BOOK THIS SPACE FOR AD
ARTICLE ADSality is a well known family of file-infectors (or PE-infectors or just a viruses). And as malware it has a very long story of evolution since 2003. Latest it versions contain rootkit on board to complicate detection from side of AV-scanners.
Driver has such features:
Processes termination via NtTerminateProcess;Blocking access to some AV web-resources via IP Filtering;Small size ~ 5 KB.According analysis, rootkit is targeted to Windows starting NT4 and finishing Vista. It should be said in advance that this rootkit is not a NEW and not contains some features which have modern rootkits or bootkits. Researched version of rootkit has appeared ITW since beginning of 2010.
Rootkit creates device with name:
\Device\amsint32
\DosDevices\amsint32
and this is signal to infection.
Rootkit contains usual most famous way of process killing, which is used by almost all "old-school" rootkits.
Sality uses old model of IP filtering for blocking access to web-resources that belong AV-vendors. This technique is called IP Filtering. More info: Windows 2000 Filter-Hook Driver example http://ntdev.h1.ru/ipfilter.html and MSDN http://msdn.microsoft.com/en-us/library/windows/hardware/ff548976(v=vs.85).aspx.
List of affected vendors:
This feature requires from driver to registering a callback function which will be called for IP-packets. This function will decide what to do with the packet: to forward it or drop.
Registered callback - fnFilterHookIP will looking for presence of AV-vendors strings in data of packet. In case of hit it forces IP-driver to drop this packet.
Encrypted AV vendors strings in it body:
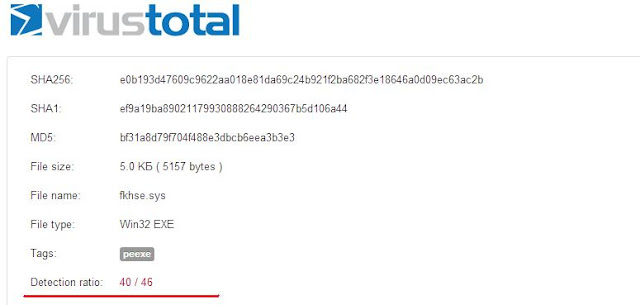
Detection ratio:
SHA256: e0b193d47609c9622aa018e81da69c24b921f2ba682f3e18646a0d09ec63ac2b
SHA1: ef9a19ba89021179930888264290367b5d106a44
MD5: bf31a8d79f704f488e3dbcb6eea3b3e3
File size: 5157 bytes
posted by https://twitter.com/artem_i_baranov
.png)






















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·