BOOK THIS SPACE FOR AD
ARTICLE ADJohn Leyden 07 October 2020 at 15:55 UTC
Malware cartographers offer their insights
ANALYSIS Security researchers have developed techniques to chart how malicious hackers make use of open source offensive security tools.
The research, presented by Paul Litvak of Israeli start-up Intezer at the VB2020 localhost conference last week, informs the long-running debate on whether the development and publication of offensive security tools is beneficial or harmful to security as a whole.
Critics argue that offensive security tools give miscreants an advantage over the security community. Those on the other side of the argument contend that offensive security tools help defenders to mitigate newly discovered techniques and probe their own defenses for flaws.
These tools are also said to have both instructional and educational value, particularly to new starters in the industry.
Up to now, little research has been presented to support either argument, and this has only served to inflame disputes on the topic that occasionally flare up on Twitter.
Ingredients in the witches’ brew of malware
Adversaries with all types of sophistication levels use offensive security tools, from ransomware groups to top government agencies.
Intezer examined the effect of libraries that provide offensive security capabilities, or strips of code taken from larger framework-style tools (such as Mimikatz and Metasploit), that are incorporated into malware.
Overall, 80 projects were checked for code reuse against a database of thousands of labeled threat actor samples from multiple vendor reports from the last few years. A total of 29 additional script-based tools were added using existing vendor reports.
INTERVIEW Metasploit founder HD Moore on bug bounties and coronavirus
The researchers developed templates or fingerprints based on elements of these tools and scripts before searching for matching patterns across a database of millions of malware samples.
The work shed light of elements of threat actor tradecraft such as the favored use of code injection, privilege escalation, and lateral movement technique implementation projects by some groups.
Mapping miscreants
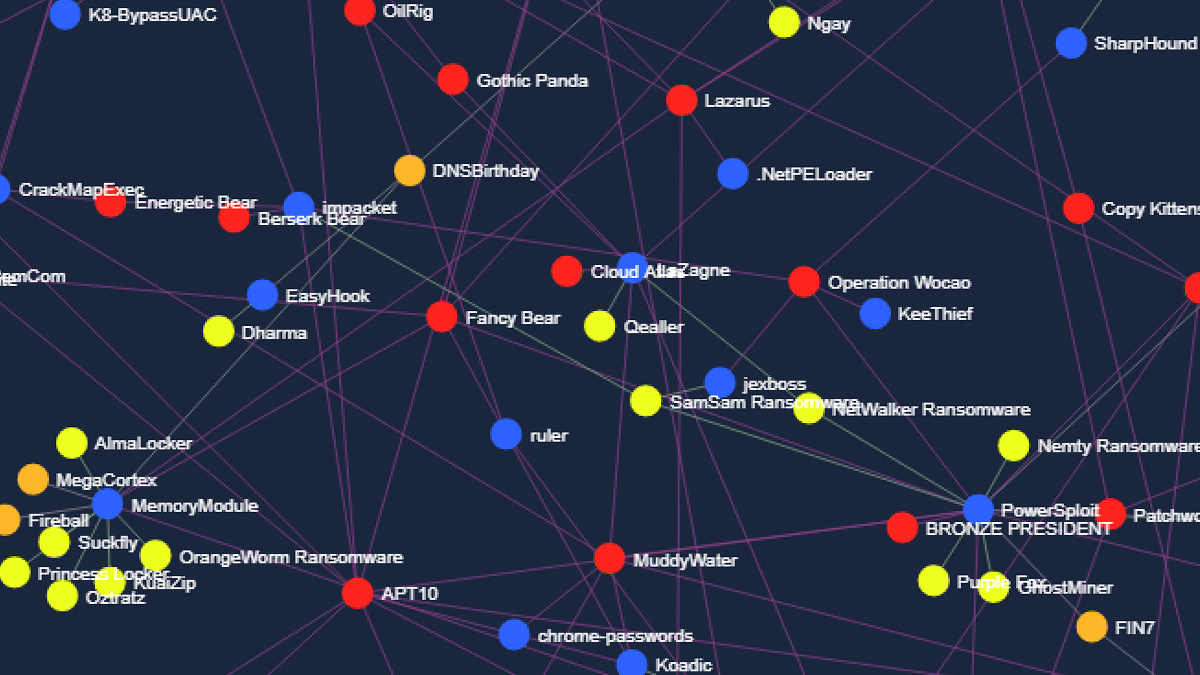
Intezer’s work allowed it to develop an interactive map that displays threat actors’ proclivity for open source offensive toolkits.
Intezer found the most commonly adopted projects were memory injection libraries and remote access trojan (RAT) tools.
The most popular memory injection tool was the ReflectiveDllInjection library, followed by the MemoryModule library. For RATs, Empire, Powersploit, and Quasar were the leading projects.
Attackers varied widely in their level of sophistication, with Litvak categorizing them into three groups.
Lurking at the bottom were threat groups who simply copy and pasted code with little understanding of how it worked. Such lazy coders routinely forget to remove incriminating strings or artifacts.
At a slightly higher level to these so-called ‘script kiddies’ were those who developed on the foundation provided by open source tools. Such groups have an understanding of tools and their protocols and are capable of applying customizations to suit their needs.
The third tier was made up of groups that integrated tools within their open code or made subtle use of frameworks.
For example, the so-called ‘Turla’ group has made use of Metasploit as an initial infection vector for the last two years. Litvak explained:
This allows them some anonymity because if the infection somehow fails… then they just pull out and all that’s left are the artifacts of Metasploit. But it is a generic tool [and] everybody can use it – so it really hurts attribution and allows Turla to exit the operation without letting the defenders know what hit them.Intezer told The Daily Swig that the company has been able to identify a number of malware campaigns based on its mapping project.
For example, back in June it found many almost undetected samples of Lazarus tools by looking for MemoryModule memory injection library users.
RECOMMENDED Open source security: Malicious NPM packages broadcast sensitive user data online
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·