BOOK THIS SPACE FOR AD
ARTICLE ADResearchers say that the campaign sidesteps end user detection and security solutions.
Spammers have started using a tricky URL obfuscation technique that sidesteps detection – and ultimately infects victims with the LokiBot trojan.
The tactic was uncovered in recent spear-phishing emails with PowerPoint attachments, which contain a malicious macro. When the PowerPoint file is opened, the document attempts to access a URL via a Windows binary (mshta.exe), and this leads to various malware being installed onto the system.
This process is not unusual for macro downloaders. However, because the domains associated with the campaign are already known to host malicious files and data, the attackers used a unique semantic attack on the campaign’s URLs to trick the email recipient and avoid being flagged by email and AV scanners. A semantic URL attack is when a client manually adjusts the parameters of its request by maintaining the URL’s syntax – but altering its semantic meaning. More on that, below.
“We found it interesting that the attackers were using URIs in this way, which essentially is an attack on the user’s preconceived notion of what a URI should look like,” said researchers with Trustwave in a Thursday report. “It may also defeat security solutions, which may be expecting URIs in a certain format.”
The malicious email that was observed by researchers is titled: “URGENT: REQUEST FOR OFFER (University of Auckland)” and the attached PowerPoint is titled “Request For Offer.” The University of Auckland is a public research university in Auckland, New Zealand. Threatpost has reached out to Trustwave for further details on the targeting and lure of this attack.
Obfuscation Tactic
It’s important to distinguish between a URL versus URI here. A URI is an identifier of a specific resource, such as a page, book or a document. A URL, meanwhile, is the most common type of URI that also tells users how to access it (such as HTTPs or FTP).
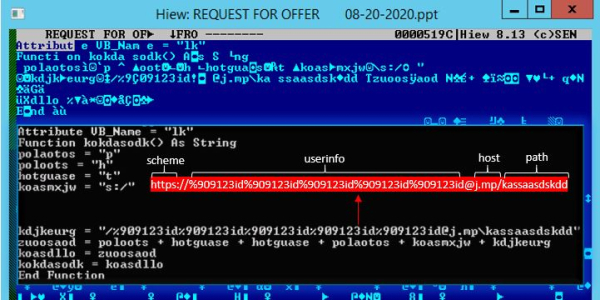
A URI is made up of a scheme, host and path. The scheme identifies the protocol to be used to access the resource on the internet, while the host identifies the host that holds the resource, and the path identifies the specific resource in the host that the web client wants to access.
The spammers behind this attack have horned in on one component of the URI scheme called an Authority component, which holds an optional user-information part. If the “userinfo” subcomponent is present, it is preceded by two slashes and followed by an “@” character. An example of this Authority structure is as follows: authority = [userinfo@]host[:port].
Because “userinfo” is not commonly used, it is sometimes ignored by servers, researchers said. In this specific campaign, attackers took advantage of this fact, utilizing what researchers called a “dummy” userinfo in order to hide their true intent.
The end result is that at face value, end users who click on the link may believe they are being led to one domain, but the URL is actually for another.
In this specific campaign, the URL used (j[.]mp/kassaasdskdd) actually utilizes a URL shortening service offered by Bit.ly and leads to Pastebin, which is a website that allows users to share plain text through public posts called “pastes.” Both the use of URL shortening services and Pastebin are commonly leveraged by cybercriminals; so to avoid being characterized as a short URL and to evade detection signatures, the attackers repeatedly use a randomized, short string (“%909123id”) in the userinfo portion of their URL (see picture below).
Because userinfo is not required to gain access to any resources, the userinfo data will be ignored when the URL is accessed – meaning that at face value, it’s unclear that the URL is shortened, and will redirect the users to Pastebin despite security gates.
“The bad guys are attempting to make the domains unnoticeable yet still conforming with the generic URI syntax,” said researchers.
The PowerPoint attachment and its macro code where the initial malicious URL is formulated. Credit: Trustwave
Researchers conducted a deeper analysis of four URLs associated in the campaign. The first URL, accessed by the PowerPoint attachment, redirects to an obfuscated VBScript hosted on Pastebin. A second URL contains VBScript, which is a dropper that writes a PowerShell downloader into the registry and sets up persistence, said researchers. This PowerShell then downloads and processes the raw data on two more Pastebin URLs, and then executes the output binaries, they said.
The content at the third URL meanwhile contains an obfuscated PowerShell code, which then executes two DotNet compiled Dynamic Link Libraries (DLLs). These DLLs bypass the Windows Anti-Malware Scan Interface (AMSI) on the machine, which is an interface standard allowing user applications and services to integrate with any anti-malware product on a machine.
They then load a DLL injector into the memory. Finally, the last URL contains an obfuscated malware LokiBot sample, which is injected into a legitimate process (notedpad.exe) by the aforementioned DLL injector.
LokiBot Malware
LokiBot is a prolific trojan that’s infamous for being simple and effective with its capabilities to covertly steal information from compromised endpoints. It’s currently being distributed in various forms that can hitch a ride inside other file formats—as is the case in the current campaign. Various versions of LokiBot also in the past were sold on underground markets for as little as $300.
The new tactic comes just a week after The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned that LokiBot is seeing a surge across the enterprise landscape. The uptick started in July, according to the agency, and activity has remained “persistent” ever since.
“LokiBot has stolen credentials from multiple applications and data sources, including Windows operating system credentials, email clients, File Transfer Protocol and Secure File Transfer Protocol clients,” according to the alert, issued Tuesday. “LokiBot has [also] demonstrated the ability to steal credentials from…Safari and Chromium and Mozilla Firefox-based web browsers.”
On October 14 at 2 PM ET get the latest information on the rising threats to retail e-commerce security and how to stop them. Register today for this FREE Threatpost webinar, “Retail Security: Magecart and the Rise of e-Commerce Threats.” Magecart and other threat actors are riding the rising wave of online retail usage and racking up big numbers of consumer victims. Find out how websites can avoid becoming the next compromise as we go into the holiday season. Join us Wednesday, Oct. 14, 2-3 PM ET for this LIVE webinar.
.png)

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·