BOOK THIS SPACE FOR AD
ARTICLE ADIt may come as a surprise to absolutely nobody that experts say, in revealing the most prevalent and likely tactics to meddle with elections this year, that state-sponsored cybercriminals pose the biggest threat.
The election to decide the next US president will take place in November this year and while the UK government could delay its next general election until January 28, 2025, it's also expected to take place towards the back end of 2024.
As leaders of major international powers, both of these elections are likely to be targeted by foreign adversaries, and according to security giant Mandiant's latest report on election security trends, defenders should be aware of the four Ds.
DDoS attacks, data theft and leaks, disinformation, and deepfakes lead the way as the most likely types of attacks to be trialed during this year's elections, researchers say, all of which have the potential to impact voter outcomes.
It's likely, however, that different attack types will be used together in multi-layered hybrid attacks – Russia's state sponsored attackers are especially fond of this approach – which would potentially increase the severity of the impact on an election.
For example, data theft and leak operations, carried out after infiltrating the network of an organization such as a political party – a hybrid approach – could potentially influence voters toward whichever party favors the nation responsible. And the risk of these taking place prior to major elections this year is believed to be high.
Mandiant assesses that election attacks would most likely be carried out to target campaigns and voters, which encompass news outlets, political parties, social media platforms, and donor groups.
The likelihood of attacks on electoral registers or voting machines, for example, is thought to be significantly lower, although successful attempts to disrupt these (as opposed to lies about them being compromised) would lead to more impactful outcomes.
Speaking of lies, disinformation spread via fake news brands and other channels, which is then amplified by voracious shares across social media, is another high-risk, high-likelihood example of election meddling for 2024.
Russia has a pedigree in this area. Shortly before its invasion of Ukraine in 2022, financial services companies were hit by DDoS attacks and citizens then received SMS texts informing them that the country's ATMs were down, which was a lie to sow panic. These hybrid efforts were attributed to Russia's spy agency (GRU) by both the US and UK.
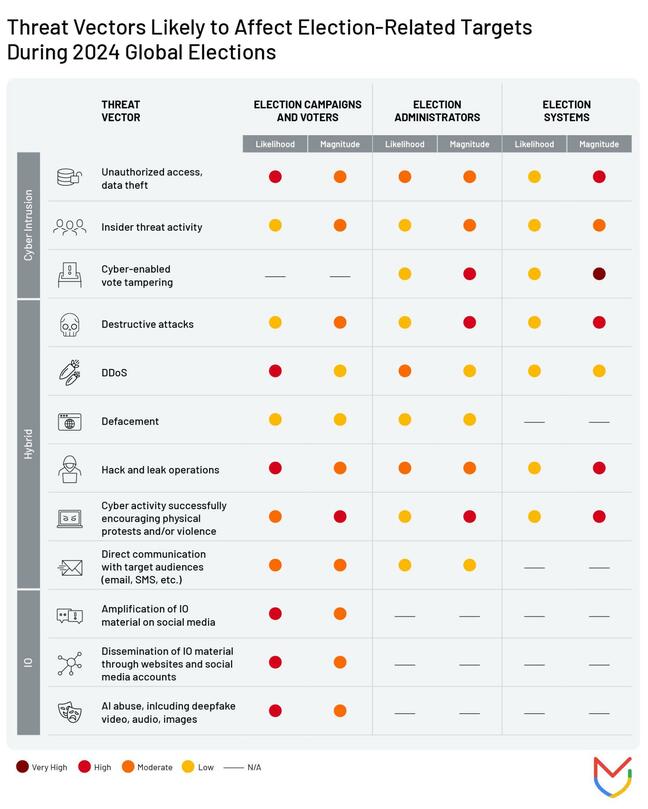
The different election attack types and the threat they present (courtesy of Mandiant)
The use of deepfake technology in cyberattacks, in one way or another, has been around for years now, but only in the past 12 months has the threat started to become more convincing. So much so, in fact, that Mandiant says it's just as likely to take place during elections as data leaks and could cause a similar degree of damage.
Pro-China cyber groups have been observed by Mandiant using deepfake technology to create viral social media clips of celebrities criticizing politicians.
In one recent case on TikTok, everyone's favorite bedtime story voicer Morgan Freeman was the subject of deepfake tech in a video that appeared to show him disagreeing with current US president Joe Biden.
"We are facing a multitude of election cyberthreats. Several actors are emboldened and interested in interfering in the democratic process," said John Hultquist, Mandiant chief analyst at Google Cloud. "Cyber espionage, information operations, and hacktivism will all be in play to some degree.
"Actors who have previously targeted elections, like those tied to Russian military intelligence and Iran's Islamic Revolutionary Guard Corps remain the boldest and most aggressive actors that Mandiant tracks. While they are constantly adapting their techniques, many of their operations follow a familiar formula: attacks with limited practical effects are exaggerated for maximum psychological impact. We will have to strike a balance between preparing for these threats while also being careful not to exaggerate their impacts.
"This isn't 2016. Though there are more actors in play, many are struggling to build and maintain influence in an environment where their operations are regularly identified and removed."
The key players
There are also no surprises about who the main suspects are when it comes to election meddling, and all of the big four adversaries to the UK aren't thought to be strangers to such activity, even in their own borders.
That's right, criminals in the employ of Russia, China, Iran, and North Korea – as usual – are the most common attackers that election defenders deal with, Mandiant says.
Russia has the highest number of groups supporting its cause, either via state sponsorship or hacktivist ideals. Groups including Sandworm and COLDRIVER have been linked with a swathe of election influences over the years, including with Brexit.
Given the number of groups working on its behalf, Russian attacks will likely span the gamut of what's possible and will be directed across the various elections in Europe this year, Jamie Collier, Mandiant senior threat intelligence advisor EMEA at Google Cloud, noted.
"Russia remains the most serious threat to Europe in the runup to the European Parliament elections. Russian operations will likely take place across Europe and attempt to undermine support for Ukraine, NATO, and the EU. Russia-nexus groups, such as APT44, have a track record of combining espionage campaigns, destructive operations, and spreading disinformation.
Microsoft warns that China is using AI to stir the pot ahead of US election Ukraine hit by DDoS attacks, Russia deploys malware All the US midterm-related lies to expect when you're electing Kremlin's Sandworm blamed for cyberattacks on US, European water utilities"This means Europe must not only prepare for a variety of cyber risks, but also understand how they come together. Hack and leak operations are one example of this in action: sensitive information stolen through a network intrusion boosts the effectiveness of subsequent information operations that can leverage authentic documents to maximize societal disruption."
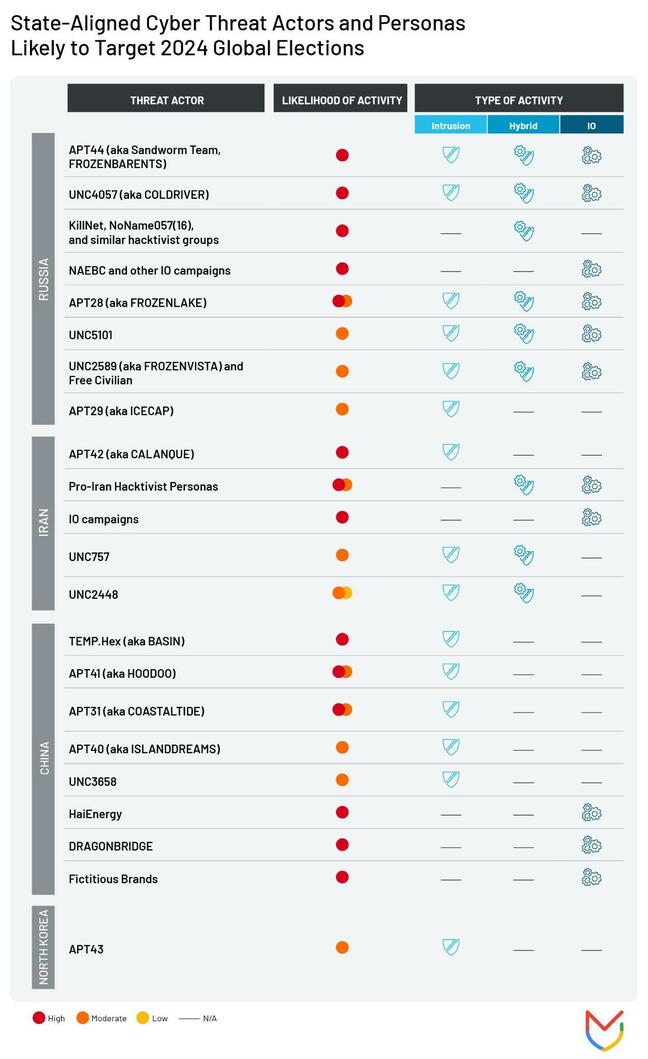
The different nations and the groups that further their causes (image courtesy Mandiant)
China also has a large number of groups supporting its objectives, but Mandiant believes these are limited to one kind of activity each. One might focus only on data theft, while another's attention lies solely on information operations, whereas some Russian groups have the capability to do all of what's possible and combine them in a single campaign.
As Hultquist said, Iran has a history of success in targeting elections and shouldn't be underestimated, while North Korea might be in and around the mix but likely won't pose anywhere near as substantial a threat as the others.
Mandiant said that while efforts to undermine elections will take place, what's less certain is the degree to which they'll be effective.
Defenders have become more wary, more skilled, and more in tune with what to expect from foreign powers, which means they've become adept at combatting their campaigns.
Citizens of countries whose elections have been targeted by adversaries are also more aware of the threat to elections and are more vigilant to disinformation campaigns, having been exposed to them for years now. ®
.png)
 7 months ago
46
7 months ago
46 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·