BOOK THIS SPACE FOR AD
ARTICLE AD
Security researchers hacked Tesla's Wall Connector electric vehicle charger twice on the second day of the Pwn2Own Automotive 2025 hacking contest.
They also exploited 23 more zero-day vulnerabilities in WOLFBOX, ChargePoint Home Flex, Autel MaxiCharger, Phoenix Contact CHARX, and EMPORIA EV chargers, as well as in the Alpine iLX-507, Kenwood DMX958XR, Sony XAV-AX8500 In-Vehicle Infotainment (IVI) systems.
PHP Hooligans were the first to crash the Tesla Wall Connector after using a Numeric Range Comparison Without Minimum Check zero-day bug to take over the device. They were followed by Synacktiv, who also hacked Tesla's EV charger via the Charging Connector, an approach that's never been demonstrated publicly before.
Today, two bug collisions occurred during Tesla Wall Connector hacking attempts: one by team PCAutomotive and the other by the Summoning Team's Sina Kheirkhah, who used an exploit chain of two already-known bugs.
According to the Pwn2Own Tokyo 2025 contest rules, all devices targeted during the competition must have all security updates installed and run the latest operating system versions.
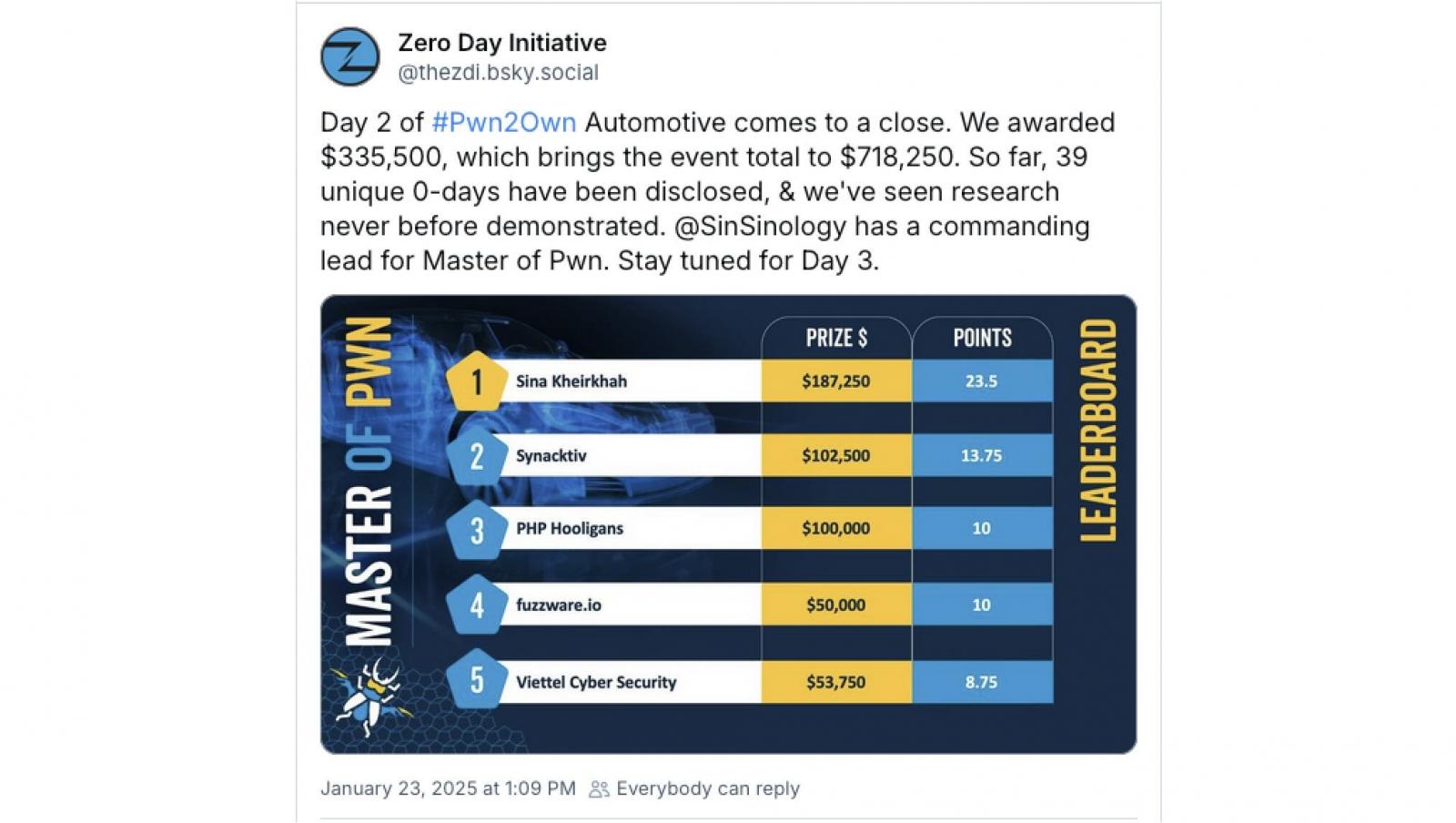
Trend Micro's Zero Day Initiative awarded $335,500 in cash rewards during the second day for 23 zero-day vulnerabilities. Sina Kheirkhah is currently in the lead for Master of Pwn.
On the first day of Pwn2Own Automotive, security researchers exploited 16 unique zero-day vulnerabilities and collected $382,750 in cash awards. After the competition ends, vendors will have 90 days to develop and release security fixes before ZDI publicly discloses the zero-day bugs.
The Pwn2Own Automotive 2025 hacking contest will focus on automotive technologies from January 22 to January 24 during the Automotive World conference in Tokyo, Japan.
Hackers will target car operating systems (i.e., Automotive Grade Linux, Android Automotive OS, and BlackBerry QNX), electric vehicle (EV) chargers, and in-vehicle infotainment (IVI) systems.
Even though Tesla also provided a Model 3/Y (Ryzen-based) equivalent benchtop unit, no security researcher had registered an attempt against the company's wall connector before the competition's schedule was published. The schedule for the second day and the results for each challenge can also be found here.
One year ago, during the first edition of Pwn2Own Automotive in Tokyo, security researchers were awarded $1,323,750 for hacking a Tesla twice and exploiting 49 zero-day bugs in multiple electric car systems.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·