A group of academics from the University of California, Santa Barbara, has demonstrated what it calls a "scalable technique" to vet smart contracts and mitigate state-inconsistency bugs, discovering 47 zero-day vulnerabilities on the Ethereum blockchain in the process.
Smart contracts are programs stored on the blockchain that are automatically executed when predetermined conditions are met based on the encoded terms of the agreement. They allow trusted transactions and agreements to be carried out between anonymous parties without the need for a central authority.
In other words, the code itself is meant to be the final arbiter of "the deal" it represents, with the program controlling all aspects of the execution, and providing an immutable evidentiary audit trail of transactions that are both trackable and irreversible.
This also means that vulnerabilities in the code could result in hefty losses, as evidenced by hacks aimed at the DAO and more recently, MonoX, where adversaries exploited loopholes to illicitly siphon funds, a scenario that could have catastrophic consequences given the burgeoning adoption of smart contracts over the past few years.
"Since smart contracts are not easily upgradable, auditing the contract's source pre-deployment, and deploying a bug-free contract is even more important than in the case of traditional software," the researchers detailed in a paper.
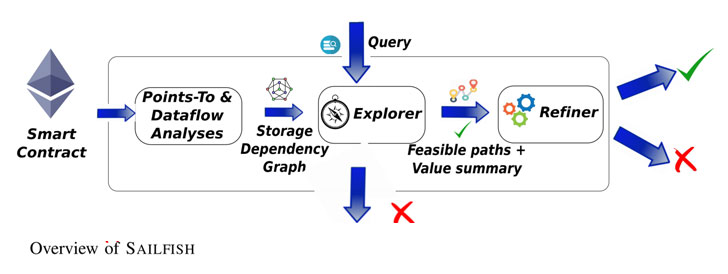
Enter Sailfish, which aims to catch state inconsistency vulnerabilities in smart contracts that allow an attacker to tamper with the execution order of the transactions or take over the control flow within a single transaction (i.e., reentrancy).
The tool works as follows. Given a smart contract, Sailfish converts the contract into a dependency graph, which captures the control and data flow relations between the storage variables and the state-changing instructions of a smart contract, using it identify potential flaws by defining hazardous access, which are implemented as graph queries to determine whether two different execution paths, at least one being a write operation, operate on the same storage variable.
The researchers evaluated Sailfish on 89,853 contracts obtained from Etherscan, identifying 47 zero-day flaws that could be leveraged to drain Ether and even corrupt application-specific metadata. This also includes a vulnerable contract implementing a housing tracker that could be abused in a manner such that a house owner can have more than one active listing.
The findings of the study will be shared at the IEEE Symposium on Security and Privacy (S&P) to be held in May 2022.
This is not the first time problematic smart contracts have attracted attention from academia. In September 2020, Chinese researchers designed a framework for categorizing known weaknesses in smart contracts with the goal of providing a detection criterion for each of the bugs.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
141
2 years ago
141 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·