BOOK THIS SPACE FOR AD
ARTICLE ADWe’ve uncovered a malicious campaign going after Mac users looking for support or extended warranty from Apple via the AppleCare+ support plans. The perpetrators are buying Google ads to lure in their victims and redirect them to bogus pages hosted on GitHub, the developer and code repository platform owned by Microsoft.
The goal of this scam is to get unsuspecting people on the phone with someone pretending to be working for Apple. From there, fraudulent call center agents will social engineer their victims in order to extract money from them.
In this blog post, we expose the techniques behind this scam and provide mitigation steps to stay away from them. We’d like to thank GitHub for their quick response in taking down the malicious accounts we reported to them.
Hey Siri, google “Apple phone support”
While Apple products are designed with simplicity in mind, we’ve all come across an issue at some point that we need assistance with. Google, who reportedly paid Apple $20 billion to be the default search engine, will display results in Safari, along with ads, hence the lucrative partnership.
Those “Sponsored” results can appear at the top or further down the search results page. In the image seen below, a malicious ad appears at the very top, right before Apple’s official phone number. In other cases we encountered, multiple malicious ads were displayed before any legitimate results.
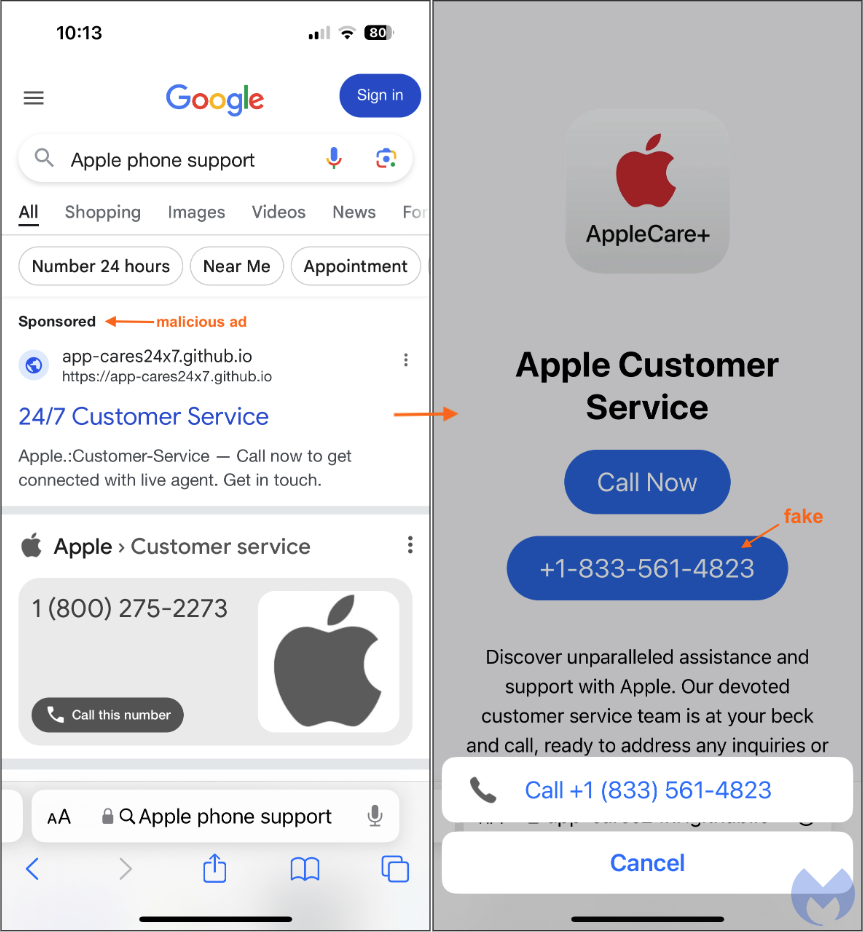
Clicking on one of those will redirect to a fake AppleCare+ customer service page, inviting users to call a 1-800 phone number supposedly belonging to Apple. In reality, in just 2 simple clicks victims are connected with scammers located in call centers overseas.
GitHub repos
The fake Apple customer service pages are hosted on Microsoft’s GitHub source code repository as standalone HTML templates using Apple’s branding. Scammers are creating several accounts on GitHub with one or multiple repositories with the same fraudulent index.html template:
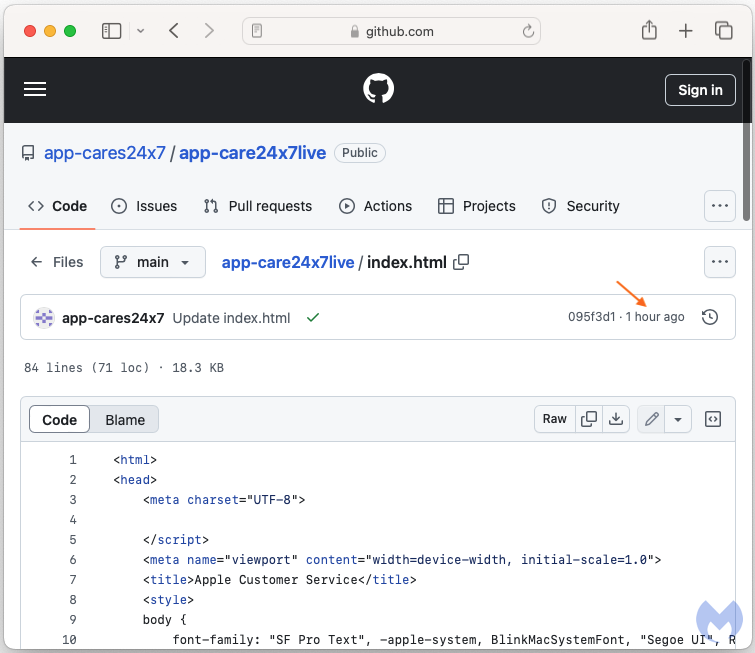
During an active campaign, they can easily swap phone numbers in case one got reported and blocked. In fact, we saw scammers do just that thanks to GitHub’s commit history:

There is also an interesting piece of code within the page (autoDial) that automatically pops up the phone dialog menu. This ensures that victims have one less thing to click on to get connected with a scammer impersonating Apple:

Risks and mitigations
This particular scheme is exceptionally easy to fall for due to the combination of malicious Google ads and lookalike pages. Scammers are preying on unsuspecting users to trust that they are real Apple service agents and that it’s okay to give them personal information.
The biggest risk to consumers is being defrauded for hundreds, and often thousands of dollars. Scammers typically instruct victims to withdraw money from their bank account and send it to them, in various ways.
In some cases we investigated this year, fraudsters will ask for the victim’s name, address, social security number and banking details. With that information, they can easily blackmail them directly or share their profile with other scammers who will pretend to help from the original incident.
We advise users to be extremely cautious when looking for phone or online support related to any of the most popular brands. Microsoft is usually highly targeted by scammers due to its dominance in the computer market share. Keep in mind that whenever you click on a sponsored result or ad, you are taking a chance of being redirected to a malicious site.
If you want to find out what personal data of yours has been exposed online, you can use our free Digital Footprint scan. Fill in the email address you’re curious about (it’s best to submit the one you most frequently use) and we’ll send you a free report.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·