Russian threat actors capitalized on the ongoing conflict against Ukraine to distribute Android malware camouflaged as an app for pro-Ukrainian hacktivists to launch distributed denial-of-service (DDoS) attacks against Russian sites.
Google Threat Analysis Group (TAG) attributed the malware to Turla, an advanced persistent threat also known as Krypton, Venomous Bear, Waterbug, and Uroburos, and linked to Russia's Federal Security Service (FSB).
"This is the first known instance of Turla distributing Android-related malware," TAG researcher Billy Leonard said. "The apps were not distributed through the Google Play Store, but hosted on a domain controlled by the actor and disseminated via links on third party messaging services."
It's worth noting that the onslaught of cyberattacks in the immediate aftermath of Russia's unprovoked invasion of Ukraine prompted the latter to form an IT Army to stage counter-DDoS attacks against Russian websites. The goal of the Turla operation, it appears, is to use this volunteer-run effort to their own advantage.
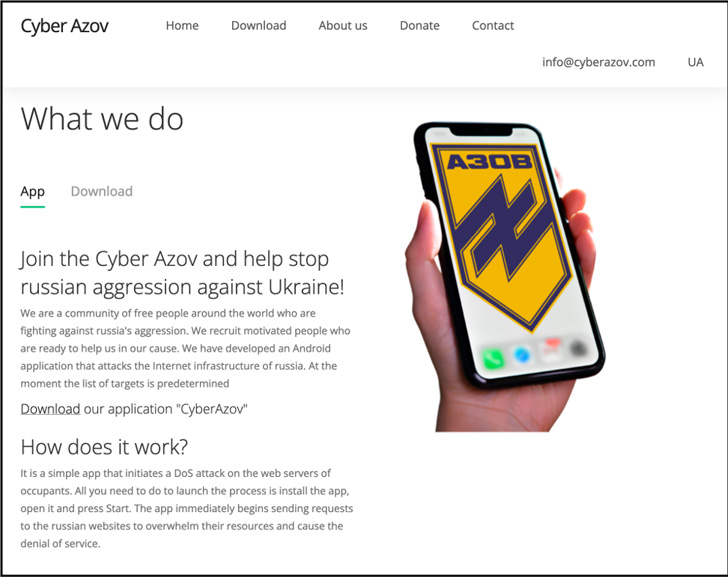
The decoy app was hosted on a domain masquerading as the Azov Regiment, a unit of the National Guard of Ukraine, calling on people from around the world to fight "Russia's aggression" by initiating a denial-of-service attack on the web servers belonging to "Russian websites to overwhelm their resources."
Google TAG said the actors drew inspiration from another Android app distributed through a website named "stopwar[.]pro" that's also designed to conduct DoS attacks by continually sending requests to the target websites.
That said, the actual number of times the malicious Cyber Azov app was installed is minuscule, posing no major impact on Android users.
Additionally, the Sandworm group (aka Voodoo Bear) has been connected to a separate set of malicious activities leveraging the Follina vulnerability (CVE-2022-30190) in the Microsoft Windows Support Diagnostic Tool (MSDT) to send links pointing to Microsoft Office documents hosted on compromised websites targeting media entities in Ukraine.
UAC-0098, a threat actor that CERT-UA last month warned of distributing tax-themed documents carrying a Follina exploit, has also been assessed to be a former initial access broker with ties to the Conti group and in charge of disseminating the IcedID banking trojan.
Other kinds of cyber activity include credential phishing attacks mounted by an adversary referred to as COLDRIVER (aka Callisto) aimed at government and defense officials, politicians, NGOs and think tanks, and journalists.
These involve sending emails either directly, including the phishing domain or containing links to documents hosted on Google Drive and Microsoft OneDrive that, in turn, feature links to an attacker-controlled website designed to steal passwords.
The latest developments are yet another indication of how Russian threat actors are exhibiting continued signs of increasing sophistication in their attempts to target in ways that highlight their evolving techniques.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
149
2 years ago
149 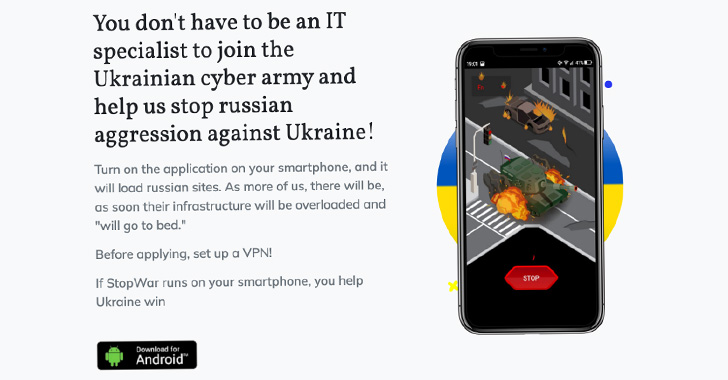

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·