BOOK THIS SPACE FOR AD
ARTICLE AD
Scammers are sending fake replacement devices to Ledger customers exposed in a recent data breach that are used to steal cryptocurrency wallets.
Ledger has been a popular target by scammers lately with rising cryptocurrency prices and the popularity of hardware wallets to secure cryptofunds.
In a post on Reddit, a Ledger user shared a devious scam after receiving what looks like a Ledger Nano X device in the mail.
As you can see from the pictures below, the device came in an authentic looking packaging, with a poorly written letter explaining that the device was sent to replace their existing one as their customer information was leaked online on the RaidForum hacking forum.
"For this reason for security purposes, we have sent you a new device you must switch to a new device to stay safe. There is a manual inside your new box you can read that to learn how to set up your new device," read the fake letter from Ledger.
"For this reason, we have changed our device structure. We now guarantee that this kinda breach will never happen again."
Even though the letter was filled with grammatical and spelling errors, the data for 272,853 people who purchased a Ledger device was actually published on the RaidForums hacking forum in December 2020. This made for a slightly convincing explanation for the sending of the new device.
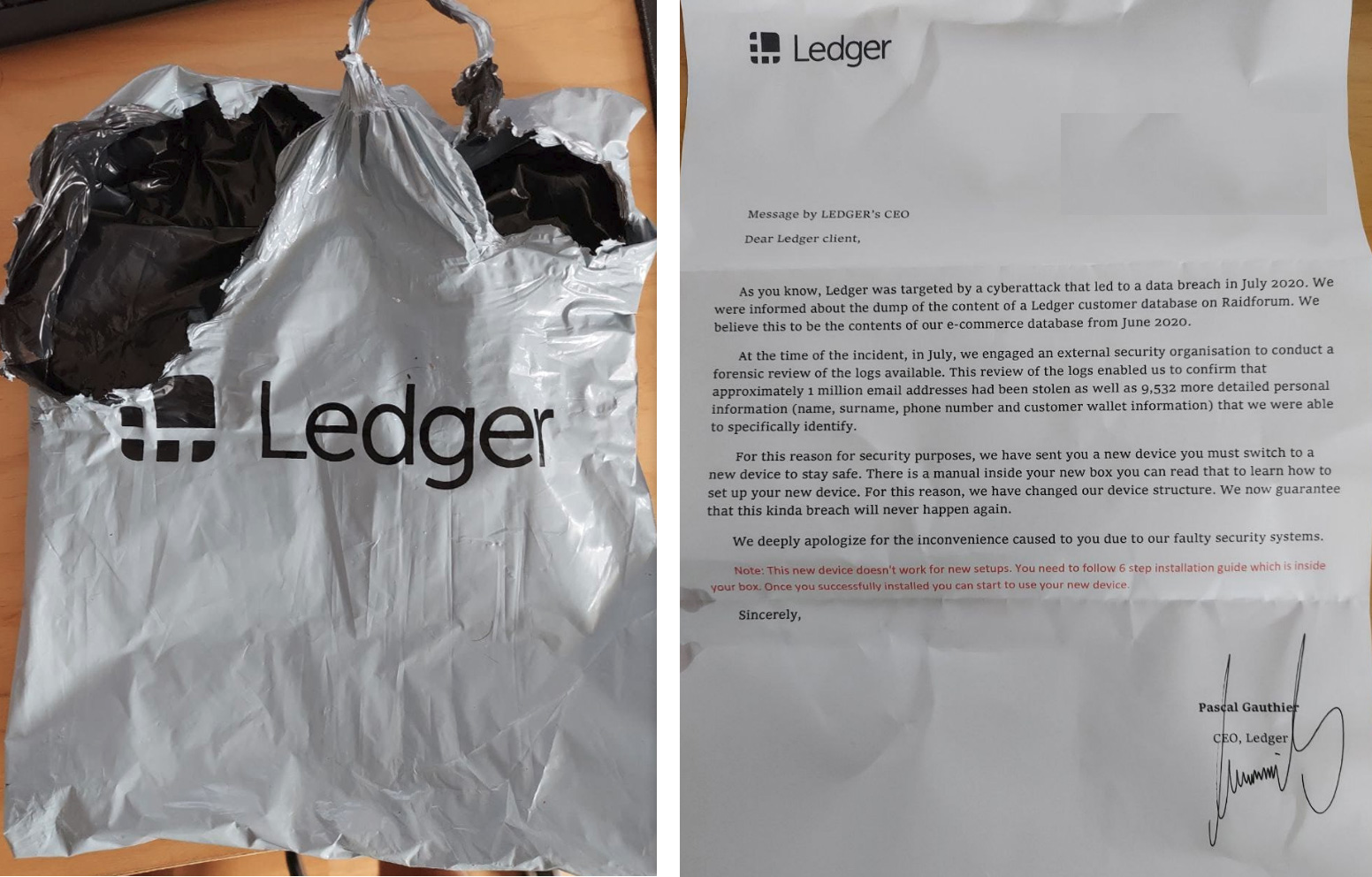 Packaging and letter for the fake Ledger device
Packaging and letter for the fake Ledger deviceSource: Reddit
Also enclosed in the package was a shrinkwrapped Ledger Nano X box that contained what appeared to be a legitimate device.
 Enclosed shrinkwrapped Ledger device
Enclosed shrinkwrapped Ledger deviceSource: Reddit
After becoming suspicious of the device, they opened it and shared pictures of the Ledger's printed circuit board on Reddit that clearly show the device was modified.
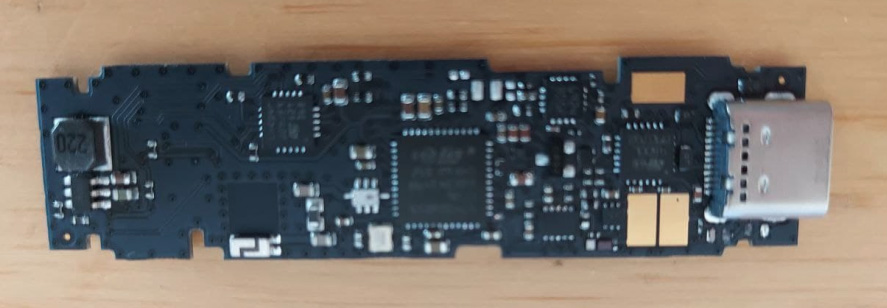 Front of fake Ledger hardware wallet
Front of fake Ledger hardware walletSource: Reddit
Based on the photos, security researcher and offensive USB cable/implant expert Mike Grover, aka _MG_, told BleepingComputer that the threat actors added a flash drive and wired it to the USB connector.
"This seems to be a simply flash drive strapped on to the Ledger with the purpose to be for some sort of malware delivery," Grover told BleepingComputer in a chat about the photos.
"All of the components are on the other side, so I can't confirm if it is JUST a storage device, but.... judging by the very novice soldering work, it's probably just an off the shelf mini flash drive removed from its casing."
In the image below, Grover highlighted the flash drive implant connected to the wires while stating. "Those 4 wires piggyback the same connections for USB port of the Ledger."
 Back of fake Ledger hardware wallet
Back of fake Ledger hardware walletSource: Reddit
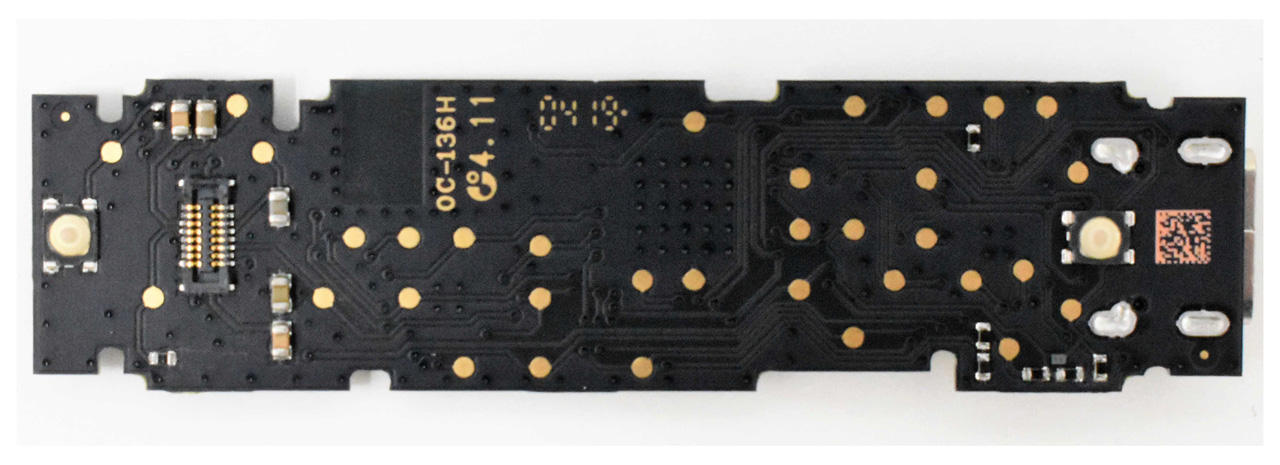 Back of real Ledger hardware wallet
Back of real Ledger hardware walletSource: Ledger
The enclosed instructions tell the person to connect the Ledger to their computer, open a drive that appears, and run the enclosed application.
The instructions then tell the person to enter their Ledger recovery phrase to import their wallet to the new device.
 Fake Ledger instructions explaining how to transfer wallet to new device
Fake Ledger instructions explaining how to transfer wallet to new deviceSource: Reddit
A recovery phrase is a human-readable seed used to generate the private key for a specific wallet. Anyone who has this recovery phrase can import a wallet and access the cryptocurrency it contains.
After entering the recovery phrase, it is sent to the attackers, who use it to import the victim's wallet on their own devices to steal the contained cryptocurrency funds.
Ledger is aware of this scam and has posted warnings about it in May on their dedicated phishing page.
As always, Ledger recovery phrases should never be shared with anyone and should only be entered directly on the Ledger device you are trying to recover. If the device does not provide the ability to enter the phrase directly, you should only use the Ledger Live application downloaded directly from Ledger.com.
In 2018, security researchers illustrated various methods that could be used to compromise hardware cryptocurrency wallets, including the Trezor One, Ledger Nano S, and Ledger Blue devices.
.png)
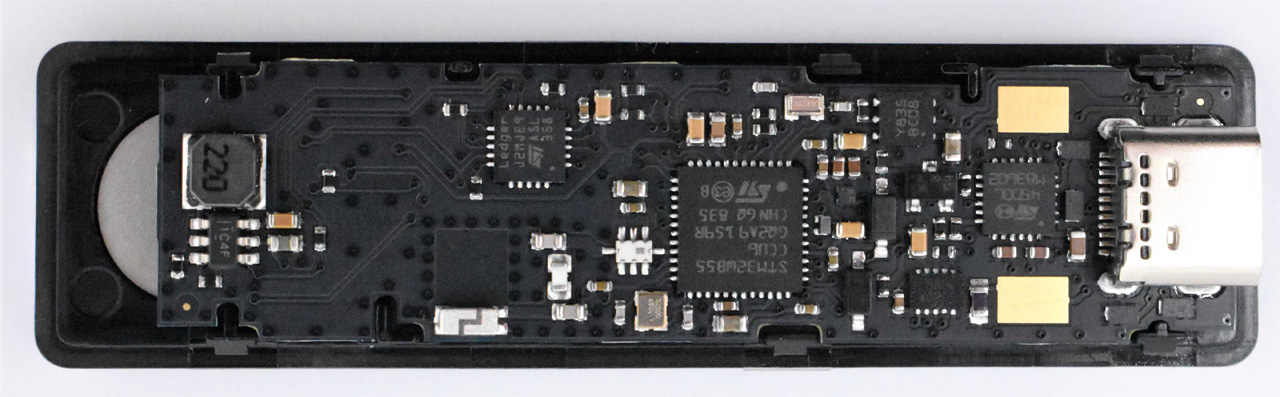 Front of real Ledger hardware wallet
Front of real Ledger hardware wallet














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·