BOOK THIS SPACE FOR AD
ARTICLE AD“We hereby keep a right (sic) to forward all of the relevant documentation and data to military agencies of our choise (sic)” REvil reportedly wrote.
Sol Oriens, a subcontractor for the U.S. Department of Energy (DOE) that works on nuclear weapons with the National Nuclear Security Administration (NNSA), last month was hit by a cyberattack that experts say came from the relentless REvil ransomware-as-a-service (RaaS) gang.
The Albuquerque, N.M. company’s website has been unreachable since at least June 3, but Sol Oriens officials confirmed to Fox News and to CNBC that the firm became aware of the breach sometime last month.
The company’s statement, captured in a Tweet stream posted by CNBC’s Eamon Javers on Thursday:
“In May 2021, Sol Oriens became aware of a cybersecurity incident that impacted our network environment. The investigation is ongoing, but we recently determined that an unauthorized individual acquired certain documents from our systems. Those documents are currently under review, and we are working with a third-party technological forensic firm to determine the scope of potential data that may have been involved. We have no current indication that this incident involves client classified or critical security-related information. Once the investigation concludes, we are committed to notifying individuals and entities whose information is involved …”
As Javers noted, “we don’t know everything this small company does,” but he posted a sample job posting that indicates that it handles nuclear weapons issues: “Senior Nuclear Weapon System Subject Matter. Expert with more than 20 years of experience with nuclear weapons like the W80-4.” The W80 is a type of nuclear warhead carried on air-launched cruise missiles.
According to an archived version and its LinkedIn profile, Sol Oriens is a “small, veteran-owned consulting firm focused on managing advanced technologies and concepts with strong potential for military and space applications” that works with the “Department of Defense and Department of Energy Organizations, Aerospace Contractors, and Technology Firms (sic) carry out complex programs. … We focus on ensuring that there are well-developed technologies available to maintain a strong National Defense.”
What Was Stolen
Brett Callow, a threat analyst and ransomware expert at the security firm Emsisoft, told Mother Jones that he had spotted Sol Oriens’s internal information posted to the REvil’s dark web blog.
At least for now, the data seems benign enough: It reportedly shows what Mother Jones described as “a company payroll form from September 2020, outing a handful of employees’ names, social security numbers, and quarterly pay. There’s also a company contracts ledger, and a portion of a memo outlining worker training plans. (The memo has Department of Energy and NNSA Defense Programs logos at the top.)”
Whether REvil – or whichever gang proves to be responsible for the attack – got its hands on more sensitive, secret information about the country’s nuclear weapons remains to be seen. But the fact that it got anything at all is, of course, deeply concerning. As Mother Jones pointed out, the NNSA is responsible for maintaining and securing the nation’s nuclear weapons stockpile and works on nuclear applications for the military, along with other highly sensitive missions.
Given all that responsibility, shouldn’t subcontractors’ security profiles be tight enough to fend off REvil or other cyberattackers? REvil reportedly blamed the victim, wagging its finger at Sol Oriens by writing that the subcontractor “did not take all necessary action to protect personal data of their employees and software development for partner companies.” The gang of cyberattackers wrote that above two screenshots of purportedly stolen data, adding that …
We hereby keep a right (sic) to forward all of the relevant documentation and data to military agencies of our choise (sic), including all personal data of employees.
Threatpost has reached out for comments from the DOE. A spokesperson for the DOE declined to comment to Mother Jones. The news outlet also reached out to a spokesperson for the FBI’s Albuquerque Field Office, who refused to either confirm or deny that the agency was investigating the matter.
The ‘Relentless’ REvil
It wouldn’t be surprising if initial reports of REvil being responsible prove accurate. The RaaS group’s ambitions are apparently boundless. Earlier this week, an official of JBS Foods confirmed that the company paid the equivalent of $11 million in ransom after a cyberattack that forced the company to shut down some operations in the United States and Australia over the Memorial Day weekend.
REvil is known for both audacious attacks on the world’s biggest organizations and suitably astronomical ransoms. In April, it put the squeeze on Apple just hours before its splashy new product launch, demanding a whopping $50 million extortion fee: a bold move, even for the notorious ransomware-as-a-service (RaaS) gang. The original attack was launched against Quanta, a Global Fortune 500 manufacturer of electronics, which claims Apple among its customers. The Taiwanese-based company was contracted to assemble Apple products, including Apple Watch, Apple Macbook Air and Pro, and ThinkPad, from an Apple-provided set of design schematics.
FireEye researchers have also reported that the actors who’ve claimed to have access to the SolarWinds network have included one with links to the REvil/Sodinokibi ransomware gang, though that doesn’t necessarily make it true.
REvil’s reported chiding begs the question: Although it’s unclear what data the attackers managed to access, if we take the gang’s words at face value that it stole what it claims to have stolen, then what “necessary action” to protect employees’ purportedly compromised personal data and software development information could Sol Oriens have done to fend off this attack?
The answer, unfortunately, is probably as varied as the group’s relentlessness, persistence and whatever-it-takes tactics. On Friday, cybersecurity firm Sophos issued a report detailing how, as the firm puts it, “No two criminal groups deploy the [RaaS] … in exactly the same way.”
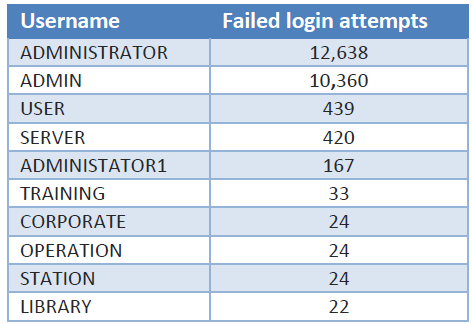
In one recent attack, for example, the targeted organization “logged a massive volume of failed inbound RDP login attempts targeting the server which eventually because a point of access for the attackers,” Sophos researchers wrote. “On a typical server, the log that stores failed attempts to login to services like RDP rolls over, overwriting the oldest data, over a period of from several days to weeks depending on how many failed attempts were made. In this attack, the volume of failed RDP login events caused the log files to completely overwrite themselves with new entries every five minutes. The data collected from that server showed approximately 35,000 failed login attempts over a five minute period, originating from 349 unique IP addresses around the world.”
Among the 35,000 brute-force login attempts made every five minutes, these were the most common usernames the attackers tried to use. Source: Sophos
The researchers noted that RDP “was implicated as one of the most common methods of breaching a network in cases we were called in to investigate, which is why shutting off the outside world’s access to RDP is one of the most effective defenses an IT admin can take.”
Unfortunately, defense isn’t as simple as shutting off RDP, given the variability of techniques used by the gang’s affiliates, they wrote. “RDP was not the only culprit: attackers also gained initial access through other internet-facing services they were able to brute-force or to launch an exploit against a known vulnerability that gave them some access. In one case, the attacker targeted a bug in a specific VPN server software to gain initial access, then exploited a bug on a five-year-old version of Apache Tomcat on the same server that let the attacker create a new admin account on the server.”
Consequences for Bold, Dangerous Cyberattacks?
David Bishop, CISO of global managed security services company Trustwave, opined that we need “more serious repercussions” for this type of attack. “We’re seeing advanced adversaries getting much bolder with who they are attacking, how they are blackmailing the targeted organization, and how they are monetizing their stolen goods,” he told Threatpost in an email on Friday.
“Most of these organized groups are financially motivated, but if these types of attackers shift their motivation from monetary to malicious, we should expect severe real-world outcomes.,” Bishop continued. “We’ve only seen the tip of the iceberg in terms of the real-world effects with the cyber-attacks on JBS and Colonial Pipeline. The public and private sectors need to closely coordinate on what we can accomplish in terms of hard legal or offensive action to combat these threats – otherwise, these adversaries will continue to attack at will.”
Download our exclusive FREE Threatpost Insider eBook, “2021: The Evolution of Ransomware,” to help hone your cyber-defense strategies against this growing scourge. We go beyond the status quo to uncover what’s next for ransomware and the related emerging risks. Get the whole story and DOWNLOAD the eBook now – on us!
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·