Cybersecurity researchers on Wednesday disclosed multiple security vulnerabilities impacting CODESYS automation software and the WAGO programmable logic controller (PLC) platform that could be remotely exploited to take control of a company's cloud operational technology (OT) infrastructure.
The flaws can be turned "into innovative attacks that could put threat actors in position to remotely control a company's cloud OT implementation, and threaten any industrial process managed from the cloud," the New York-headquartered industrial security company Claroty said in a report shared with The Hacker News, adding they "can be used to target a cloud-based management console from a compromised field device, or take over a company's cloud and attack PLCs and other devices to disrupt operations."
CODESYS is a development environment for programming controller applications, enabling easy configuration of PLCs in industrial control systems. WAGO PFC100/200 is a series of PLCs that make use of the CODESYS platform for programming and configuring the controllers.
The list of seven vulnerabilities is listed below -
CVE-2021-29238 (CVSS score: 8.0) - Cross-site request forgery in CODESYS Automation Server CVE-2021-29240 (CVSS score: 7.8) - Insufficient Verification of Data Authenticity in CODESYS Package Manager CVE-2021-29241 (CVSS score: 7.5) - Null pointer dereference in CODESYS V3 products containing the CmpGateway component CVE-2021-34569 (CVSS score: 10.0) - WAGO PFC diagnostic tools – Out-of-bounds write CVE-2021-34566 (CVSS score: 9.1) - WAGO PFC iocheckd service "I/O-Check" – Shared memory buffer overflow CVE-2021-34567 (CVSS score: 8.2) - WAGO PFC iocheckd service "I/O-Check" – Out-of-bounds read CVE-2021-34568 (CVSS score: 7.5) - WAGO PFC iocheckd service "I/O-Check" – Allocation of resources without limitsSuccessful exploitation of the flaws could enable the installation of malicious CODESYS packages, result in a denial-of-service (DoS) condition, or lead to privilege escalation via execution of malicious JavaScript code, and worse, manipulation or complete disruption of the device.
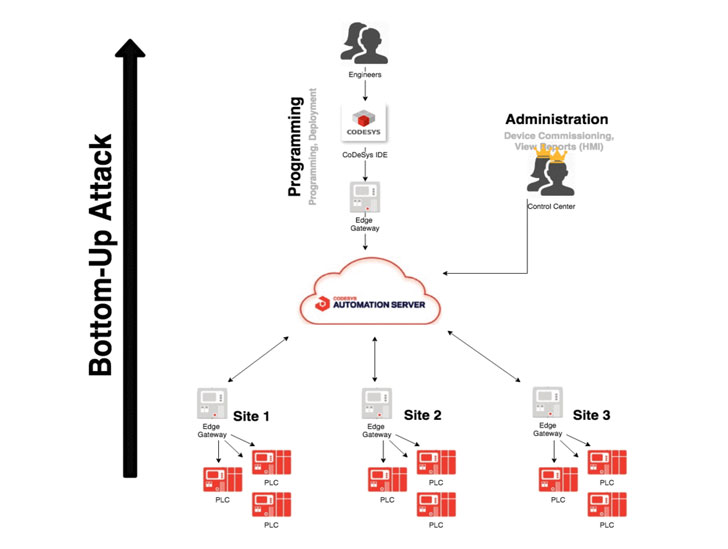
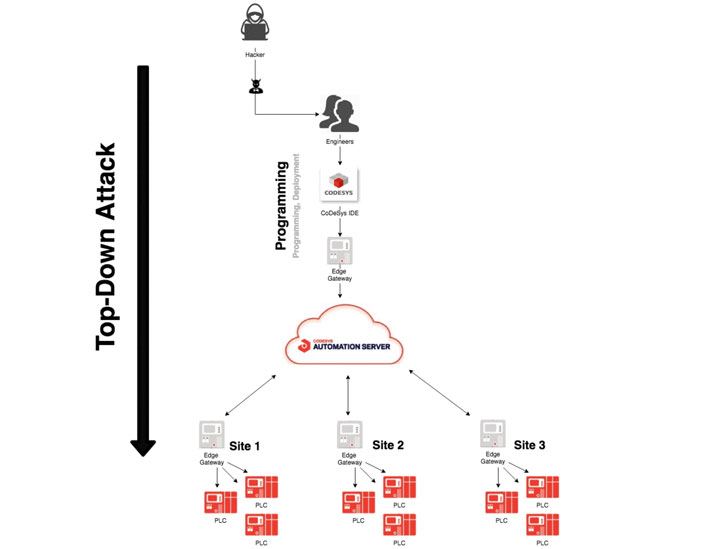
In the wild, this could play out in one of two ways: "bottom-up" or "top-down." The twin approaches mimic the paths an adversary is likely to take to either control a PLC endpoint in order to eventually compromise the cloud-based management console, or the reverse, commandeer the cloud in order to manipulate all networked field devices.
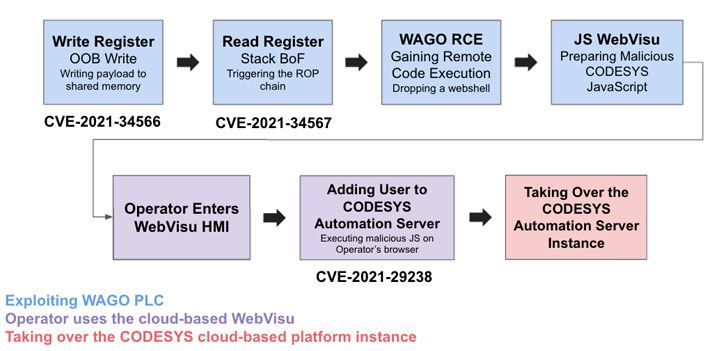
In a "bottom-up" complex exploit chain devised by Claroty, a mix of CVE-2021-34566, CVE-2021-34567, and CVE-2021-29238 were exploited to obtain remote code execution on the WAGO PLC, only to gain access to the CODESYS WebVisu human-machine interface and stage a cross-site request forgery (CSRF) attack to seize control of the CODESYS automation server instance.
"An attacker that obtains access to a PLC managed by the Automation Server Cloud can modify the 'webvisu.js' file and append JavaScript code to the end of the file that will send a malicious request to the cloud server on behalf of the logged in user," Claroty senior researcher Uri Katz, who discovered and reported the flaws, explained.
"When a cloud user views the WebVisu page, the modified JavaScript will exploit the lack of CSRF token and run in the context of the user viewing it; the request will include the CAS cookie. Attackers can use this to POST to '/api/db/User' with a new administrator user, giving them full access to the CODESYS cloud platform," Katz added.
An alternate "top-down" attack scenario, on the other hand, involves compromising the CODESYS engineering station by deploying a malicious package (CVE-2021-29240) that's designed to leak the cloud credentials associated with an operator account, and subsequently using it to tamper with the programmed logic and gain unfettered access to all the connected PLCs.
"Organizations moving forward with cloud-based management of OT and ICS devices must be aware of the inherent risks, and increased threats from attackers keen on targeting industrial enterprises with extortion-based attacks—including ransomware—and more sophisticated attacks that can cause physical damage," Katz said.
The disclosures mark the second time-critical flaws that have been uncovered in CODESYS and WAGO PLCs in as many months. In June, researchers from Positive Technologies revealed ten critical vulnerabilities in the software's web server and runtime system components that could be abused to gain remote code execution on the PLCs.
The development also comes a week after IoT security firm Armis disclosed a critical authentication bypass vulnerability affecting Schneider Electric Modicon PLCs — dubbed "ModiPwn" (CVE-2021-22779) — that could be exploited to allow full control over the PLC, including overwriting critical memory regions, leaking sensitive memory content, or invoking internal functions.
In a related report published earlier this May, Claroty made public a memory protection bypass vulnerability in Siemens SIMATIC S7-1200 and S7-1500 PLCs (CVE-2020-15782) that could be leveraged by a malicious actor to remotely gain access to protected areas of the memory and achieve unrestricted and undetected code execution.
The revelations also coincide with a joint cybersecurity advisory released by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) documenting a historical spear-phishing and intrusion campaign conducted by state-sponsored Chinese actors from December 2011 to 2013, targeting 23 oil and natural gas (ONG) pipeline operators in the country.
"CISA and the FBI assess that these actors were specifically targeting U.S. pipeline infrastructure for the purpose of holding U.S. pipeline infrastructure at risk," the agencies said. "Additionally, CISA and the FBI assess that this activity was ultimately intended to help China develop cyberattack capabilities against U.S. pipelines to physically damage pipelines or disrupt pipeline operations."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
308
3 years ago
308 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·