 |
| Image credit: Adaptive Shield |
As security professionals who have spent more than a few years in the industry, we know a good challenge when we see one.
SaaS and cloud-based technologies are growing rapidly, offering organizations convenience and constant feature refreshes without the need to install and deploy software on-premises.
However, even when referred to as 'a game-changer,' many organizations are still highly concerned by security breaches.
Today, organizations have anywhere from 35-to literally hundreds of SaaS applications running. Slack, Office 365, Zoom, Zendesk, Salesforce, Hubspot, etc.
These applications are at the core of modern enterprises, to the point where running a business without them would be nearly impossible, with the cost and time-saving benefits they provide enabling growth while conserving resources.
SaaS applications are easy to use, scalable, and now, they even come with an impressive array of native security controls to secure sensitive corporate data.
How to make the most of your SaaS security
Solving the SaaS Security Management Problem
SaaS application security is one of the growing concerns amongst startups and tech businesses, threatening them with their data being lost or stolen or reputation damaged.
The problem is that even with the built-in security controls, organizations still experience security breaches due to misconfigurations in their SaaS applications. With so many settings, controls, and policies to manage and track on these platforms, things fall through the cracks ALL THE TIME, resulting in huge security holes.
The thing is that ensuring SaaS applications are continuously configured properly is very tedious, and you need to know what you're doing across tons of different applications.
Any business-critical SaaS platform has dozens of additional security and user-related settings; do the math, and you'll quickly see that trying to maintain them on your own is basically impossible.
Moreover, when you consider that applications like Salesforce have security guides that are hundreds of pages long and are continually being updated, it's clear that trying to prevent misconfigurations is a losing proposition.
A recent example of this; A global enterprise had a misconfiguration in a leading business software platform that enabled anonymous access to anyone, exposing full employee lists, emails, schedules, dashboards—leaving them wide open to potential threats.
Organizations have tried to address the issue with varying degrees of success over the years using different tools. For example, Cloud Access Security Brokers (CASBs) address security issues in SaaS applications.
But they are reactive, primarily focusing on the detection of breaches once they have occurred, which doesn't help proactively prevent misconfigurations in the first place. And Cloud Security Posture Management tools (CSPM) only address IaaS and PaaS Security use cases.
The other "approach," some organizations take, is that of doing nothing at all.
Automation Means Optimal SaaS Security
Without an automatic approach to maintaining security settings and controls, organizations don't stand a realistic chance of getting total control of their SaaS applications.
Trying to maintain consistent policies across all applications, understanding which applications involve which security features, and account for each one's specific methods is all just too complicated and time-consuming—and leaves room for mistakes.
Fortunately, the emerging category of SaaS Security Posture Management (SSPM) tools address this need, and Adaptive Shield is one best solution in this category that has been designed to enable optimal security posture automatically.
Adaptive Shield aims to address the critical issue of proactively maintaining continuous security for the myriad of SaaS applications used in organizations across the globe.
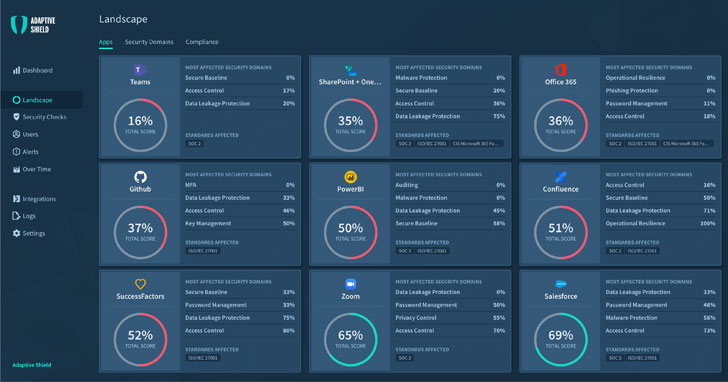 |
| Image credit: Adaptive Shield |
The team at Adaptive Shield does SaaS application security management adaptively across any type of SaaS application—including video conferencing platforms, customer support tools, HR management systems, dashboards and workspaces, content, and file-sharing applications, messaging applications, marketing platforms, and more.
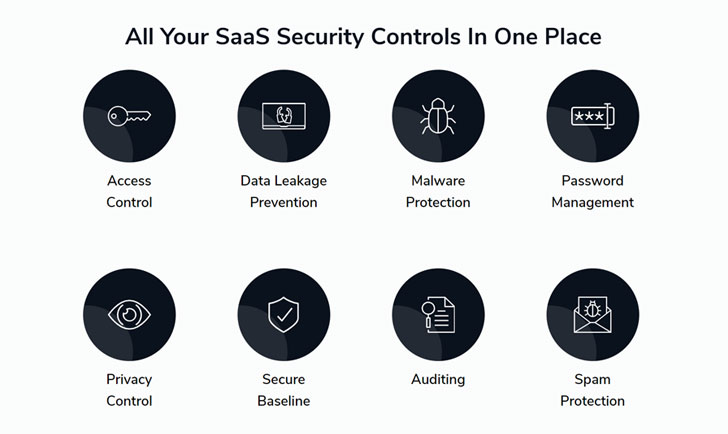 |
| Image credit: Adaptive Shield |
It assesses posture in a customized and automated manner, tailored to the specific circumstances of the application. And it's not just a one-time assessment; Once policies are set, they are continuously monitored and enforced.
Adaptive Shield:
Leverages built-in security settings/controls to discover all gaps and fix them automatically proactively. Continuously monitors global settings and user privileges to verify there are no breaches or drifts. Provides ongoing research and updates regarding all security-related settings and native controls for each SaaS platform covered, and embeds them effortlessly into the platform. Remediates any SaaS security issues from beginning to end. Displays all your SaaS security controls in one place to make management incredibly simple. It takes 5 minutes to deploy, and there's zero disruption to the business.Just like those little robotic vacuum cleaners that keep things consistently clean and free of dust without the need for oversight, Adaptive Shield extends continuous automatic hygiene across your SaaS applications.
Final Thoughts
According to Gartner, by 2025, nearly 99% of security failures in the cloud will be human-driven. And complex SaaS environments only serve to make circumstances more complicated.
The goal of Adaptive Shield is to remove the confusion and make SaaS security maintenance sustainable and straightforward, giving you the tools to protect your organization effortlessly.
Get started today and gain complete control for your SaaS security
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 4 years ago
184
4 years ago
184 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·