BOOK THIS SPACE FOR AD
ARTICLE ADHeyyy Everyoneee,
I hope everyone is doing good , it’s been a while since I haven’t shared any writeup of my finding’s.
This blog post is going to be about a reflected xss bug affecting Facebook mirror websites. I will be explaining the whole process how I found the vulnerable endpoint.
Well many people ask me how do I look for xss bugs so in this same blog I will also share my method of finding xss.
And here we go…..
I was collecting subdomains of thefacebook.com domain, as I have seen many writeups regarding bugs found in thefacebook.com subdomain only. I wanted to find something there too :)
Started with collecting the subdomains. I basically use tools like Findomain, Subfinder,Assetfinder ,etc to find subdomains of my target. After I collected the subdomains I used another tool called httprobe
After the subdomain enumeration part is completed. I have a habit of doing directory bruteforcing(using ffuf) on all the collected hosts from httprobe, then going through them to see if I can find some easy wins. Look at the below code that’s how I do it
python3 dir.py httprobe.txtWhile I was looking at the https://mirror-ext.glbx.thefacebook.com ffuf result:


Only one directory was there,I decided to look what might be there. http://mirror-ext.glbx.thefacebook.com/help/
It was normal help page with the support email address, didn’t seem interesting to me at first but looking at the page source I could see something ineteresting.
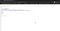
Look at the second line, I tried accessing that endpoint http://mirror-ext.glbx.thefacebook.com/.layout/mirror.php and it was just a blank page :(

This time there was nothing in the page source code too that I can look further into, then I decided to find more php endpoints under the /.layout directory.

These were the files which I was able to find using different wordlists. They were all same as the earlier one mirror.php blank page, only one was different header.php
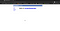
Looking at the page source code I found that the endpoint was getting reflected inside anchor tag href value, it might be vulnerable to xss so I started testing for it.

Adding characters like “>< at the end of the url gave not found page.
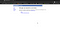
I didn’t wanted to give up so easily as I can smell xss there. I started bruteforcing for parameters but didn’t find any.
Upon adding a slash and then another directory name didn’t gave me the not found error like last time.I tried this because of @brutelogic blog which I read in the past
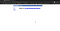

Trying again with “>< and I found that they are getting url encoded.

Later I realised that the href value is inside single quotes. So trying with single quote this time.
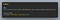
I tried this at first when I saw that my input was getting reflected inside href, href=’/javascript:alert()’, but this wasn’t working because there is a slash before our input. I started looking on google for a way to include two href in a single anchor tag , found a solution on https://stackoverflow.com/questions/13965753/how-can-i-open-multiple-links-using-a-single-anchor-tag
Based upon the solution , the final payload was:
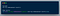
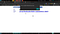
I was like holy sh*t!! I just found a xss on a Facebook domain.
Well I knew about some more Facebook mirror domains so tried to see if I can replicate the same xss on there also. Result was:
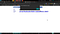
One more subdomain was vulnerable http://mirror.t.tfbnw.net/ but I don’t have any screenshot of it.
That’s the end of the story.
Regarding the fix, now the single quote(‘) is converted to &.

I was rewarded with a $500 bounty for this xss.
Video POC:
How do I look for xss bugs?
I am using this awesome burp plugin called reflector
It basically checks the parameter whose value is getting reflected in the source page and then tries to see which symbols are also getting reflected in the source page like “,>,<,{,},’,etc
You just need to browse the web application , visit every page there, fill all the input fields. Then look at the burp issue tab to see if it has find anything.

Talking about some automation work:
Use tools like paramspider , gau ,etc to collect endpoints which have parameter in them then you can use kxss, dalfox (choice is yours, use whatever tool which works for you, they both are very good.) on them to see if you can find some xss. Below you can see the dalfox tool in action

https://twitter.com/0xAsm0d3us
Beginner Guide
If you are a beginner and want to learn about xss, start by reading blogs there are many great people writing blogs about xss like @brutelogic (He is very kind and helpful. If you are having a hard time bypassing a xss waf or something , he is always ready to help you there. )
https://twitter.com/soaj1664ashar
There are many more just search them on google yourself.
Want to practise xss somewhere goto : Portswigger Web Security Academy
Do ctf challenges related to xss, watch poc videos/writeups they will give you an idea where you should look for xss, which fields are more prone to be vulnerable to xss eg. search fields, submit forms, etc .
That’s all, thankyou very much for reading it till the last. Hope you would have enjoyed it.
Sya everyonee
.png)
 4 years ago
229
4 years ago
229 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·