BOOK THIS SPACE FOR AD
ARTICLE AD
On the second day of Pwn2Own Ireland 2024, competing white hat hackers showcased an impressive 51 zero-day vulnerabilities, earning a total of $358,625 in cash prizes.
Pwn2Own is a hacking contest where security researchers compete to exploit software and mobile hardware devices to earn the coveted title of "Master of Pwn" and $1,000,000 in cash and prizes.
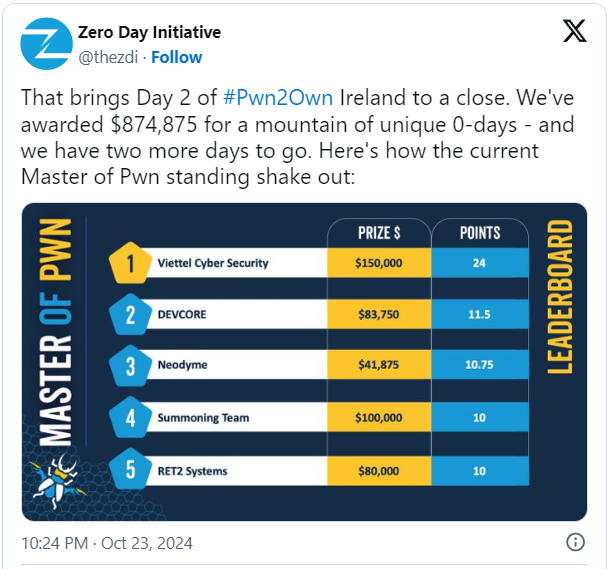
On day 2 of Pwn2Own, the Viettel Cyber Security team maintained a strong lead in the race for the "Master of Pwn" title, with standout performances across several categories.
Pham Tuan Son and ExLuck from ANHTUD kicked off the day by exploiting a Canon imageCLASS MF656Cdw printer using a stack-based buffer overflow, securing $10,000 and 2 Master of Pwn points.
Ken Gannon from NCC Group chained five bugs, including a path traversal, to exploit the Samsung Galaxy S24, gaining a $50,000 payout and 5 points. His exploit allowed him to install an app and gain shell access to the popular Android device.
Dungdm from Viettel Cyber Security took control of a Sonos Era 300 smart speaker using a Use-After-Free (UAF) vulnerability. His successful exploit added $30,000 to his team's earnings and 6 Master of Pwn points.
Team Cluck's duo Chris Anastasio and Fabius Watson chained two vulnerabilities, including a CRLF injection, to compromise the QNAP TS-464 NAS, earning $20,000 and 4 points in the process.
Corentin BAYET of Reverse Tactics earned $41,750 and 8.5 points despite one of the three bugs in his chain being a repeat from earlier rounds while targeting the QNAP QHora-322 router.
Collisions and fails
Day 2 also had several collisions, meaning the same exploit was used by other researchers, as well as unsuccessful attempts to hack the devices in the allotted time.
Tenable and Synactiv received reduced payouts and fewer points due to collisions when hacking the Lorex 2K and Synology BeeStation devices, respectively.
Also, DEVCORE, Rapid7, and Neodyme encountered difficulties in executing their exploits within the time limits, resulting in several failed attempts across devices like the Sonos Era 300 and Lexmark CX331adwe printer.
Despite the setbacks, the Pwn2Own competition remains intense, only having reached halfway, with two days remaining for participants to climb higher in the rankings.
At this point, researchers have exploited a total of 103 zero-day vulnerabilities, 52 on day one, and earned $847,875 in prizes.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·