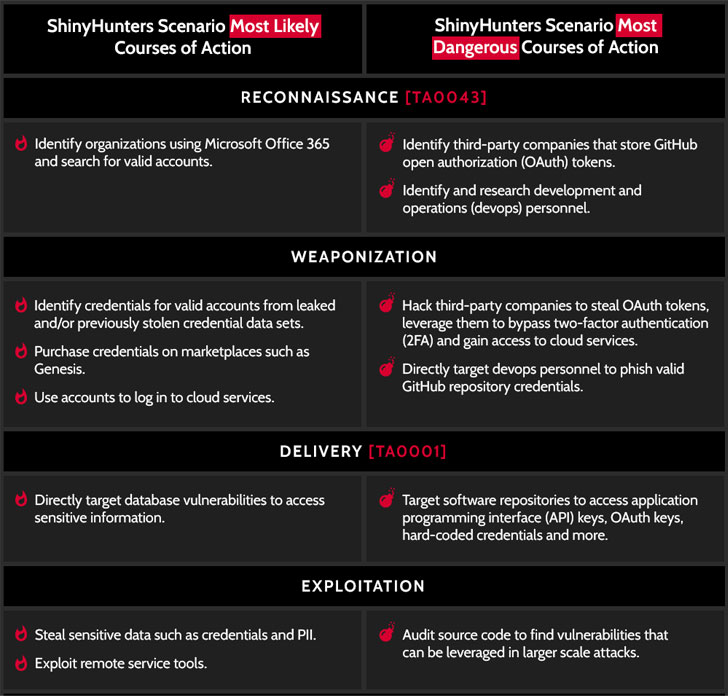
ShinyHunters, a notorious cybercriminal underground group that's been on a data breach spree since last year, has been observed searching companies' GitHub repository source code for vulnerabilities that can be abused to stage larger scale attacks, an analysis of the hackers' modus operandi has revealed.
"Primarily operating on Raid Forums, the collective's moniker and motivation can partly be derived from their avatar on social media and other forums: a shiny Umbreon Pokémon," Intel 471 researchers said in a report shared with The Hacker News. "As Pokémon players hunt and collect "shiny" characters in the game, ShinyHunters collects and resells user data."
The revelation comes as the average cost of a data breach rose from $3.86 million to $4.24 million, making it the highest average cost in 17 years, with compromised credentials responsible for 20% of the breaches reported by over 500 organizations.
Since rising to prominence in April 2020, ShinyHunters has claimed responsibility for a string of data breaches, including Tokopedia, Wattpad, Pixlr, Bonobos, BigBasket, Mathway, Unacademy, MeetMindful, and Microsoft's GitHub account, among others.
An assessment by Risk Based Security found that the threat actor has exposed a total of more than 1.12 million unique email addresses belonging to S&P 100 organizations, education, government and military entities as of late 2020.
Last week, the group began selling a database purportedly containing the personal information of 70 million AT&T customers for a starting price of $200,000, although the U.S. telecom provider has denied suffering a breach of its systems.
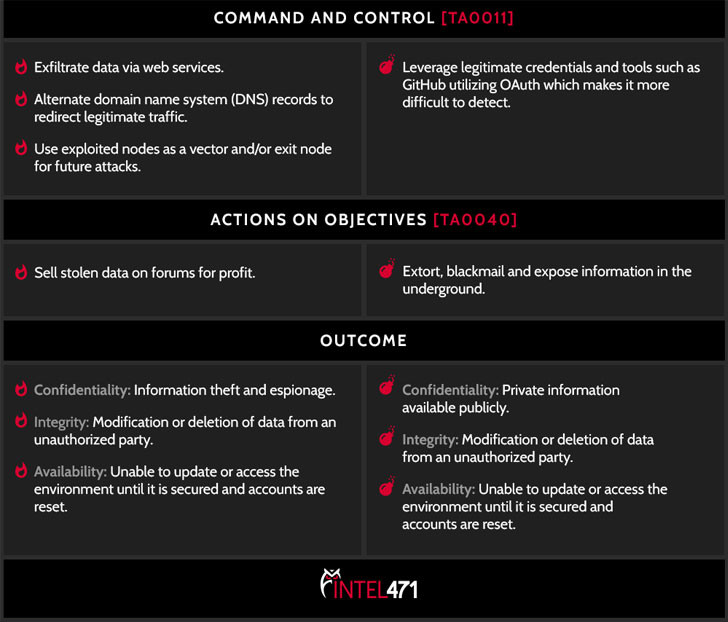
ShinyHunters has a checkered history of compromising websites and developer repositories to steal credentials or API keys to a company's cloud services, which are subsequently abused to gain access to databases and gather sensitive information to be resold for profit or published for free on hacker forums.
The adversary has also been observed targeting DevOps personnel or GitHub repositories in order to steal valid OAuth tokens, leveraging them to breach cloud infrastructure and bypass any two-factor authentication mechanisms.
"ShinyHunters may not have as much notoriety as the ransomware groups that are currently causing havoc for enterprises all over the world. However, tracking actors like this are crucial to preventing your enterprise from being hit with such an attack," the researchers said.
"The information ShinyHunters gathers is often turned around and sold on the same underground marketplaces where ransomware actors use it to launch their own attacks. If enterprises can move to detect activity like ShinyHunters, they in turn can stop ransomware attacks before they are ever launched."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
317
3 years ago
317 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·