BOOK THIS SPACE FOR AD
ARTICLE ADMany online services allow users to reset their passwords by clicking a link sent via SMS, and this unfortunately widespread practice has turned mobile phone numbers into de facto identity documents. Which means losing control over one thanks to a divorce, job termination or financial crisis can be devastating.
Even so, plenty of people willingly abandon a mobile number without considering the potential fallout to their digital identities when those digits invariably get reassigned to someone else. New research shows how fraudsters can abuse wireless provider websites to identify available, recycled mobile numbers that allow password resets at a range of email providers and financial services online.

Researchers in the computer science department at Princeton University say they sampled 259 phone numbers at two major wireless carriers, and found 171 of them were tied to existing accounts at popular websites, potentially allowing those accounts to be hijacked.
The Princeton team further found 100 of those 259 numbers were linked to leaked login credentials on the web, which could enable account hijackings that defeat SMS-based multi-factor authentication.
“Our key finding is that attackers can feasibly leverage number recycling to target previous owners and their accounts,” the researchers wrote. “The moderate to high hit rates of our testing methods indicate that most recycled numbers are vulnerable to these attacks. Furthermore, by focusing on blocks of Likely recycled numbers, an attacker can easily discover available recycled numbers, each of which then becomes a potential target.”
The researchers located newly-recycled mobile numbers by browsing numbers made available to customers interested in signing up for a prepaid account at T-Mobile or Verizon (apparently AT&T doesn’t provide a similar interface). They said they were able to identify and ignore large blocks of new, unused numbers, as these blocks tend to be made available consecutively — much like newly printed money is consecutively numbered in stacks.
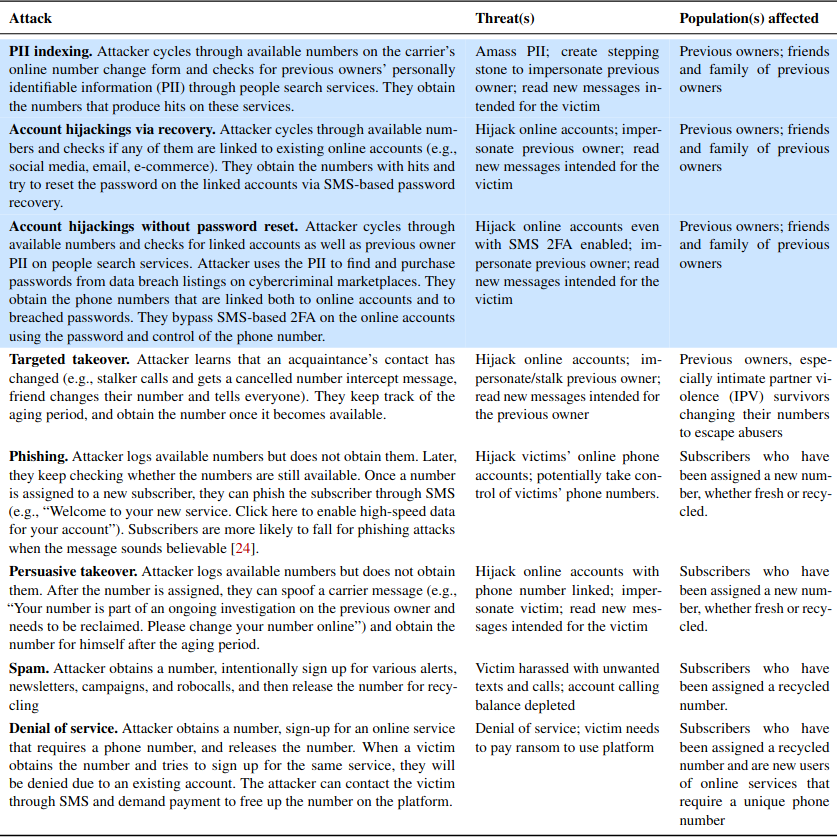
The Princeton team has a number of recommendations for T-Mobile and Verizon, noting that both carriers allow unlimited inquiries on their prepaid customer platforms online — meaning there is nothing to stop attackers from automating this type of number reconnaissance.
“On postpaid interfaces, Verizon already has safeguards and T-Mobile does not even support changing numbers online,” the researchers wrote. “However, the number pool is shared between postpaid and prepaid, rendering all subscribers vulnerable to attacks.”
They also recommend the carriers teach their support employees to remind customers about the risks of relinquishing a mobile number without first disconnecting it from other identities and sites online, advice they generally did not find was offered when interacting with customer support regarding number changes.
In addition, the carriers could offer their own “number parking” service for customers who know they will not require phone service for an extended period of time, or for those who just aren’t sure what they want to do with a number. Such services are already offered by companies like NumberBarn and Park My Phone, and they generally cost between $2-5 per month.
The Princeton study recommends consumers who are considering a number change instead either store the digits at an existing number parking service, or “port” the number to something like Google Voice. For a one-time $20 fee, Google Voice will let you port the number, and then you can continue to receive texts and calls to that number via Google Voice, or you can forward them to another number.
Porting seems like less of a hassle and potentially safer considering the average user has something like 150 accounts online, and a significant number of those accounts are going to be tied to one’s mobile number.
While you’re at it, consider removing your phone number as a primary or secondary authentication mechanism wherever possible. Many online services require you to provide a phone number upon registering an account, but in many cases that number can be removed from your profile afterwards.
It’s also important for people to use something other than text messages for two-factor authentication on their email accounts when stronger authentication options are available. Consider instead using a mobile app like Authy, Duo, or Google Authenticator to generate the one-time code. Or better yet, a physical security key if that’s an option.
The full Princeton study is available here (PDF).
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·