BOOK THIS SPACE FOR AD
ARTICLE AD
Google is in the process of developing a password strength indicator for its Chrome browser. While it is true that such functionality is available today by way of a browser plug-in, the fact that Google is dedicating resources to developing a browser native password strength tool is a clear indicator of Google’s priorities.
By adding this feature, Google is decisively acknowledging the critical role that password strength plays in keeping its users secure.
So why the sudden emphasis on password strength? It likely has to do with the fact that cybercriminals have more resources at their disposal than ever before, thanks to modern CPUs and the scalability that can be achieved through cloud computing.
As such, many passwords that were once considered to be secure can now be brute force cracked with relative ease. Longer and more complex passwords tend to be much more resistant to these attempts.
Hive Systems has created a chart outlining how long it would take a hacker to brute force crack various types of passwords.
This chart is periodically updated as technology changes so as to provide accurate estimates of the time required to crack a password.
According to the company’s 2022 chart, a twelve-digit numeric password can be cracked in approximately two seconds. However, a 12-character password consisting of numbers, upper- and lower-case letters would take an estimated 24 years to crack.
If symbols were also included then the estimated time required to brute force crack the password increases to 3000 years!
The lesson is that password length requirements alone are meaningless. After all, all of the previous examples were based on a twelve-character password. Password complexity is what made the difference between a password taking two seconds to crack or taking 3000 years to crack.
Of course, this is not to say that you can ignore password length completely.
According to the Hive Systems chart, a cyber criminal can crack a six-character password instantly no matter how complex that password may be. In case you are wondering, a determined (and patient) cybercriminal can crack a complex, ten-character password in a semi-reasonable amount of time - five months.
However, eleven characters seems to be the current tipping point, as a complex eleven-character password will take about 34 years to crack.
If you really want to keep your organization secure, you need to require users to use passwords that are both long and complex. The problem is however, that end users often have an aversion to using highly secure passwords.
Most users would probably prefer a password that is shorter and easier to remember, especially if they’re not relying on the power of a password manager.
In spite of end users’ hesitancies, the forthcoming Google password strength tool may ultimately improve your organization’s cyber security, even if you do not use Chrome.
There are at least two ways in which this could conceivably happen.
End-user coachingFirst, when the new password strength tool becomes available, Chrome will actively coach users on using secure passwords. Over time, Chrome users will likely become accustomed to using stronger passwords and that behavior may find its way into your organization. Password reuse
The second way in which Google may indirectly improve your organization’s security is through something that nobody likes to talk about—password reuse. Many of your users probably use their work password on various consumer Websites so that they do not have to remember so many passwords.
Password reuse poses obvious security concerns. However, if Chrome coaxes users into adopting stronger passwords then those passwords will become more difficult to crack, thereby lessening some of the risks associated with password reuse.
The good news is that there is an easy way of starting users down the road to using strong passwords even before the new version of Chrome is released.
Like Chrome’s planned improvements, Specops Password Policy already provides dynamic feedback any time that a user changes their work password.
This feedback helps users to choose stronger passwords and can help to reduce user frustration at the same time.
As a user enters a new password, the dynamic password feedback feature checks in real time to see whether or not the user’s chosen password aligns with the organization’s password policy. If the new password is not compliant with the policy then Specops Password Policy will tell the user where their password falls short and what they need to do t fix the problem.
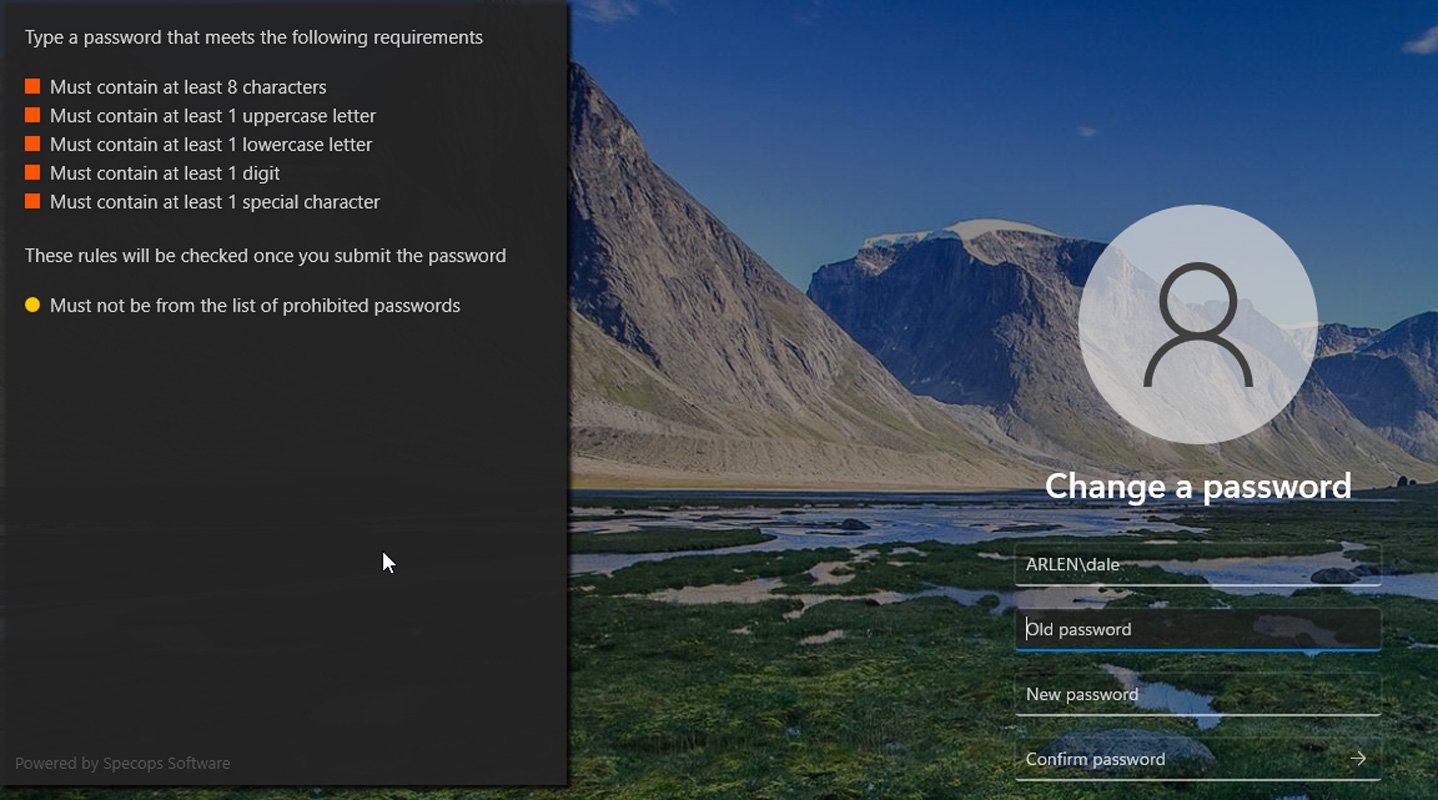 Specops Password Policy dynamic feedback as an end-user would see it
Specops Password Policy dynamic feedback as an end-user would see itThis prescriptive guidance will not only make the user’s lives easier, it may even reduce the number of password related helpdesk calls that your organization receives. You can test out Specops Password Policy in your Active Directory for free.
Sponsored by Specops
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·