Cybersecurity researchers have disclosed two new attack techniques on certified PDF documents that could potentially enable an attacker to alter a document's visible content by displaying malicious content over the certified content without invalidating its signature.
"The attack idea exploits the flexibility of PDF certification, which allows signing or adding annotations to certified documents under different permission levels," said researchers from Ruhr-University Bochum, who have systematically analyzed the security of the PDF specification over the years.
The findings were presented at the 42nd IEEE Symposium on Security and Privacy (IEEE S&P 2021) held this week.
The two attacks — dubbed Evil Annotation and Sneaky Signature attacks — hinge on manipulating the PDF certification process by exploiting flaws in the specification that governs the implementation of digital signatures (aka approval signature) and its more flexible variant called certification signatures.
Certification signatures also allow different subsets of modifications on the PDF document based on the permission level set by the certifier, including the ability to write text to specific form fields, provide annotations, or even add multiple signatures.
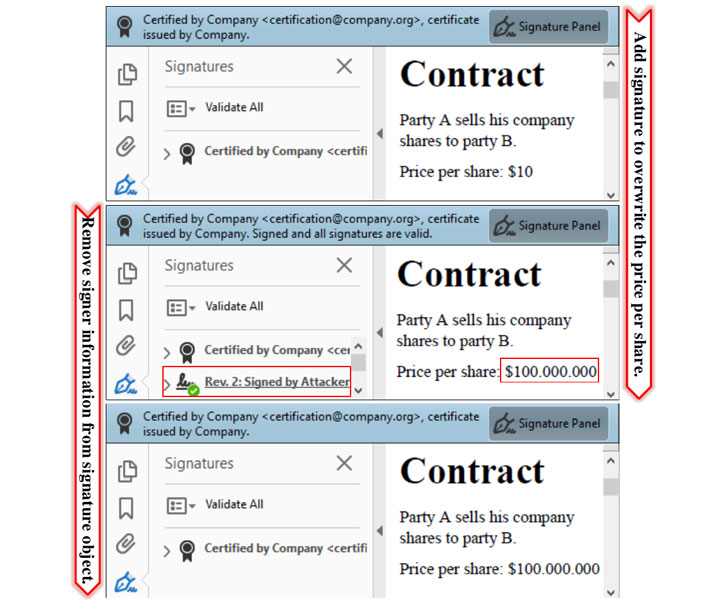
The Evil Annotation Attack (EAA) works by modifying a certified document that's provisioned to insert annotations to include an annotation containing malicious code, which is then sent to the victim. On the other hand, the idea behind the Sneaky Signature attack (SSA) is to manipulate the appearance by adding overlaying signature elements to a document that allows filling out form fields.
"By inserting a signature field, the signer can define the exact position of the field, and additionally its appearance and content, the researchers said. "This flexibility is necessary since each new signature could contain the signer's information. The information can be a graphic, a text, or a combination of both. Nevertheless, the attacker can misuse the flexibility to stealthily manipulate the document and insert new content."
In a hypothetical attack scenario detailed by the academics, a certifier creates a certified contract with sensitive information while enabling the option to add further signatures to the PDF contract. By taking advantage of these permissions, an attacker can modify the contents of the document, say, to display an International Bank Account Number (IBAN) under their control and fraudulently transfer funds, as the victim, unable to detect the manipulation, accepts the tampered contract.
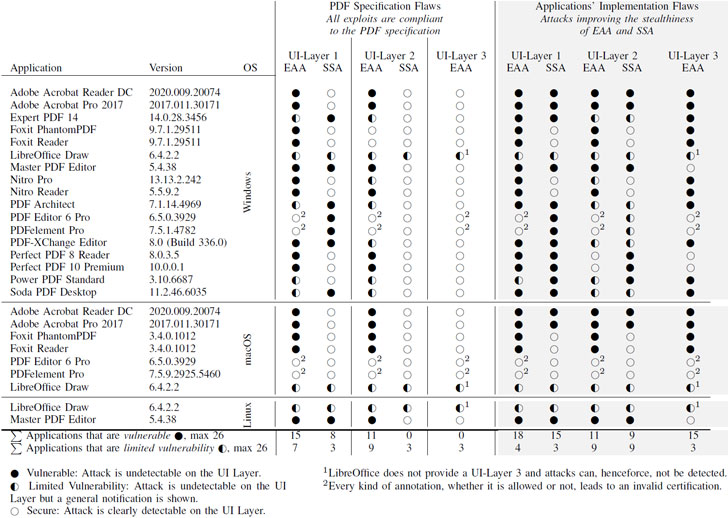
15 of 26 PDF applications evaluated by the researchers, counting Adobe Acrobat Reader (CVE-2021-28545 and CVE-2021-28546), Foxit Reader (CVE-2020-35931), and Nitro Pro, were found vulnerable to the EAA attack, enabling an attacker to change the visible content in the document. Soda PDF Desktop, PDF Architect, and six other applications were identified as susceptible to SSA attacks.
More troublingly, the study revealed that it's possible to execute high-privileged JavaScript code — e.g., redirect the user to a malicious website — in Adobe Acrobat Pro and Reader by sneaking such code via EAA and SSA as an incremental update to the certified document. The weakness (CVE-2020-24432) was addressed by Adobe as part of its Patch Tuesday update for November 2020.
To fend off such attacks, the researchers recommend prohibiting FreeText, Stamp, and Redact annotations as well as ensuring that signature fields are set up at defined locations in the PDF document prior to certification, alongside penalizing any subsequent addition of signature fields with an invalid certification status. The researchers have also created a Python-based utility called PDF-Detector, which parses certified documents to highlight any suspicious elements found in the PDF document.
"Although neither EAA nor SSA can change the content itself – it always remains in the PDF – annotations and signature fields can be used as an overlay to add new content," the researchers said. "Victims opening the PDF are unable to distinguish these additions from regular content. And even worse: annotations can embed high privileged JavaScript code that is allowed to be added to certain certified documents."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
197
3 years ago
197 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·