BOOK THIS SPACE FOR AD
ARTICLE AD
Phishing campaigns attributed to an advanced threat actor called SideWinder involved a fake VPN app for Android devices published on Google Play Store along with a custom tool that filters victims for better targeting.
SideWinder is an APT group that’s been active since at least 2012, believed to be an actor of Indian origin with a relatively high level of sophistication.
Security researchers at Kaspersky attributed close to 1,000 attacks to this group in the past two years. Among its primary targets are organizations in Pakistan, China, Nepal, and Afghanistan.
The adversary relies on a fairly large infrastructure with that includes more than 92 IP addresses, mainly for phishing attacks, hosting hundreds of domains and subdomains used as command and control servers.
 SideWinder APT group's infrastructure, source: Group-IB
SideWinder APT group's infrastructure, source: Group-IBA recent phishing campaign attributed to SideWinder (a.k.a. RattleSnake, Razor Tiger, T-APT-04, APT-C-17, Hardcore Nationalist) targeted organizations in Pakistan in both the public and private sector.
Researchers at cybersecurity company Group-IB earlier this year detected a phishing document luring victims with a document proposing “a formal discussion of the impact of US withdrawal from Afghanistan on maritime security.”
 Lure used by SideWinder APT group in phishing campaign, source: Group-IB
Lure used by SideWinder APT group in phishing campaign, source: Group-IBIn a report shared with BleepingComputer, Group-IB says that SideWinder has also been observed in the past cloning government website (e.g. government portal in Sri Lanka) to steal user credentials.
The recent phishing campaign also used this method against targets, as the actor set up multiple websites that mimicked legitimate domains of the Pakistani government:
finance.pakgov[.]net vpn.pakgov[.]net csd.pakgov[.]net hajj.pakgov[.]net nadra.pakgov[.]net pt.pakgov[.]net flix.pakgov[.]net covid.pakgov[.]netDuring the investigation, the researchers discovered a phishing link that redirected to the legitimate domain "securevpn.com." Its purpose remains unclear, but it could be to select targets of interest and redirect them to a malicious site.
Another link discovered by Group-IB downloaded from Google Play, the official Android app store, a fake version of the ‘Secure VPN’ app, which is still present on Google Play at the time of writing and has just over 10 downloads.
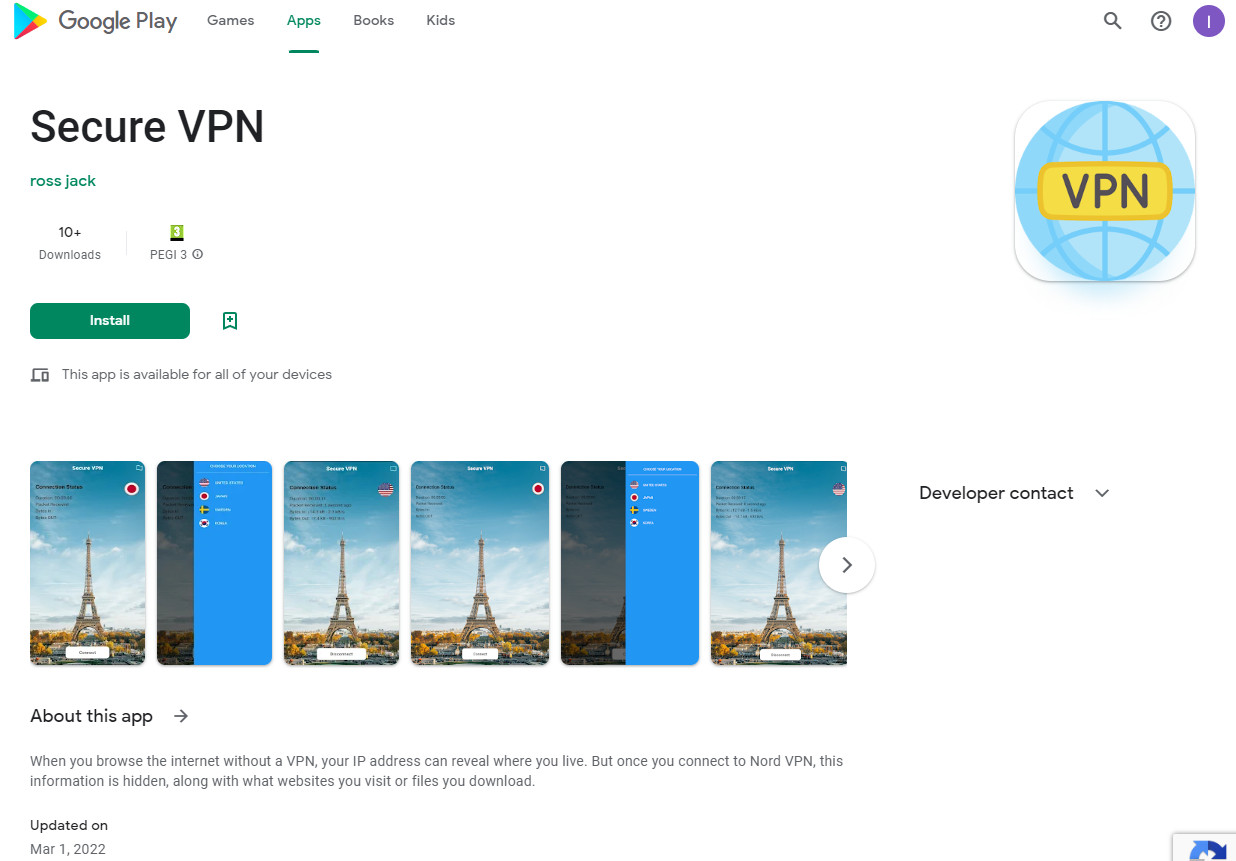 Fake Secure VPN app in Google Play used by SiderWinder APT in phishing campaign, source: BleepingComputer
Fake Secure VPN app in Google Play used by SiderWinder APT in phishing campaign, source: BleepingComputerThe researchers note that the description available for SideWinder’s fake Secure VPN app has been copied from the legitimate NordVPN app.
At runtime, the fake Secure VPN app makes a couple of requests to two domains likely owned by the attacker but these were unavailable during the investigation and a request to the root directory redirected to the legitimate NordVPN domain.
Unfortunately, the researchers could not confirm the purpose of the fake VPN app or whether it is malicious or not. However, SideWinder has used fake apps on Google Play in the past, as shown by past research from Trend Micro.
The list of actions previous fake apps from SideWinder were capable of include collecting and sending to the command and control server information like:
Location Battery status Files on device Installed app list Device information Sensor information Camera information Screenshot Account Wifi information Data of WeChat, Outlook, Twitter, Yahoo Mail, Facebook, Gmail, and Chrometheir apps are capable to collect a number of parameters on the targeted hosts and send the information back to their C2. Such parameters include: Location, Battery status, Files on device, Installed app list, Device information, Sensor information, Camera information, Screenshot, Account, Wifi information, Data of WeChat, Outlook, Twitter, Yahoo Mail, Facebook, Gmail, and Chrome.
Group-IB also found that the adversary used a custom tool that’s been recently added to their arsenal, tracked internally by Group-IB as SideWinder.AntiBot.Script.
“The script checks the client browser environment and, based on several parameters, decides whether to issue a malicious file or redirect to a legitimate resource” - Group-IB
If the script detects a visitor from an IP in Pakistan, it redirects to a malicious location. The following parameters are checked to determine if a visitor is a potential target or not:
Geographic position Version of the operating system Data about the user agent System language settingsIt can also determine the number of logical processors on the system and the video card used by the host, as well as access the credentials container in the web browser, which can return saved passwords.
Checking the video card is likely to determine if the host is used for malware analysis purposes, as it is compared to the device’s screen size.
Another function in the script, the most significant one, is used to serve a malicious file and to redirect a non-interest target to a legitimate resource.
Based on its findings, Group-IB assesses that SideWinder’s infrastructure is widely spread to deploy new command and control servers to support phishing activity.
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·