BOOK THIS SPACE FOR AD
ARTICLE AD
New findings have emerged that shed light on a critical SonicWall vulnerability disclosed last year, which was initially thought to have been patched.
In October last year, a critical stack-based Buffer Overflow vulnerability, tracked as CVE-2020-5135, was discovered affecting over 800,000 SonicWall VPNs.
When exploited, the vulnerability allows unauthenticated remote attackers to execute arbitrary code on the impacted devices, or cause Denial of Service (DoS).
Turns out, the vulnerability was not properly patched—until now.
As such a new vulnerability identifier, CVE-2021-20019 has been assigned to the flaw.
SonicWall bug in 800K VPN firewalls was only partially fixed
In October last year, BleepingComputer reported on a critical stack-based Buffer Overflow vulnerability in SonicWall VPN firewalls.
The vulnerability, tracked as CVE-2020-5135, was present in versions of SonicOS, ran by over 800,000 active SonicWall devices.
Craig Young of Tripwire Vulnerability and Exposure Research Team (VERT), and Nikita Abramov of Positive Technologies were initially credited with discovering and reporting the vulnerability.
But, now, Tripwire has reached out to BleepingComputer, claiming the previously made fix for the flaw was "unsuccessful."
The critical buffer overflow vulnerability lets an attacker send a malicious HTTP request to the firewall to cause a Denial of Service (DoS) or execute arbitrary code.
After a series of emails between Tripwire researcher Young and SonicWall, the vulnerability was eventually treated as a problem and patched.
But later on, the researcher retested his proof-of-concept (PoC) exploit against SonicWall instances and concluded that the fix was "botched."
"I decided to spin up a SonicWall instance on Azure to confirm how it responded to my proof-of-concept exploit."
"In the past, when researching network appliances, I have observed differences in vulnerable behavior between virtual and physical systems."
"In some past research, I have observed differences in vulnerable behavior related to hardware-based acceleration utilizing a separate code path," says Young in a blog post.
The Tripwire researcher was surprised to notice, however, that in this case, his PoC exploit didn't trigger a system crash—but a flood of binary data in the HTTP response instead:
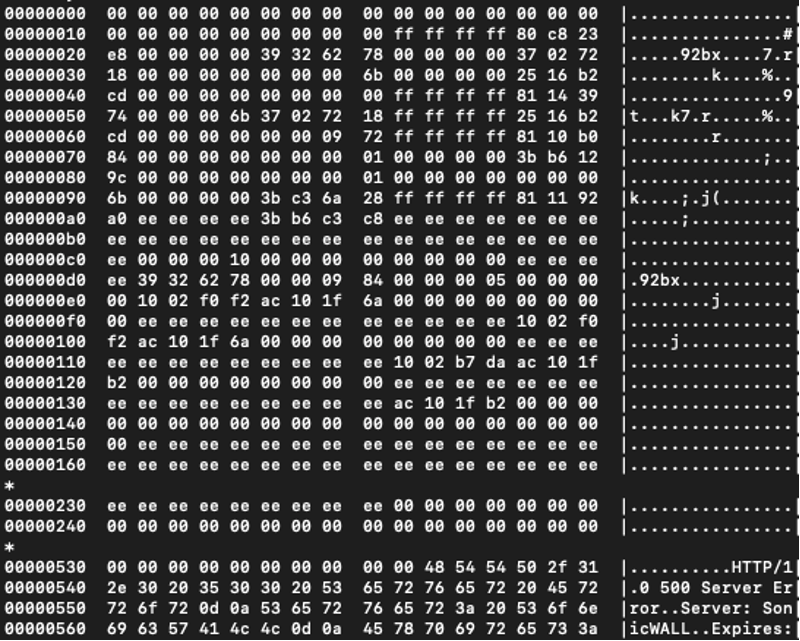 HTTP response returning the binary response (bottom right)
HTTP response returning the binary response (bottom right)Source: Tripwire
This is when Young reached out to SonicWall again for a remedy.
Young states that the binary data returned in the HTTP responses could be memory addresses.
"Although I never observed recognizable text in the leaked memory, I believe this output could vary based on how the target system is used."
"I also suspect that the values in my output are in fact memory addresses which could be a useful information leak for exploiting an RCE bug," said the researcher.
After reporting this to SonicWall on October 6th, 2020, the researcher sent a few more follow-ups; twice in March 2021.
Eventually, according to Young, SonicWall's PSIRT stated:
"This [vulnerability has] been assigned CVE-2021-20019 and a patch would be released in early April 2021," but the researcher was not aware of a patch having been published.
BleepingComputer reached out to SonicWall for a comment and we were told:
"SonicWall is active in collaborating with third-party researchers, security vendors and forensic analysis firms to ensure its products meet or exceed expected security standards."
"Through the course of this practice, SonicWall was made aware of, verified, tested and patched a non-critical buffer overflow vulnerability that impacted versions of SonicOS."
"SonicWall is not aware of this vulnerability being exploited in the wild. As always, SonicWall strongly encourages organizations maintain patch diligence for all security products," a SonicWall spokesperson told BleepingComputer.
SonicWall has now released advisories [1, 2] related to this vulnerability today, with further information on the fixed versions.
Although most versions have a patch available, platforms including NSsp 12K, SuperMassive 10k, and SuperMassive 9800 are awaiting a patch release.
As such, SonicWall customers are advised to monitor the advisory pages for updates.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·