colonial Pipeline and the subsequent intensifying of pressure by US law enforcement, the DarkSide ransomware shut down, and REvil has begun to restrict their targets.
Since then, other ransomware operations' Tor sites have gone offline, including those for Ako/Ranzy and Everest.
It is not clear if the shutdown of the Qlocker sites is related to fear of increased law enforcement activity.
Following the money
Instead of demanding millions of dollars to recover files, the threat actors priced their ransom demands at only $500, which led to many businesses paying the ransom to recover their files.
As the Qlocker ransomware operation used a fixed set of Bitcoin addresses that victims were rotated through, it has been possible to track how many bitcoins they received in ransom payments.
Out of the twenty-two Qlocker Bitcoin addresses known by BleepingComputer, victims paid a total of 8.93258497 bitcoins in ransomware. Today that is worth $353,708, but before this week's Bitcoin crash, those same bitcoins would be worth almost $450,000.
If we divide the number of Bitcoins earned by the ransom payment of .01 bitcoins, we come out to approximately 893 victims who have paid the ransom.
This amount of ransoms and victims might be larger if Qlocker used other bitcoin addresses.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·