Cybersecurity researchers have unpacked a new Golang-based botnet called Kraken that's under active development and features an array of backdoor capabilities to siphon sensitive information from compromised Windows hosts.
"Kraken already features the ability to download and execute secondary payloads, run shell commands, and take screenshots of the victim's system," threat intelligence firm ZeroFox said in a report published Wednesday.
Discovered first in October 2021, early variants of Kraken have been found to be based on source code uploaded to GitHub, although it's unclear if the repository in question belongs to the malware's operators or if they simply chose to start their development using the code as a foundation.
The botnet – not to be confused with a 2008 botnet of the same name – is perpetuated using SmokeLoader, which chiefly acts as a loader for next-stage malware, allowing it to quickly scale in size and expand its network.
Kraken's features are said to be constantly evolving, with its authors fiddling with new components and altering existing features. Current iterations of the botnet come with functions to maintain persistence, download files, run shell commands, and steal from different cryptocurrency wallets.
The wallets targeted include Armory, Atomic Wallet, Bytecoin, Electrum, Ethereum, Exodus, Guarda, Jaxx Liberty, and Zcash. Also consistently downloaded and executed on the machine is the RedLine Stealer, which is used to harvest saved credentials, autocomplete data, and credit card information from web browsers.
What's more, the botnet comes with an administration panel that enables the threat actor to upload new payloads, interact with a specific number of bots, and view command history and information about the victims.
Over time, Kraken has also emerged as a conduit for the deployment of other generic information stealers and cryptocurrency miners, netting the botnet operators around $3,000 every month. "It is currently unknown what the operator intends to do with the stolen credentials that have been collected or what the end goal is for creating this new botnet," the researchers concluded.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
186
2 years ago
186 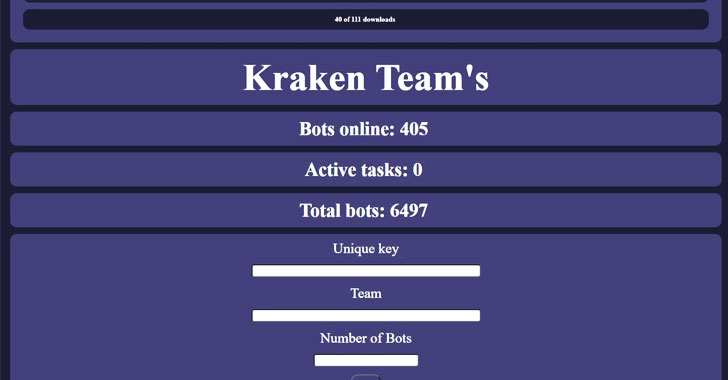

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·