BOOK THIS SPACE FOR AD
ARTICLE ADSUMMARY
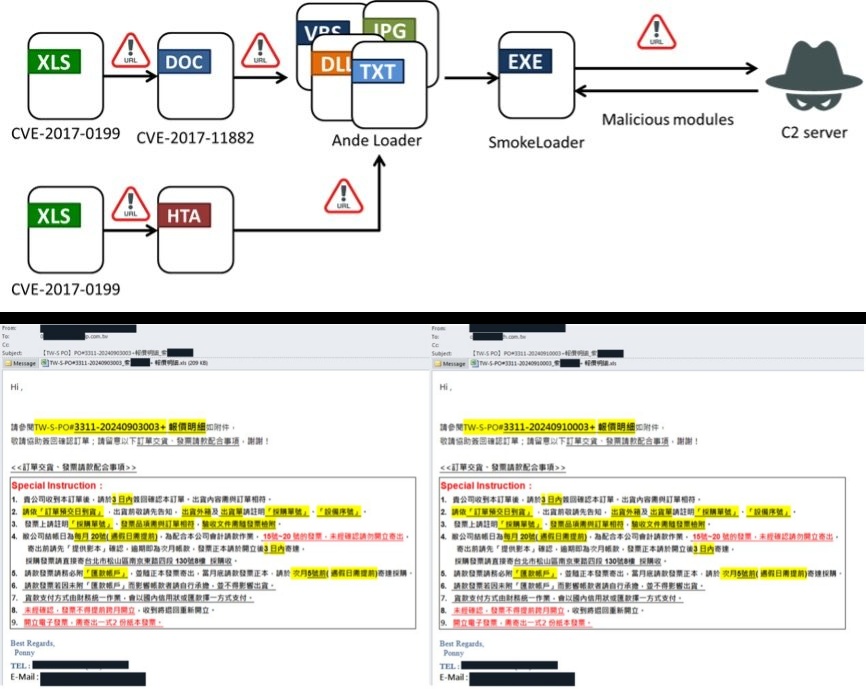
Targeted Campaign: SmokeLoader malware attacks Taiwanese industries, including manufacturing, healthcare, and IT. Phishing Emails: The campaign uses phishing emails exploiting MS Office vulnerabilities (CVE-2017-0199, CVE-2017-11882). Credential Theft: Plugins target browsers, email clients, and FTP software to steal credentials and sensitive data. Advanced Techniques: SmokeLoader employs evasion tactics like code obfuscation, anti-debugging, and sandbox evasion. Preventative Measures: FortiGuard Labs blocked the malware, offering antivirus signatures and IPS rules for protection.Cybersecurity researchers at Fortinet’s FortiGuard Labs have discovered a series of new malware attacks targeting companies in Taiwan. The attacks, which have been linked to the SmokeLoader malware, have impacted industries ranging from manufacturing and healthcare to IT and beyond.
SmokeLoader, known for its ability to deliver other malicious payloads, is taking a more direct role in this campaign, using its own plugins to execute attacks and steal sensitive data.
According to research by FortiGuard Labs, the attacks began with phishing emails containing malicious attachments, which were designed to exploit vulnerabilities in Microsoft Office. These included CVE-2017-0199, enabling malicious documents to automatically download and execute harmful payloads, and CVE-2017-11882, exploiting a vulnerability in Microsoft Office’s equation editor for remote code execution.
The emails, as per FortiGuard Labs’ blog post shared with Hackread.com heard of this publishing on Monday, written in native Taiwanese, were convincing but contained inconsistencies, such as different font and colour schemes, that suggested the text had been copied from elsewhere.
Once the malicious attachment was opened, the SmokeLoader malware was downloaded and executed, allowing it to communicate with its command and control (C2) server. From there, the malware downloaded various plugins, each designed to target specific applications and extract sensitive information.
The plugins used by SmokeLoader were found to target popular web browsers, email clients, and file transfer protocol (FTP) software, including Internet Explorer, Firefox, Chrome, Opera, Outlook, Thunderbird, and FileZilla. The malware was able to extract login credentials, auto-fill data, and even email addresses from these applications.
One of the plugins, known as Plugin 4, was designed to clear cookies from targeted browsers, forcing victims to re-enter their login credentials. Another plugin, Plugin 8, was used to inject keylogging code into explorer.exe, allowing the malware to capture keyboard inputs and clipboard content.
The SmokeLoader malware was also found to use advanced techniques to evade detection, including code obfuscation, anti-debugging, and sandbox evasion. Its modular design allows it to adapt to different attack scenarios, making it a formidable threat to organizations.
FortiGuard Labs has detected and blocked the malware, assigning it a severity level of “High.” The company has also provided protections for its customers, including antivirus signatures and IPS rules to detect and prevent malware.
In a comment to Hackread.com, Casey Ellis, Founder and Advisor at Bugcrowd, a San Francisco, Calif.-based leader in crowdsourced cybersecurity suggests the use of SmokeLoader aligns with a broader global pattern of cyber actors preparing for future attacks by infiltrating systems in advance.
“Given the geo-political environment, Taiwan is no stranger to thinking about Advanced Persistent Threats (APTs) and the use of SmokeLoader does seem to follow suit with the general trend of pre-positioning that we have seen in other parts of the world.“
What can you do to protect yourself?
To avoid falling victim to the SmokeLoader malware, it’s important to stay cautious with emails from unknown or suspicious sources. Don’t click on links or download attachments, especially if they prompt you to enable macros or run files.
If you’re unsure about an email, even from a familiar source, check its content carefully. Scan links, files, and attachments using tools like VirusTotal or your system’s security software to ensure they’re safe.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·