BOOK THIS SPACE FOR AD
ARTICLE AD
QNAP customers are once again urged to secure their Network Attached Storage (NAS) devices following a massive Qlocker ransomware campaign earlier this month.
In a security advisory published earlier today, the company says that its security team has discovered AgeLocker ransomware samples in the wild, with "the potential to affect QNAP NAS devices."
"To secure your device, we strongly recommend regularly updating QTS or QuTS hero and all installed applications to their latest versions to benefit from vulnerability fixes," QNAP said. "You can check the product support status to see the latest updates available to your NAS model."
Customers are also warned not to expose their NAS devices on the Internet since it would allow potential attackers to find them and gain access to the users' data.
A QNAP PSIRT spokesperson told BleepingComputer that NAS devices recently compromised by AgeLocker ransomware were running outdated firmware.
"So we'd like to urgent users to update the firmware and apps to the latest version to keep the devices safe from attack," the spokesperson added.
If you have enabled manual port forwarding, auto port forwarding (UPnP, Universal Plug and Play) and demilitarized zone (DMZ) for QNAP NAS in your router or modem configuration, your QNAP NAS is directly connected to the Internet. Some other connection methods that put your QNAP NAS directly on the Internet include obtaining a public IP address (static/PPPoE/DHCP) by QNAP NAS itself. — QNAP
Ransomware that also steals data before encryption
AgeLocker ransomware was first spotted in the wild in July 2020 and, since then, it has already targeted QNAP NAS devices worldwide in a September 2020 campaign.
This ransomware strain uses an encryption algorithm known as Age (short for Actually Good Encryption), designed as a GPG replacement for encrypting files, backups, and streams.
Age uses the X25519 (an ECDH curve), ChaChar20-Poly1305, and HMAC-SHA256 algorithms, according to ransomware decryption expert Michael Gillespie, which makes it a very secure method to encrypt victims' files.
While in the case of the first victim, AgeLocker operators asked for a 7 bitcoin ransom (roughly $64,500 at the time), we do not yet know the amount requested to decrypt victims' files during September 2020 attacks.
QNAP devices were previously targeted by eCh0raix ransomware (aka QNAPCrypt) in June 2019 and June 2020.
Starting last weekend, QNAP users were once again hit by ransomware in a massive and still ongoing Qlocker ransomware campaign.
While at first QNAP told BleepingComputer that Qlocker exploits an SQL Injection vulnerability (CVE-2020-36195) to encrypt unpatched devices, it was later discovered that it also used hardcoded credentials in the HBS 3 Hybrid Backup Sync app.
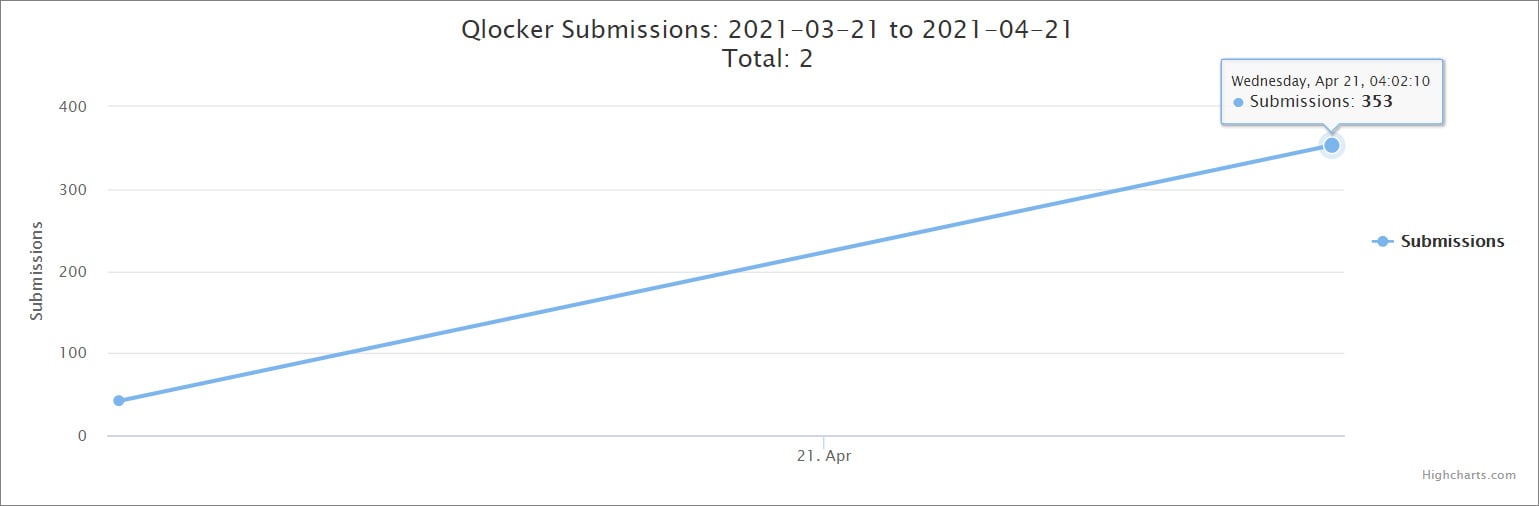 ID-R Qlocker submissions
ID-R Qlocker submissionsHow to secure your NAS device
To update QTS or QuTS hero and all your installed applications, you should go through the following steps.
Update QTS or QuTS hero:
Log on to QTS or QuTS hero as administrator. Go to Control Panel > System > Firmware Update. Under Live Update, click Check for Update. QTS or QuTS hero downloads and installs the latest available update.Update all installed apps:
Log on to QTS or QuTS hero as administrator. Go to App Center > My Apps. Check the All option before clicking Install Updates. Click OK on the confirmation message to update all installed apps to their latest versions.The company also advised customers in the past to change the default access port number, use strong account passwords, and enable password policies to further secure their devices.
QNAP NAS owners should also go through the following checklist designed to mitigate against potential attacks:
Change all passwords for all accounts on the device Remove unknown user accounts from the device Make sure the device firmware is up-to-date and all of the applications are also updated Remove unknown or unused applications from the device Install QNAP MalwareRemover application via the App Center functionality Set an access control list for the device (Control panel -> Security -> Security level).png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·