BOOK THIS SPACE FOR AD
ARTICLE AD
I am super excited to write my first ever story on Medium. I will In-Sha-Allah be consistent with my writing and will write more cybersecurity and technology-related blogs. Before starting, I am a cybersecurity university student and a very passionate learner of cybersecurity. I love learning and exploiting things.
I recently read a famous book on web application penetration testing or bug bounty hunting named Real-World Bug Hunting-A Field Guide to Web Hacking By Peter Yaworski. I will talk with you about this book through this blog. This blog will contain two parts, in part 1, I will share my own personal review of this book and secondly, I will share all the resources and bugs discussed in this book.
This book contains all the vulnerabilities that exist in any web application. The methodology used is that, in each chapter, the author discussed a different vulnerability. Firstly author introduces the vulnerability and then two or three real-world bug reports are being discussed. At last, takeaways and summaries are being discussed. I personally have not read any web application books before, so I felt like this book is a bit advance and felt like having strong theoretical knowledge of different vulnerabilities is a prerequisite for this.
If you want to read this book then I can say two things about you. First, if you know theoretical knowledge of different modern vulnerabilities and you have a strong understanding of web technologies then go and read this book. But if you are a very beginner like me and you are struggling to learn web technologies and other stuff then I will suggest to not read this book at first instead try to read books like The Web Application Hacker’s Handbook: Discovering and Exploiting Security Flaws, etc first.
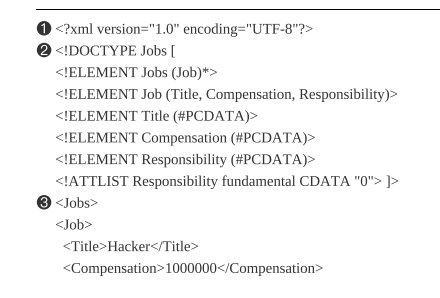
Although I understand the first few chapters very well and got to know the theory of different vulnerabilities like, what is SSRF, Different types of XSS etc and more and more this book developed a hacker mind in me. We have to check each place with a different aproach. But as soon I moved to the middle chapters then the real-life reports become a bit complicated because of the different codes, encoding and javascript scripts. (I will include all the reports chapter wise at the last of this blog so you can find all the materials in order.) For example, I failed to grasp the concept used here

Although I benefited a lot from this book and highly recommend it for those who want to be masters in bug bounty hunting, to read at least once in life. If not now, then read it at the point where you feel like you know all the basics of the web. I came to know about different web application vulnerabilities which I never heard of. I felt like I need to work on my web side. I started learning the basics of web applications. I will recommend to every beginner to learn web development first before diving into bug bounty hunting. The resources shared in this book are amazing, it contains separate chapters just for the resources. (tools, blogs, video channel etc). The very benefit I got from this book is that while mentioning the certain report it contains the name of the person who reported this, I find out that person on Twitter or on LinkedIn and connected with him
So in short this book is amazing but not for very beginners who has just started learning bug bounty hunting but for those who have a little bit of knowledge of web technologies. This book contains very informative resources which I am going t share below.
Click on the report to redirect to the public report. Some of the reports are being made private by HackerOne so they will no longer be available. Although I am attaching everything.
Chapter #2 — Open Redirect
Shopify Theme Install Open Redirect — Report Here
Shopify Login Open Redirect — Report Here
Hackerone Interstitial Redirect — Report Here
Chapter #3 — HTTP Parameter Pollution
Hackerone Social Sharing Buttons — Report Here
Twitter Unsubscribe Notifications — Report Here
Twitter Web Intents — Report Here
Chapter #4 — Cross-site Request Forgery
Shopify Twitter Disconnect — Report Here
Change Users Instacart Zones — Report Here
Badoo Full Account Takeover — Report Here
Chapter #5 — Html Injection And Content Spoofing
Coinbase Comment Injection Through Character Encoding — Report Here
Hackerone Unintended Html Inclusion — Report Here
Hackerone Unintended Html Include Fix Bypass — Report Here
Within Security Content Spoofing — Report Here
Chapter #6 — Carriage Return Line Feed Injection
V.shopify.com Response Splitting — Report Here
Twitter Http Response Splitting — Report Here
Chapter #7 — Cross-site Scripting
Shopify Wholesale — Report Here
Shopify Currency Formatting — Report Here
Yahoo! Mail Stored Xss — Report Here
Google Image Search — Report Here
Google Tag Manager Stored Xss — Report Here
United Airlines Xss — Report Here
Chapter #8 — Template Injection
Uber Angularjs Template Injection — Report Here
Uber Flask Jinja2 Template Injection — Report Here
Rails Dynamic Render — Report Here
Unikrn Smarty Template Injection — Report Here
Chapter #9 — SQL INJECTION
Uber Blind Sqli — Report Here
Drupal Sqli — Report Here
Chapter #10 — Server-side Request Forgery
Esea Ssrf And Querying Aws Metadata — Report Here
Google Internal Dns Ssrf — Report Here
Chpater #11 — Xml External Entity
Read Access To Google — Report Here
Facebook Xxe With Microsoft Word — Report Here
WIKILOC XXE — Report Here
Chapter #12 — Remote Code Execution
Polyvore Imagemagick — Report Here
Algolia Rce On Facebooksearch.algolia.com — Report Here
RCE THROUGH SSH — Report Here
Chapter #13 — Memory Vulnerabilities
php ftp_genlist() integer overflow — Report Here
python hotshot module — Report Here
Libcurl Read Out Of Bounds — Report Here
Chapter #14 — Subdomain Takeover
Ubiquiti Subdomain Takeover — Report Here
Scan.me Pointing To Zendesk — Report Here
Shopify Windsor Subdomain Takeover — Report Here
Snapchat Fastly Takeover — Report Here
Legal Robot Takeover — Report Here
Uber Sendgrid Mail Takeover — Report Here
Chapter #15 — Race Conditions
Exceeding Keybase Invitation Limits — Report Here
Shopify Partners Race Condition — Report Here
Chapter #16 — Insecure Direct Object References
Binary.com Privilege Escalatio — Report Here
Moneybird App Creation — Report Here
Twitter Mopub Api Token Theft — Report Here
chapter 317 —Oauth Vulnerabilities
Stealing Slack Oauth Tokens — Report Here
Passing Authentication With Default Passwords — Report here
Stealing Microsoft Login Tokens — Report here
Swiping Facebook Official Access Tokens — Report here
Chapter #18 — Application Logic And Configuration Vulnerabilities
Bypassing Shopify Administrator Privileges — Report here
Hackerone Signal Manipulation — Report here
Hackerone Incorrect S3 Bucket Permissions — Report Here
Bypassing Gitlab Two-factor — Report Here
Yahoo! Php Info Disclosure — Report Here
Hackerone Hacktivity Voting — Report Here
.png)
 3 years ago
180
3 years ago
180 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·