BOOK THIS SPACE FOR AD
ARTICLE AD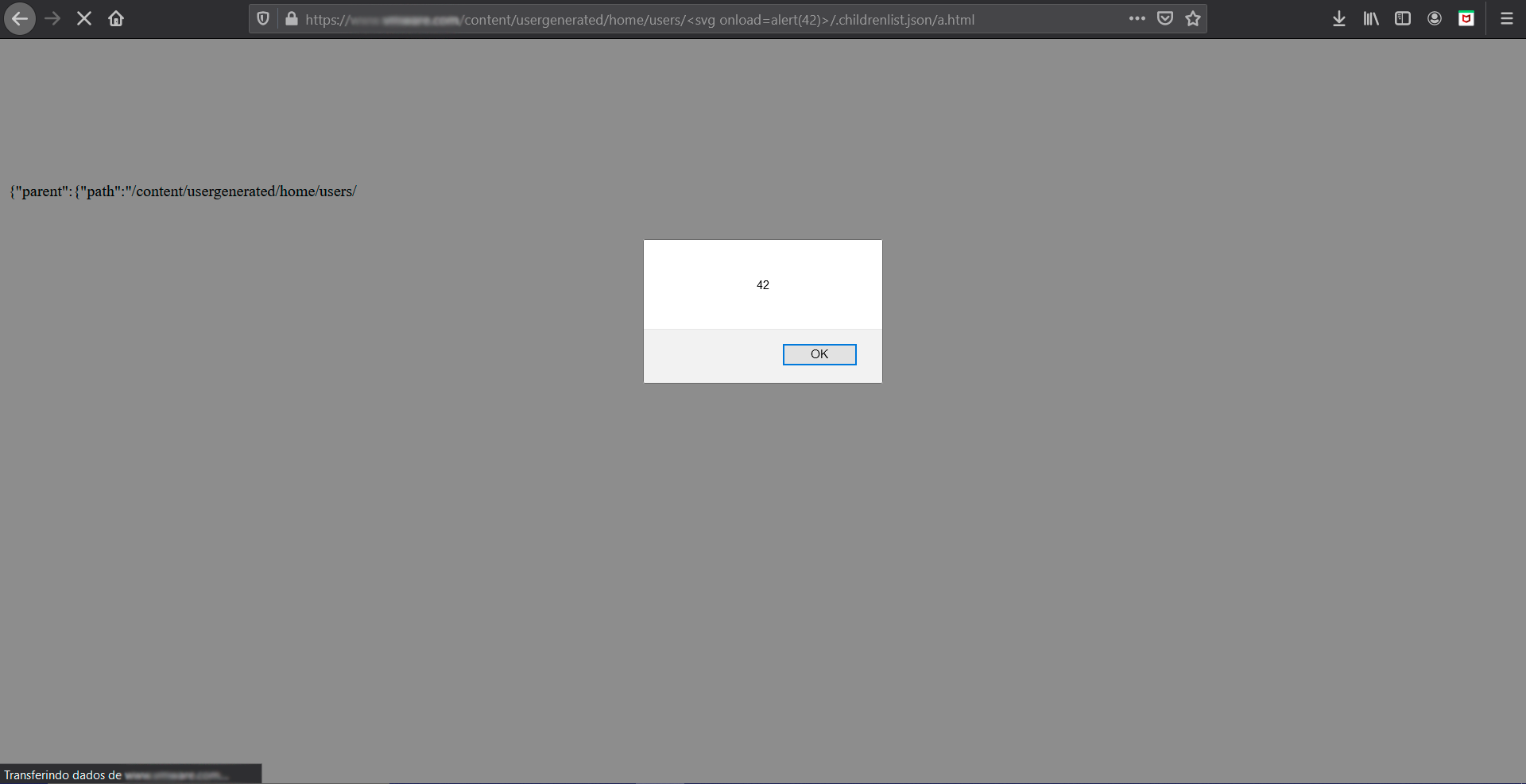
Hi, everyone! My name is Luan and i’m a medical student from Brazil who also likes computers. The following history is how i found multiple vulnerabilities in the main website of a Future 50 company, related to a CVE that is almost 5 years old!
Let’s begin!
I was reading some content in the company main website when i looked at the URL and it was something like following:
https://redacted.com/content/dam/somepage
Then i remembered an awesome article i’ve read: https://clarkvoss.medium.com/the-cve-that-will-never-die-86149b450840
Definitely the server was running Adobe Experience Manager, so i started to look for vulns.
The CVE has never died
My first attempt was successful and the server has misconfigured GET servlet. I could see everything under any path just by appending “.children.json” to the URL.

For my surprise, the server also has misconfigured POST servlet, so i was able to create content by a POST request like following:


After playing around with some requests, i got a reflection and i created a payload for reflected XSS.
Unfortunately the company has not a bug bounty program, but they do gave me a license key for their virtualization software, that costs 200 dollars!
.png)
 3 years ago
224
3 years ago
224 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·