BOOK THIS SPACE FOR AD
ARTICLE AD
What is css injection ?
CSS injection vulnerabilities arise when an application imports a style sheet from a user-supplied URL, or embeds user input in CSS blocks without adequate escaping. They are closely related to cross-site scripting (XSS) vulnerabilities but often trickier to exploit.
Testing

XSS : Not worked :(.
Test CSS File: Good CSS File injected :).

Other vulnerability CLICKJACKING to help us complete the CSS injection
Our attack method will allow the victim to enter an address and pull data from that page with css injection.
We need it for this
fakeurl (I used ngrok )PHP scriptSending the address to the victim
Step #1
Create index.php

The index file will establish the link between the victim and the site.
Create a.php

In this file we will call the target site in iframe.
Create css.php

css.php file is one of our most important files.Here, css codes to be injected into the page are produced.The generated codes are reproduced per character.
Req 1: abcdef123456789 -> founded aReq 2 : a(abcdef123456789) -> founded 9Req 3 : a9(abcdef123456789)In this way, the cycle continues until we get full data.
As in the scripting languages, CSS has REGEX.
For example : input[name^=email_protected_]
Since the e-mail address is protected here, the input name changes constantly, and we will ask that it complete the rest based on the remaining part.
Create opt.php
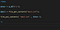
opt.php writes incoming requests to the file.Thus, the next request is generated by reading from the written file.
Get Full Payload : https://dotphp.net/cssinj/site.php?css=https://dotphp.net/cssinj/css.php
Test Injection.


And the last step is to send an address to the victim. : https://dotphp.net/inj.php ( index.php )
Youtube video URL : https://www.youtube.com/embed/qkHf9XExyBU
Inline CSS Injection Leak Data : https://medium.com/bugbountywriteup/exfiltration-via-css-injection-4e999f63097d
Twitter: https://twitter.com/Tismayil1
Happy Hunting. :)
.png)
 4 years ago
207
4 years ago
207 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·