BOOK THIS SPACE FOR AD
ARTICLE AD
About the Program:
The program is a platform for connecting students,teachers and parents.Each of them have an unique domain.The teachers can connect a student and their parents into their class by use of code or invitation.The privilege is as follows Teachers > Parents > Students.The Vulnerability:
So There is an Chat functionality to develop an conversation between Teachers and parents.I tried to abuse the message box with XSS and as per my initial analysis everything were filtered.I Tried with both end as a teacher and as a parent ! no Luck!,Everything were encoded.Then i found teacher has an option to download the message history,I intercepted the request and to my shocking i found out the payloads in the messages were not stripped.
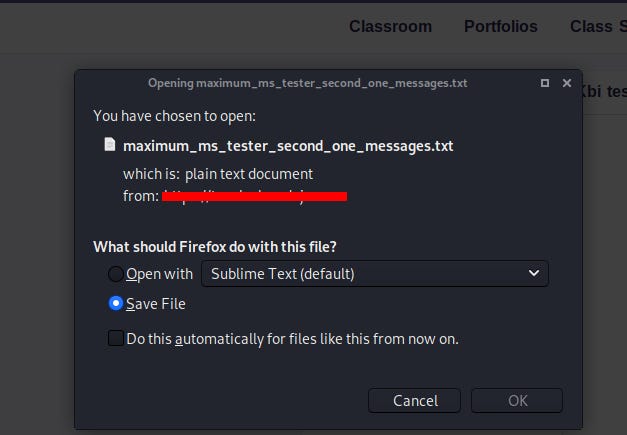


Reflected File Download(RFD) is an attack technique which might enables attacker to gain complete access over a victim’s machine by virtually downloading a file from a trusted domain.This web attack technique has been discovered by Oren Hafif, a Trustwave SpiderLabs security researcher in 2014.
But our vulnerability is not a classic RFD,If it is,It will be closed as P5 by Bugcrowd.Confirmation:
So now i need to confirm the issue and asked Robert bro(Great advisor of mine) to reproduce the issue in his browser and he said it was not working and the quotes were filtered by underscores in his browser.
Clearly there’s a bug on that site: they should not allow filenames with quotes and then not escape them. My concern here is that browser behavior difference could contribute to cases where sites get into trouble and then just blame Firefox, leaving our users unprotected. We have made exceptions to strict content-disposition parsing in the past, it might be worth figuring out what heuristic other browsers are using here.
So i thought it was a bug that can be exploited in older browsers and i know that bugcrowd ASE wont be able to reproduce it.So again played around and found something“; is the universal bypass and now the quotes were not converted into underscores in browsers when it reaches the delimiter.But How?

Attack scenario
The parent and teacher were the attacker and victim respectively.The parent send the payload calc.exe and delete’s it(to make the teacher less suspicious).
Report Timeline:
Reported - 03 Feb 2021Bounty awarded -28 Apr 2021Resolved -13 May 2021
Instagram- https://www.instagram.com/username_.not._available/
.png)
 3 years ago
877
3 years ago
877 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·