BOOK THIS SPACE FOR AD
ARTICLE AD
Two suspects were arrested in Miami this week and charged with conspiracy to steal and launder over $230 million in cryptocurrency using crypto exchanges and mixing services.
The two defendants, 20-year-old Malone Lam (aka "Greavys," "Anne Hathaway," and "$$$") and 21-year-old Jeandiel Serrano (aka "Box," "VersaceGod," and "@SkidStar") were arrested Wednesday night by FBI agents and appeared in court on Thursday.
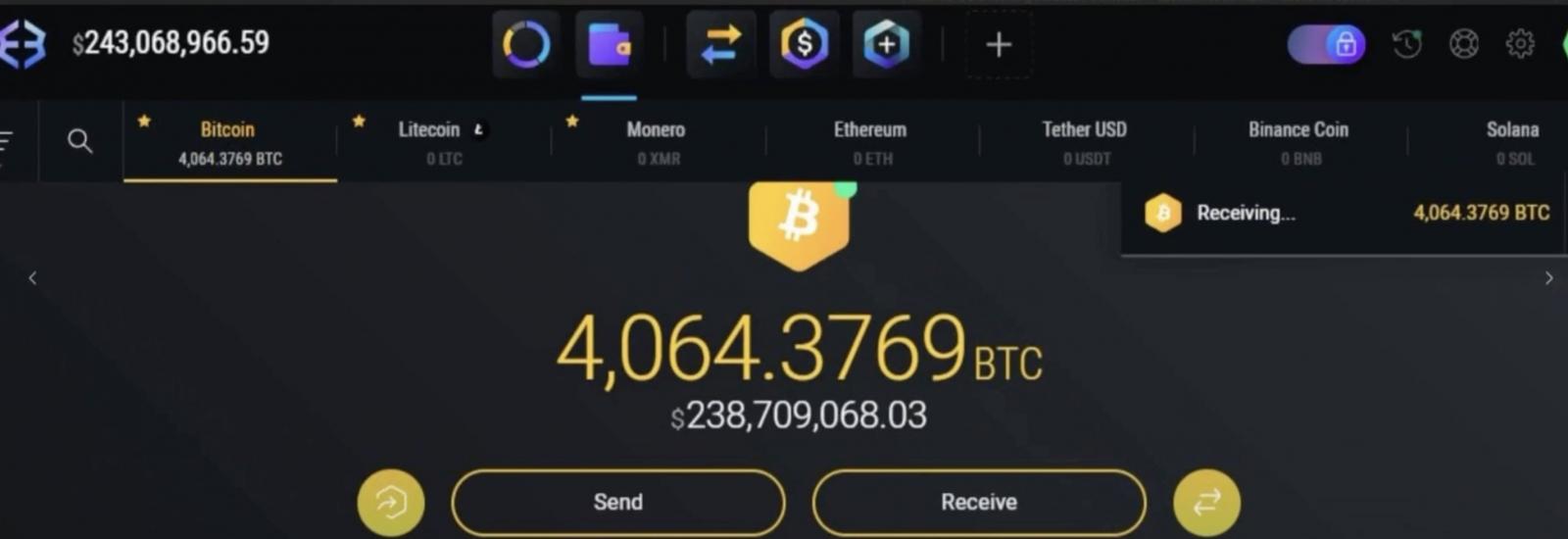
During a successful attack on August 18, they stole more than 4,100 Bitcoin from a Washington, D.C., victim (worth more than $230 million at the time).
According to court documents, Lam, Serrano, and others allegedly gained unauthorized access to victims' cryptocurrency accounts, transferring funds into crypto wallets under their control before laundering the stolen assets.
They reportedly laundered the stolen cryptocurrency via a combination of crypto mixers and exchanges, using "peel chains" and pass-through wallets, and virtual private networks (VPNs) to hide their identities and locations throughout the scheme.
The stolen cryptocurrency was then used to finance lavish lifestyles, with the defendants allegedly spending on international travel, luxury cars, high-end watches, designer handbags, and nightclub outings in Los Angeles and Miami.
 Stolen crypto being transferred (ZachXBT)
Stolen crypto being transferred (ZachXBT)Exposed after OPSEC blunders, spending spree
Crypto fraud investigator ZachXBT, who assisted the official investigators, identified a third alleged conspirator known by the alias "Wiz." As he revealed, the group targeted a creditor of cryptocurrency exchange Genesis, using spoofed phone numbers and impersonating Google and Gemini customer support to compromise accounts.
While posing as a Gemini support representative, they claimed the account had been compromised and deceived the victim into resetting two-factor authentication (2FA) and sharing their screen via the AnyDesk remote desktop application to access private keys from Bitcoin Core and steal funds.
"An initial tracing showed $243M split multiple ways between each party before funds quickly peeled off to 15+ exchanges immediately swapping back and forth between Bitcoin, Litecoin, Ethereum, and Monero," ZachXBT said.
The follow-up investigation found that a cluster of Ethereum addresses linked to Serrano and Wiz received over $41 million from two exchanges in recent weeks. Despite efforts to cover their tracks, investigators traced the laundered funds after they were used to buy luxury cars, watches, and jewelry.
The funds were quickly laundered through multiple cryptocurrency exchanges, with transactions bouncing between Bitcoin, Litecoin, Ethereum, and the privacy-focused coin Monero.
ZachXBT revealed that Wiz was caught after exposing his real name during a screen-sharing session, as shown by a recording he shared (embedded below).
3/ Here is a private video recording showing the live reaction by multiple of the threat actors to receiving $238M.
Theft txn hash
4064 BTC - Aug 19 at 4:05 am UTC
4b277ba298830ea538086114803b9487558bb093b5083e383e94db687fbe9090 pic.twitter.com/djSxBTkOF8
Additionally, while most funds were converted to Monero for added anonymity, Wiz and Serrano reportedly made critical errors, linking their laundered funds to the original stolen amounts.
The FBI arrested Lam and Serrano after tracking their lavish spending and social media posts from friends revealed their locations in Los Angeles and Miami.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·