BOOK THIS SPACE FOR AD
ARTICLE AD
Security researchers are warning that external remote access services continue to be the main vector for ransomware gangs to breach company networks but there's a notable uptick in exploiting vulnerabilities.
Along with phishing and exploiting vulnerabilities in a public-facing application, these are the primary methods of compromise that ultimately lead to threat actors stealing data and encrypting systems.
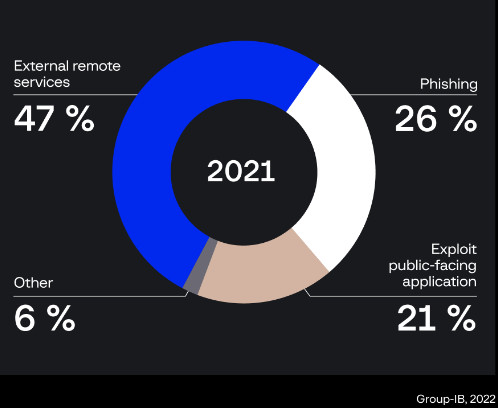 source: Group-IB
source: Group-IBAccording to cybersecurity company Group-IB, threat actors are commonly targeting remote desktop (RDP) servers exposed on the web for initial access into a network.
Compromised credentials are also popular with some ransomware affiliates, who use the logins to attack the infrastructure from the inside.
Vulnerability exploitation on the rise
The cybersecurity company notes in a report today that last year ransomware gangs started to focus on multiple vulnerabilities in public-facing applications, and moved quickly to adding exploits for newly disclosed security issues.
Among the most notable vulnerabilities that Group-IB identified as being used by ransomware threat actors in 2021 are the following:
CVE-2021-20016 (SonicWall SMA100 SSL VPN) CVE-2021-26084 (Atlassian Confluence) CVE-2021-26855 (Microsoft Exchange) CVE-2021-27101, CVE-2021-27102, CVE-2021-27103, and CVE-2021-27104 (Accellion FTA) CVE-2021-30116 (Kaseya VSA) CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207 (Microsoft Exchange) CVE-2021-35211 (SolarWinds)A recently published joint report from Cyber Security Works, Securin, Cyware, and Ivanti notes that the number of vulnerabilities associated with ransomware attacks has grown to 310 in the first quarter of 2022.
The companies identified 22 new security issues being exploited by ransomware gangs in the first months of the year, an 7.6% increase since December 2021.
Not all bugs are new, though. Half of the flaws recently linked to ransomware attacks were disclosed in 2019. However, public exploits exist for many of them, which makes the attacker’s job much easier.
In the first quarter of 2022, the four companies found that ransomware actors were actively exploiting a total of 157 vulnerabilities, slightly more than in the previous quarter.
Techniques and tools
Looking at the threat actors’ leak sites, Group-IB says that ransomware gangs published information from 3,500 victims, most of them based in the U.S. (1,655).
The most aggressive ransomware operations in 2021 were LockBit and Conti (also confirmed in reports from other companies), each with a victim count of 670 and 640, respectively. The third spot was occupied by Pysa, with data from 186 victims published on their leak site.
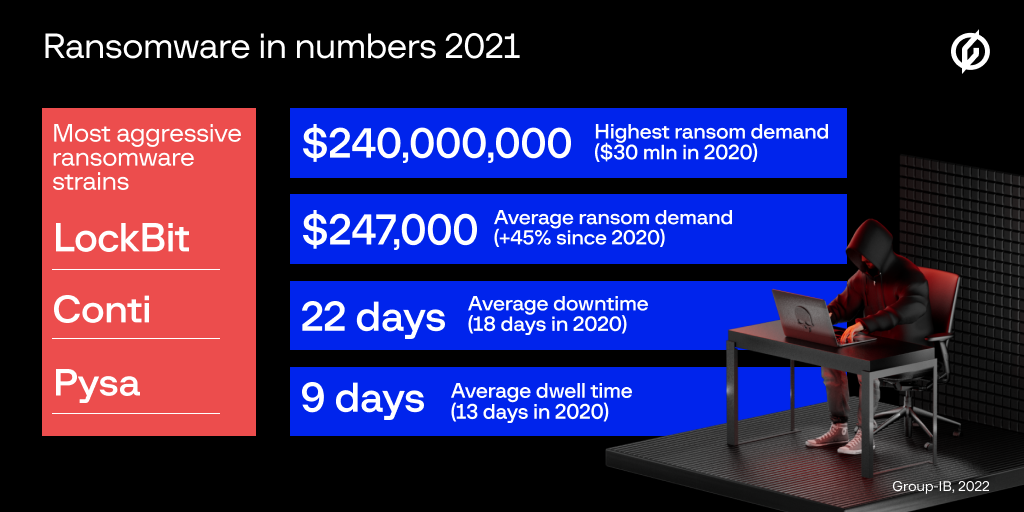 source: Group-IB
source: Group-IBThe company’s digital forensics and incident response (DFIR) team investigated more than 700 ransomware attacks last year and found that data exfiltration had occurred in 63% of the cases.
Based on data collected from these incidents, Group-IB estimates that the ransom demand averaged $247,000 last year.
Data exfiltration remains a strong tactic for ransomware actors to pressure victims into paying a ransom. Some gangs have gone as far as creating custom tools and offering them to affiliates.
For instance, LockBit provides an automated data collection module called StealBit, while BlackMatter had the ExMatter tool. These utilities selected files for exfiltration based on specific extensions or keywords, that were more likely to include valuable information for the attackers.
Among the techniques observed by Group-IB in ransomware attacks, at the top of the chart are the use of command and scripting interpreters and remote services, both being part of all attacks that the researchers investigated
Additionally, the adversaries also used various methods to discover remote systems, steal credentials (Mimikatz, Lazagne), and disable security tools.
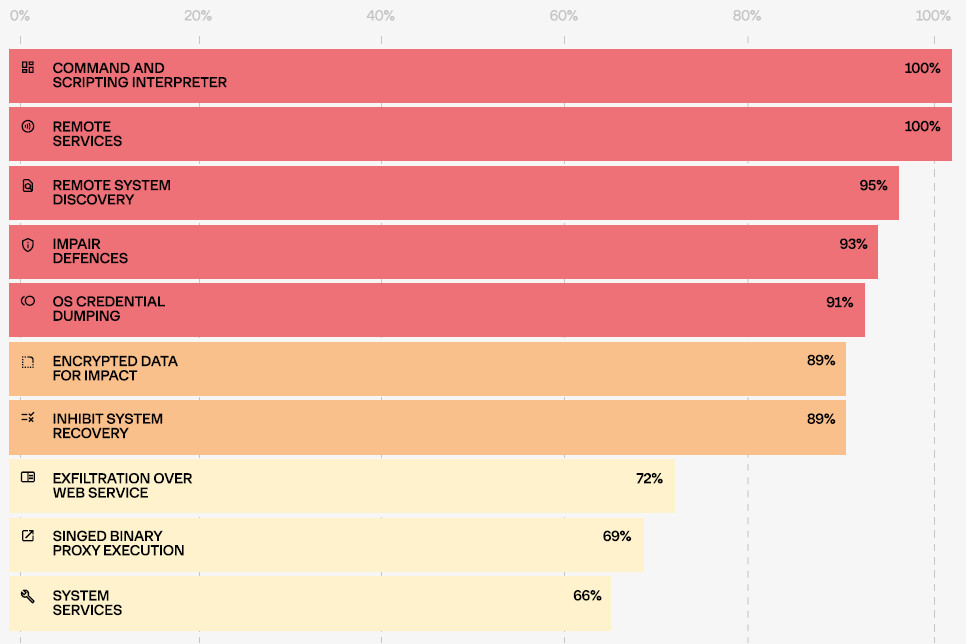 source: Group-IB
source: Group-IBAs for the tools used in various steps of an attack, Group-IB created a top 10, where SoftPerfect Network Scanner is at the head of the list.
In more than half of the investigated ransomware incidents, the researchers found a Cobalt Strike beacon, a common tool for post-exploitation stages as it allows a wide range of actions (script execution, logging keystrokes, file downloads).
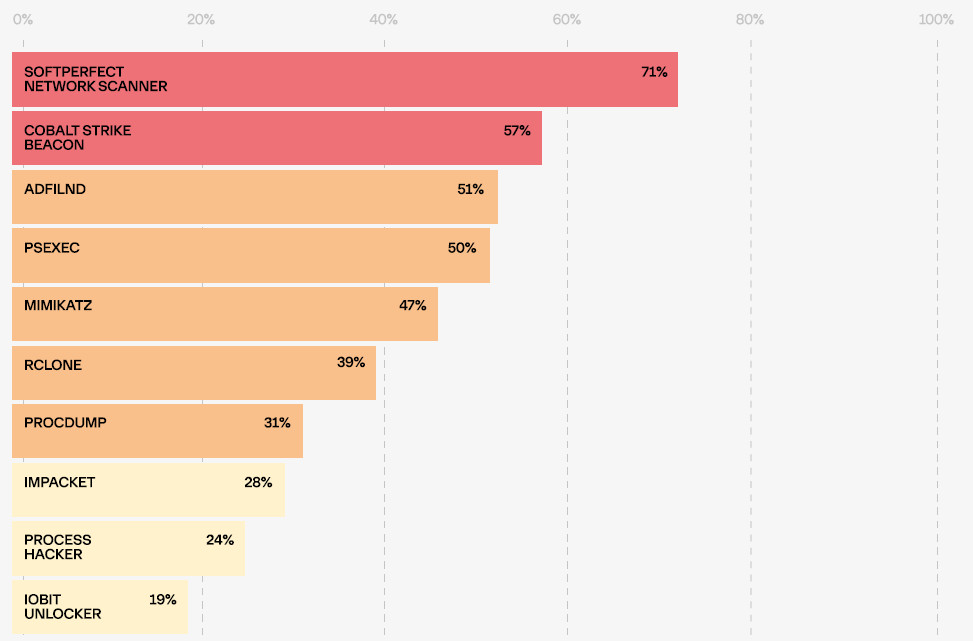 source: Group-IB
source: Group-IBDefenders can use this information to set up detections that could catch ongoing malicious activity before the final strike occurs.
However, despite changing tactics, and adopting new tools and techniques, the main stages of a ransomware attack remain the same:
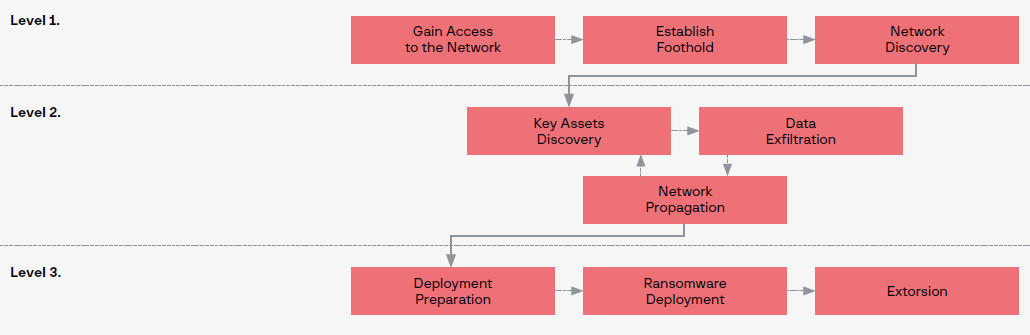 source: Group-IB
source: Group-IBOleg Skulkin, head of Group-IB’s DFIR team, says that merging tactics, techniques, and procedures (TTPs) due to affiliates migrating from one ransomware operation to another makes it difficult for security professionals to keep track of the methods this adversary adopts.
But defining the main trends in a standardized way like the MITRE ATT@CK matrix should make it easier to prepare for ransomware incidents.
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·