BOOK THIS SPACE FOR AD
ARTICLE AD
The Raccoon Stealer malware is back with a second major version circulating on cybercrime forums, offering hackers elevated password-stealing functionality and upgraded operational capacity.
The Raccoon Stealer operation shut down in March 2022 when its operators announced that one of the lead developers was killed during Russia’s invasion of Ukraine.
The remaining team promised to return with a second version, relaunching the MaaS (malware as a service) project on upgraded infrastructure and with more capabilities.
According to the security analysts at Sekoia, Raccoon Stealer 2.0 is now promoted on Telegram and hacking forums, with the first samples captured by malware analysts earlier this month.
Raccoon’s silent re-emergence
The admin of the project posted a teaser on June 2, 2022, informing the community that the testing of the Raccoon Stealer 2.0 has been underway for two weeks and "clients" have been happy with the beta.
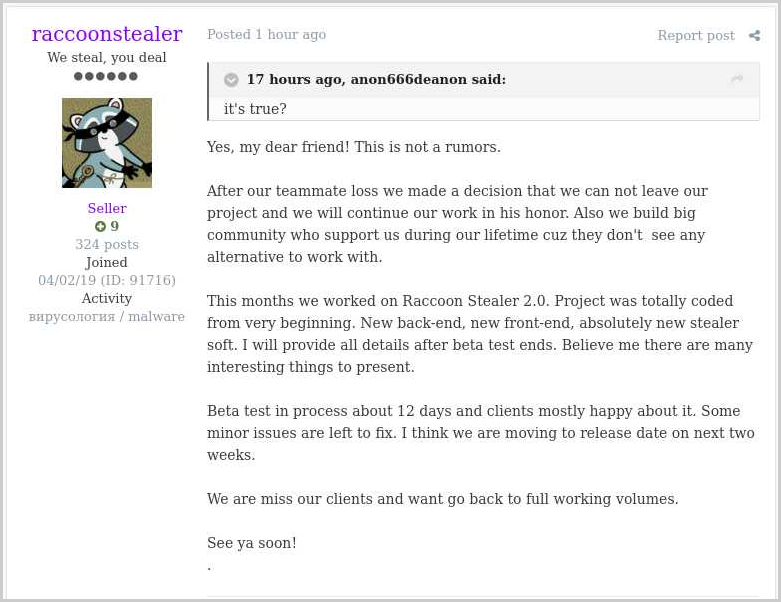 Raccoon's representative announced success of beta (KELA)
Raccoon's representative announced success of beta (KELA)According to the malware authors, the new Raccoon version was built from scratch using C/C++, featuring a new back-end, front-end, and code to steal credentials and other data.
A new malware family detection was discussed among analysts on Twitter on June 8, 2022, who assigned the name “RecordBreaker,” not realizing this is the next major version of Raccoon Stealer.
Sekoia’s technical analysis now confirms that this 56KB sample is the new Raccoon, able to work on 32 and 64-bit systems without any dependencies, only fetching eight legitimate DLLs from its C2 servers.
The C2 also provides the malware with its configuration (apps to target, URL hosting the DLLs, token for data exfiltration), receives machine fingerprint data, and then waits for individual POST requests that contain stolen information.
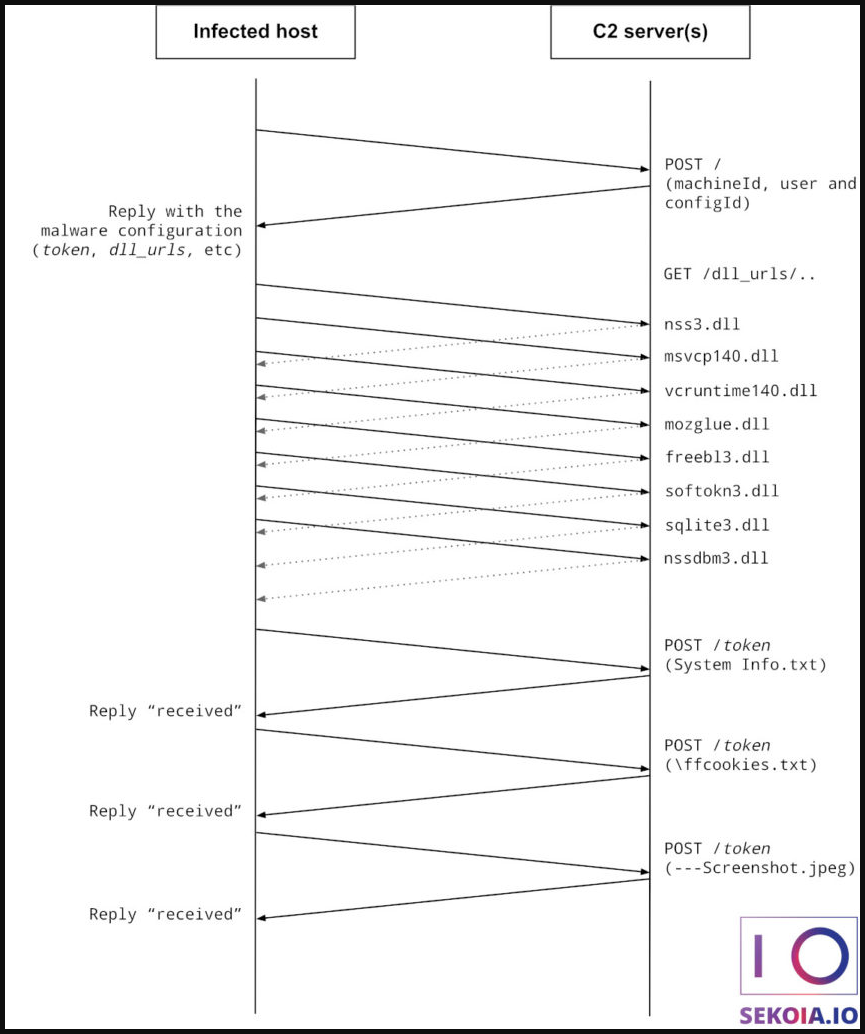 Raccoon Stealer's data exchange with the C2 (Sekoia)
Raccoon Stealer's data exchange with the C2 (Sekoia)The data stolen by Raccoon Stealer 2.0 includes the following:
Basic system fingerprinting info. Browser passwords, cookies, autofill data, and saved credit cards. Cryptocurrency wallets and web browser extensions including MetaMask, TronLink, BinanceChain, Ronin, Exodus, Atomic, JaxxLiberty, Binance, Coinomi, Electrum, Electrum-LTC, and ElectronCash. Individual files located on all disks. Screenshot capturing. Installed applications list.While the malware authors claim the exfiltrated data is being encrypted, Sekoia didn’t observe any functions of this type in the analyzed sample.
What stands out is that the new Raccoon sends data each time it collects a new item, which increases the risk of detection but ensures maximum effectiveness until the malware is discovered and uprooted from the host.
Likely to see increased usage
Raccoon Stealer’s exit from the market was so short that one would call it more of a temporary hiatus, so neither its reputation nor cybercriminal interest in it has faded.
While other information-stealers appeared during Raccoon Stealer's hiatus, such as Mars Stealer and Jester Stealer, none of them had the chance to reach Raccoon’s notoriety and reputation.
“We expect a resurgence of Raccoon Stealer v2, as developers implemented a version tailored to the needs of cybercriminals (efficiency, performance, stealing capabilities, etc.) and scaled their backbone servers to handle large loads,” comments Sekoia in the report.
Finally, it is essential to note that Raccoon Stealer’s second major version is currently only available to a limited number of hackers, most likely previous customers. The cost is set to $275/month, or $125/week.
 Raccoon's announcement of beta on Telegram
Raccoon's announcement of beta on Telegram(Sekoia)
Its operators have chosen not to announce Raccoon’s wide availability yet, possibly because they’re still working on some aspects of the malware.
Sekoia highlights the absence of modern anti-analysis and detection avoidance mechanisms in the examined sample, so these could be implemented next.
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·