BOOK THIS SPACE FOR AD
ARTICLE ADThere are active ransomware and brute-force attacks being launched against internet-exposed, network-attached storage devices, the device maker warned.
Get your internet-exposed, network-attached storage (NAS) devices off the internet now, Taiwanese manufacturer QNAP warns: Ransomware and brute-force attacks are widely targeting all network devices.
“The most vulnerable victims will be those devices exposed to the Internet without any protection,” QNAP said on Friday, urging all QNAP NAS users to follow security-setting instructions that the Taiwanese NAS maker included in its alert.
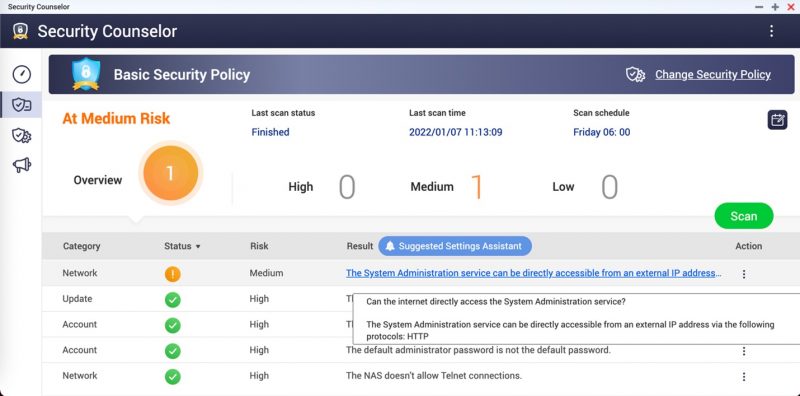
First off, to check whether your NAS is exposed to the internet, QNAP instructed device owners to open the device’s Security Counselor: a built-in security portal that integrates anti-virus and anti-malware software.
“Your NAS is exposed to the Internet and at high risk if there shows ‘The System Administration service can be directly accessible from an external IP address via the following protocols: HTTP’ on the dashboard.” —QNAP
QNAP directed customers to this site to figure out which router ports are exposed to the internet.
Fending Off Attacks Against Exposed NAS Devices
If your NAS device turns out to be exposed to the internet, QNAP recommended taking these two steps to secure it:
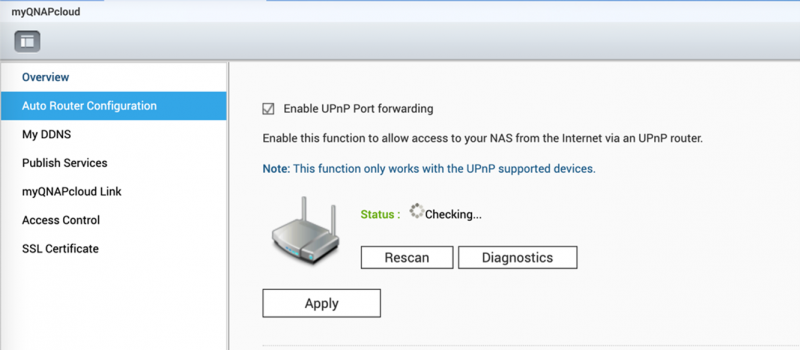
Disable the Port Forwarding function of the router. Go to the management interface of your router, check the Virtual Server, NAT or Port Forwarding settings, and disable the port forwarding setting of NAS management service port (port 8080 and 433 by default). Disable the UPnP function of the QNAP NAS. Go to myQNAPcloud on the QTS menu, click the “Auto Router Configuration,” and unselect “Enable UPnP Port forwarding.”QNAP also provides detailed instructions on how to prevent malware infections, including via password hygiene, enabling IP and account access protection to prevent brute force attacks, disabling SSH and Telnet connections if you don’t use these services, and avoiding the use of default port numbers such as 22, 443, 80, 8080 and 8081.
A Plague of Ransomware Attacks
QNAP didn’t specify which ransomware gangs or strains are involved in the ongoing attacks, but QNAP device owners have suffered through more than their share over the past few years.
That includes repeated targeting by operators wielding eCh0raix ransomware. aka QNAPCrypt.
In August 2021, Palo Alto Network Unit 42 researchers put out a report about a new variant of eCh0raix that was exploiting a critical bug, CVE-2021-28799 – an improper authorization vulnerability that gives attackers access to hard-coded credentials so as to plant a backdoor account – in the Hybrid Backup Sync (HBS 3) software on QNAP’s NAS devices. Users had started reporting attacks that abused what turned out to be the same flaw in April 2021.
eCh0raix was also used to target QNAP NAS servers in 2019, in targeted attacks that brute-forced weak credentials and exploited known vulnerabilities. QNAP also came under attack by operators inflicting Qlocker ransomware in April 2021.
Password Reset: On-Demand Event: Fortify 2022 with a password security strategy built for today’s threats. This Threatpost Security Roundtable, built for infosec professionals, centers on enterprise credential management, the new password basics and mitigating post-credential breaches. Join Darren James, with Specops Software and Roger Grimes, defense evangelist at KnowBe4 and Threatpost host Becky Bracken. Register & Stream this FREE session today – sponsored by Specops Software.
.png)

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·